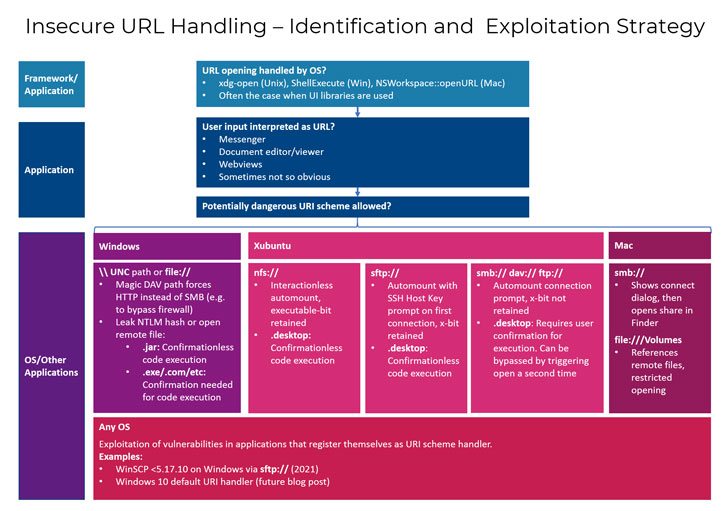
Multiple one-click vulnerabilities have been discovered across a
variety of popular software applications, allowing an attacker to
potentially execute arbitrary code on target systems.
The issues were discovered by Positive Security researchers
Fabian Bräunlein and Lukas Euler and affect apps like Telegram,
Nextcloud, VLC, LibreOffice, OpenOffice, Bitcoin/Dogecoin Wallets,
Wireshark, and Mumble.
“Desktop applications which pass user supplied URLs to be opened
by the operating system are frequently vulnerable to code execution
with user interaction,” the researchers said[1]. “Code execution can be
achieved either when a URL pointing to a malicious executable
(.desktop, .jar, .exe, …) hosted on an internet accessible file
share (nfs, webdav, smb, …) is opened, or an additional
vulnerability in the opened application’s URI handler is
exploited.”
Put differently; the flaws stem from an insufficient validation
of URL input that, when opened with the help of the underlying
operating system, leads to inadvertent execution of a malicious
file.
Positive Security’s analysis found that many apps failed to
validate the URLs, thereby allowing an adversary to craft a
specially-crafted link pointing to a piece of attack code,
resulting in remote code execution.
Following responsible disclosure, most of the apps have released
patches to remediate the flaws –
- Nextcloud[2]
– Fixed in version 3.1.3 of Desktop Client released on February 24
(CVE-2021-22879) - Telegram – Issue reported on January 11 and subsequently fixed
via a server-side change on (or slightly before) February 10 - VLC Player[3]
– Issue reported on January 18, with patched version 3.0.13 set for
release next week - OpenOffice – Fixed in the upcoming 4.1.10 release
(CVE-2021-30245) - LibreOffice[4]
– Addressed in Windows, but vulnerable in Xubuntu
(CVE-2021-25631) - Mumble[5]
– Fixed in version 1.3.4 released on February 10
(CVE-2021-27229) - Dogecoin[6]
– Fixed in version 1.14.3 released on February 28 - Bitcoin ABC[7]
– Fixed in version 0.22.15 released on March 9 - Bitcoin Cash[8]
– Fixed in version 23.0.0 (currently in release process) - Wireshark[9]
– Fixed in version 3.4.4 released on March 10 (CVE-2021-22191) - WinSCP[10] – Fixed in version
5.17.10 released on January 26 (CVE-2021-3331)
“This issue spans multiple layers in the targeted system’s
application stack, therefore making it easy for the maintainers of
any one to shift the blame and avoid taking on the burden of
implementing mitigation measures on their end,” the researchers
said.
“However, due to the diversity of client systems and their
configuration states, it is crucial that every party involved takes
on some amount of responsibility and adds their contribution in the
form of mitigation measures” such as URL validation and preventing
remote shares from being auto-mounted.
References
- ^
said
(positive.security) - ^
Nextcloud
(nextcloud.com) - ^
VLC
Player (www.videolan.org) - ^
LibreOffice
(github.com) - ^
Mumble
(github.com) - ^
Dogecoin
(github.com) - ^
Bitcoin
ABC (github.com) - ^
Bitcoin
Cash (gitlab.com) - ^
Wireshark
(gitlab.com) - ^
WinSCP
(winscp.net)