security updates, Microsoft late yesterday separately issued an
advisory
warning billions of its Windows users of a new critical, unpatched,
and wormable vulnerability affecting Server Message Block
3.0 (SMBv3) network communication protocol.
It appears Microsoft originally planned to fix the flaw as part
of its March 2020 Patch Tuesday update only, but, for some reason,
it pulled the plug at the last minute, which apparently did not
stop a tech company from accidentally leaking the existence of the
unpatched flaw.
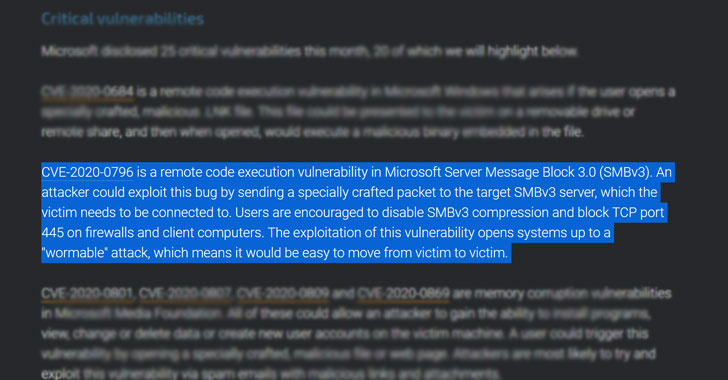
The yet-to-be patched flaw (tracked as CVE-2020-0796), if
exploited successfully, could allow an attacker to execute arbitrary
code[3] on the target SMB Server
or SMB Client.
The belated acknowledgment from Microsoft led some researchers
to call the bug “SMBGhost.”
[4]
“To exploit the vulnerability against an SMB Server, an
unauthenticated attacker could send a specially crafted packet to a
targeted SMBv3 Server,” Microsoft disclosed in an advisory. “To
exploit the vulnerability against an SMB Client, an unauthenticated
attacker would need to configure a malicious SMBv3 Server and
convince a user to connect to it.”
Server Message Block protocol provides the basis for file
sharing, network browsing, printing services, and interprocess
communication over a network.
vulnerable systems to a “wormable” attack, making it easy to
propagate from one victim to the other.
Although it’s unclear when Microsoft plans to patch the flaw,
the company is urging users to disable SMBv3 compression and block
TCP port 445 on firewalls and client computers as a workaround.
Set-ItemProperty -Path
“HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters”
DisableCompression -Type DWORD -Value 1 -Force
Furthermore, Microsoft has cautioned that disabling SMBv3
compression will not prevent the exploitation of SMB
clients.
It’s worth pointing out that the flaw impacts only Windows 10
version 1903, Windows 10 version 1909, Windows Server version 1903,
and Windows Server version 1909. But it’s possible more versions
are affected as SMB 3.0 was introduced with Windows 8 and Windows
Server 2012.
Despite the severity of the SMB bug, there’s no evidence that
it’s being exploited in the wild. But it’s also necessary to draw
attention to the fact that this is far from the only time SMB has
been exploited as an attack vector for intrusion attempts.
In the past few alone, some of the major ransomware infections,
including WannaCry[5] and NotPetya[6], have been the
consequence of SMB-based exploits.
For now, until Microsoft releases a security update designed to
patch the CVE-2020-0796 RCE flaw, it’s recommended that the system
administrators implement the workarounds to block attacks
attempting to exploit the vulnerability.
References
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/FT9f_WS07qs/smbv3-wormable-vulnerability.html