Indian IT firm that has secretly been operating as a global
hackers-for-hire service or hacking-as-a-service platform.
Based in Delhi, BellTroX InfoTech allegedly targeted
thousands of high-profile individuals and hundreds of organizations
across six continents in the last seven years.
Hack-for-hire services do not operate as a state-sponsored group
but likely as a hack-for-hire company that conducts commercial
cyberespionage against given targets on behalf of private
investigators and their clients.
According to the latest report published by the University of
Toronto’s Citizen Lab, BellTroX—dubbed ‘Dark Basin‘ as
a hacking group—targeted advocacy groups, senior politicians,
government officials, CEOs, journalists, and human rights
defenders.
[1]
“Over the course of our multi-year investigation, we found that
Dark Basin likely conducted commercial espionage on behalf of their
clients against opponents involved in high profile public events,
criminal cases, financial transactions, news stories, and
advocacy,” the report reads.
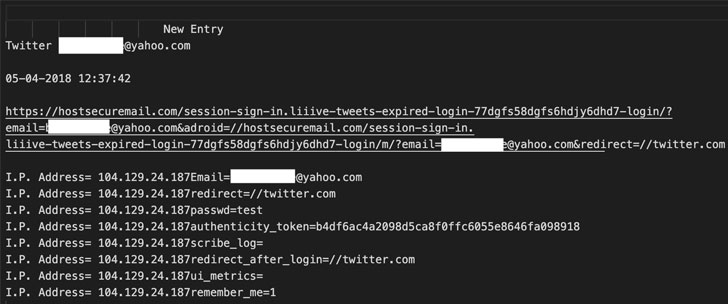
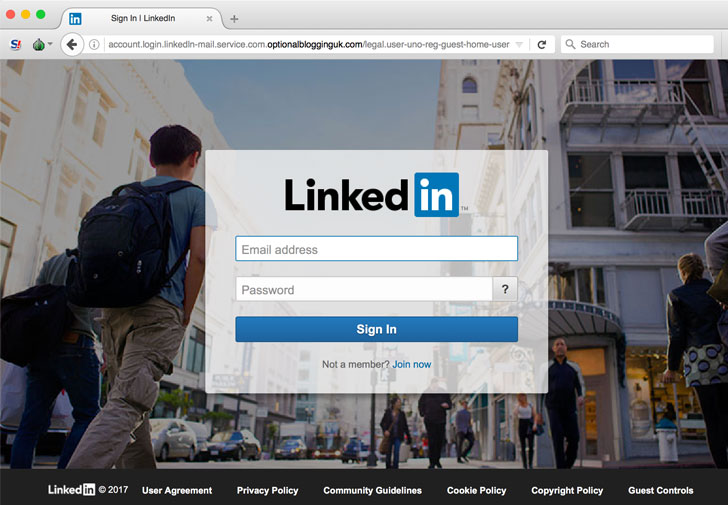
Citizen Lab started its investigation into the ‘Dark Basin’
group in 2017 after it was contacted by a journalist targeted with
phishing pages that were served via the self-hosted open-source
Phurl URL shortener.
disguise at least 27,591 other phishing links containing the
targets’ email addresses.
“Because the shorteners created URLs with sequential shortcodes,
we were able to enumerate them and identify almost 28,000
additional URLs containing email addresses of targets.”
Initially suspected to be state-sponsored, the hacking group was
later identified as a hack-for-hire scheme, given the variety of
targets.
indicted in
California in 2015 for his role in a similar hack-for-hire
scheme, along with two private investigators who admitted to paying
him to hack the accounts of marketing executives.
“Dark Basin left copies of their phishing kit source code
available openly online, as well as log files” that “recorded every
interaction with the credential phishing website, including testing
activity carried out by Dark Basin operators,” Citizen Lab
said.
“We were able to identify several BellTroX employees whose
activities overlapped with Dark Basin because they used personal
documents, including a CV, as bait content when testing their URL
shorteners.”
“They also made social media posts describing and taking credit
for attack techniques containing screenshots of links to Dark Basin
infrastructure.”
Citizen Lab notified hundreds of individuals and institutions
targeted by BellTroX and shared their findings with the United
States Department of Justice (DOJ) on the request of several
targets.
“Dark Basin has a remarkable portfolio of targets, from senior
government officials and candidates in multiple countries to
financial services firms such as hedge funds and banks to
pharmaceutical companies.”
“Many of Dark Basin’s targets have a strong but unconfirmed
sense that the targeting is linked to a dispute or conflict with a
particular party whom they know.”
Cybersecurity company NortonLifeLock[3]
also conducting a parallel investigation into Dark Basin’s
operations, dubbed as “Mercenary.Amanda” and released a list of
Indicators of Compromise (IoC).
References
- ^
Dark Basin
(citizenlab.ca) - ^
indicted in California in 2015
(www.justice.gov) - ^
NortonLifeLock
(www.nortonlifelock.com)
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/c709SGVoDo4/hacker-for-hire-belltrox-india.html