of Justice (DoJ) and sanctioned by the US Treasury for allegedly
laundering $100 million worth of virtual currency using prepaid
Apple iTunes gift cards.
According to a newly unsealed court
document[1], the illicit funds
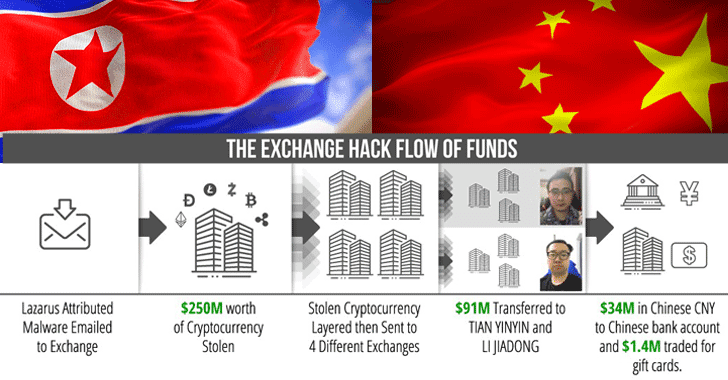
originated from a $250 million haul stolen from two different
unnamed cryptocurrency exchanges that were perpetrated by
Lazarus Group, a cybercrime group with ties with the North
Korean government.
The two individuals in question — Tian Yinyin
(田寅寅) and Li Jiadong (李家东) — were both charged with
operating an unlicensed money transmitting business and money
laundering conspiracy.
Prosecutors said the defendants worked on behalf of the threat
actors based in North Korea to allegedly launder over a $100
million worth of stolen cryptocurrency to obscure transactions,
adding the hacking of cryptocurrency exchanges posed a severe
threat to the security of the global financial system.
It’s worth noting that Lazarus Group was one among the three
hacking outfits to be sanctioned by the
US government last September for conducting a variety of
financially-motivated operations ranging from cyber-espionage to
data theft, so as to fund the country’s illicit weapon and missile
programs.
Per the US Treasury[3], the Lazarus Group stole
the funds in 2018 after an employee of a cryptocurrency exchange
unwittingly downloaded malware through an email, which gave the
threat actor access to private keys, virtual currency, and other
customer information.
“Lazarus Group cyber actors used the private keys to steal
virtual currencies (250 million dollar equivalent at date of theft)
from this exchange, accounting for nearly half of the DPRK’s
estimated virtual currency heists that year.” the Treasury
said.
While the name of the exchange remains unknown, a report by
Kaspersky[4] back in August 2018
detailed a campaign[5] that involved dropping
malware in the corporate networks of a number of crypto-exchanges
by sending spear-phishing emails.
Stating that North Korea trains hackers to “target and launder
stolen funds from financial institutions,” the Treasury added that
both Tian and Li received $91 million from North Korea-controlled
accounts that can be traced back to the 2018 cryptocurrency
exchange hack and an additional $9.5 million from a hack of a
second exchange.
Prosecutors said the two individuals helped convert more than $34
million of the illicit funds they received back into Chinese yuan
by moving them to a bank account linked to the exchange account, in
addition to converting $1.4 million worth of cryptocurrency into
Apple gift cards.
Created in 2007, the Lazarus Group has gone after a number of
targets, including militaries, governments, financial institutions,
media companies, and utility sectors, to perpetrate monetary heists
and destructive malware attacks, making it the most-profitable
cryptocurrency-hacker syndicate in the world.
A United Nations
report[6] last August estimated
North Korea to have generated an estimated $2 billion for its
weapons programs through “widespread and increasingly sophisticated
cyberattacks” targeting banks and cryptocurrency exchanges.
References
- ^
court document
(www.justice.gov) - ^
sanctioned by the US government
(thehackernews.com) - ^
US Treasury
(home.treasury.gov) - ^
report by Kaspersky
(www.kaspersky.com) - ^
campaign
(securelist.com) - ^
United Nations report
(www.reuters.com)
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/i9KSMKnensE/cryptocurrency-lazarus-hackers.html