enterprises invest in threat prevention; the more hackers adapt and
continue to penetrate enterprises.
To make things worse, detecting these penetrations still takes
too long with an average dwell time that exceeds 100 (!) days.
To keep the enterprise protected, IT needs to figure out a way
to break this endless cycle without purchasing complex security and
data analysis tools and hiring the right (skilled and expensive)
security professionals to operate them.
Enter MDR
An advanced security service, Managed Detection and Response (MDR),
provides 24/7 threat detection and response, leveraging AI and
machine learning to investigate, alert, and contain threats.
MDR is becoming popular and gaining traction. In fact, Gartner
forecasts that by 2024, 25% of organizations will be using MDR
services, up from less than 5% today. And by 2024, 40% of midsize
enterprises will use MDR as their only managed security service
(source: Gartner’s Market Guide for Managed Detection and Response
Services Published 15 July 2019 – ID G00367208).
MDR is the industry’s hope to break the cycle of adding more and
more threat prevention tools, as hackers continuously increase
their attack capabilities. Yet, to gain visibility into all network
traffic – critical for effective detection and response –
traditional MDR services require installing dedicated software and
hardware across an enterprise’s network.
This deployment model is expensive and complex, causing many
companies to put off implementing MDR services while leaving their
network at risk.
Houston, we have a triple problem
1 — Every enterprise is a target for hackers, regardless of
its size or type of business. According to Verizon’s 2019 Data
Breach Investigations Report (DBIR[1]), 43% of breaches
involved small business victims; 10% were breaches of the Financial
Industry, and 15% were breaches involving Healthcare organizations.
2 — On top of that, enterprises need always to
assume the worst, as Gartner[2] states clearly, “The
assumption must be that the organization will be compromised, that
the hacker’s ability to penetrate systems is never fully countered.
Continuous monitoring of systems and behavior is the only way to
reliably detect threats before it is too late.”
3 — As a result, enterprises must continuously stand
guard, presenting a huge challenge for IT in terms of resources and
in-house skills. Furthermore, according to the DBIR, “56% of
breaches took months or longer to discover,” which during this long
dwell time the malware distributes itself, spreads throughout the
enterprise, and when activated, the damage caused is
multiplied.
In short, if all enterprises are targets, and must always assume
they’re under attack, then IT needs to be watching 24/7. Hmmm, does
this sound impractical to anyone else?
Okay, we’ve had a problem – meet Cato MDR
Cato MDR is incorporated into Cato’s SASE[3] platform, overcoming the
complications of traditional MDR. Cato aims to break the endless
cycle of increasing threats and lurking hackers. How? By enabling
customers that use Cato Cloud[4], to offload the
resource-intensive and skill-dependent process of detecting
compromised endpoints, to its SOC team. The team has instant, clear
visibility to all traffic, and there’s no need for customers to
deploy any additional network probes or software agents.
Cato automatically collects, indexes, and stores the metadata of
every WAN and Internet traffic flow traversing the Cato Cloud. Data
aggregation and machine learning algorithms mine the full network
context of Cato’s huge data warehouse, detecting any malware
indicators across customer networks. Cato’s SOC team assesses the
traffic flaws and alerts customers on any active threats.
A sneak peek behind the scenes
Cato claims that its MDR service stands guard for customers, and
dwell time is reduced from months to just 1-2 days. We had to get a
closer look to understand, if and how this is possible. Here’s what
we found.
Cato’s MDR service delivers these key capabilities:
- Zero-footprint data collection: Cato can access all
relevant information for threat analysis since it already serves as
the customer’s network platform (remember, Cato MDR is integrated
into Cato’s SASE platform). This eliminates the need for any
further installations, and all that’s left for customers is to
subscribe to the service. - Automated threat hunting: Cato uses big data and machine
learning algorithms to mine the network for suspicious flows, which
are based on the many flow attributes available to Cato. These
include accurate client application identification, geolocation,
risk assessment of the destination based on IP, URL category, URL
name structure, frequency of access, and more. - Human verification: Cato’s SOC team inspects suspicious
flows on a daily basis, closing the investigation for benign
traffic. - Network-level threat containment: Cato alerts customers
in case of a verified threat, and based on a predefined policy,
will apply network-level threat containment by blocking the network
traffic. - Guided remediation: Cato provides the context of threats
for IT’s further reference and recommends the actions to be taken
for remediation.
Additional cool capabilities
Multi-dimensional approach:
Cato has full visibility into all network traffic. From each
network flow that passes through its MDR service, Cato extracts and
collects metadata on the following:
- Source – Cato distinguishes between human and non-human
traffic, client type, OS data, - and more.
- Destination – Cato sees the popularity, category, and
reputation. - Behavior – Cato knows the traffic patterns, such as
frequency and volume of data.
Cato then stores all this metadata in its big data repository.
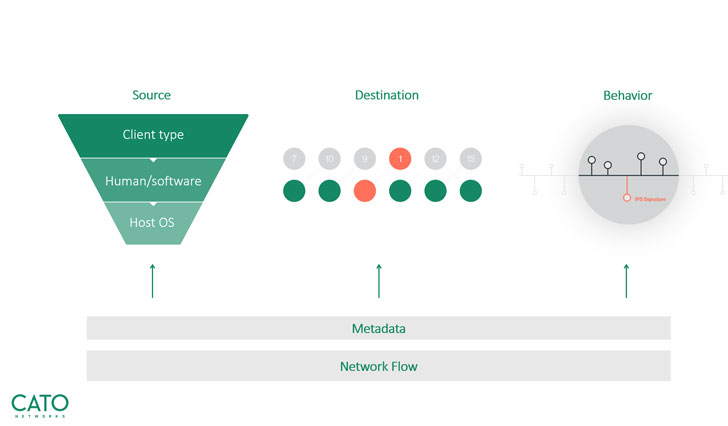 |
| Cato’s unique multi-dimensional approach |
Threat hunting:
We zoomed into Cato’s threat hunting technology and learned that
Cato reduces a daily quantity of millions of flows down to only
10-20 flows, which need actually to be investigated by its SOC
team. The team then reviews the list and makes sure customers are
only notified of confirmed threats that need attention. This
eliminates what we all dread – false positives.
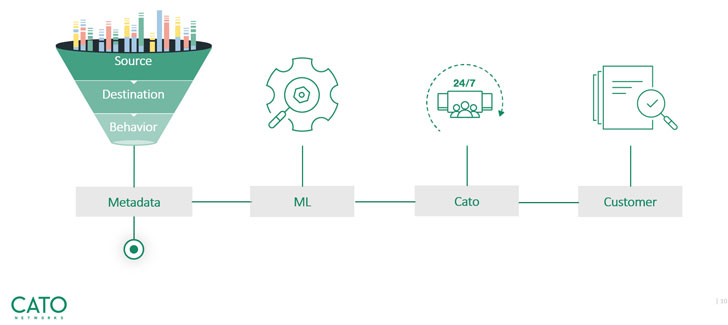 |
| Threat hunting – from millions of events to a meaningful, actionable item |
Service walkthrough
The Cato MDR portal is where customers handle all requests and
activities. The portal includes an online ticketing system, through
which all threats are reported, and their remediation status is
tracked. We found the portal to be intuitive and self-explanatory;
we’re happy to take you through a quick walkthrough:
Once you log into the portal, you’ll be able to view your
company’s activities’ detailed status.
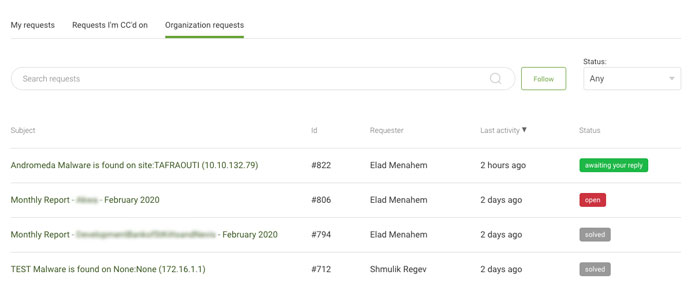 |
| View all company activities and requests |
For each request category, you can see a summary of all active
tickets that include: the ID number of a specific request, the name
of the requestor, the time of the last activity performed on the
request, and the status of the ticket.
Clicking on any of the requests enabled us to drill down into
its specifics. Each threat incident includes the following detailed
information:
- Name and IP of the site on which a threat was discovered.
- Type and name of threat.
- Risk level of a specific threat type.
- Internal/external IP address that is the target of an
attack. - Domain name that refers to a server’s IP address.
- Destination port number of a communication channel.
- Reference and link to Cato’s event discovery (Instant
Insight[5]). - Action taken by Cato’s SOC team.
- Further reference to a specific threat or attack.
- Recommended action for customers to take for removing a
threat.
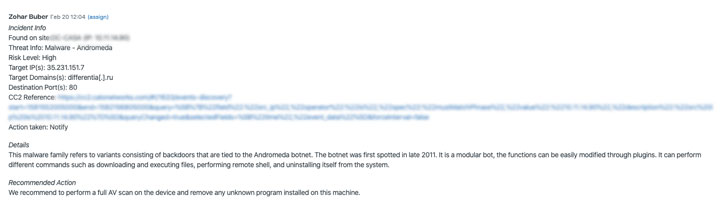 |
| Drill down into any request |
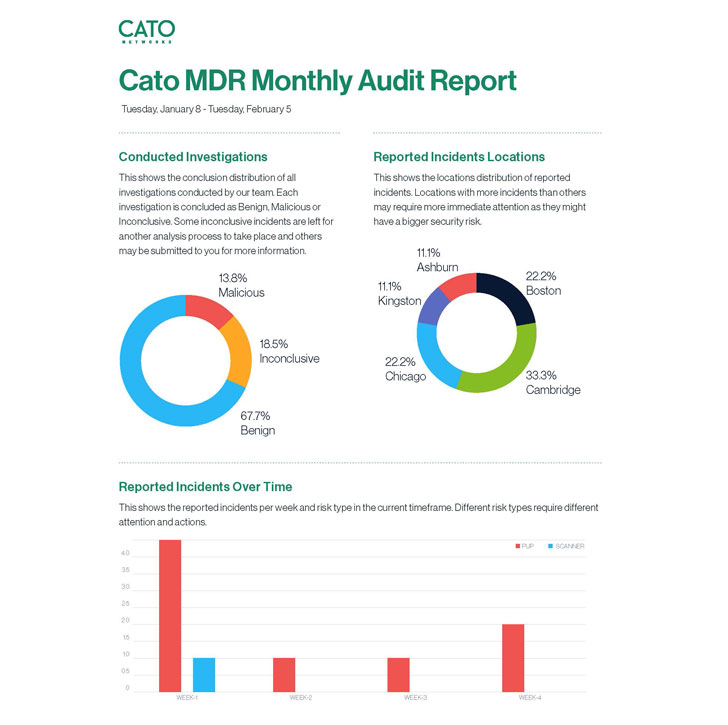
Cato MDR generates monthly reports that list all previous and
ongoing investigations and include an executive summary section,
which we found especially beneficial for easily sharing with
relevant peers and managers.
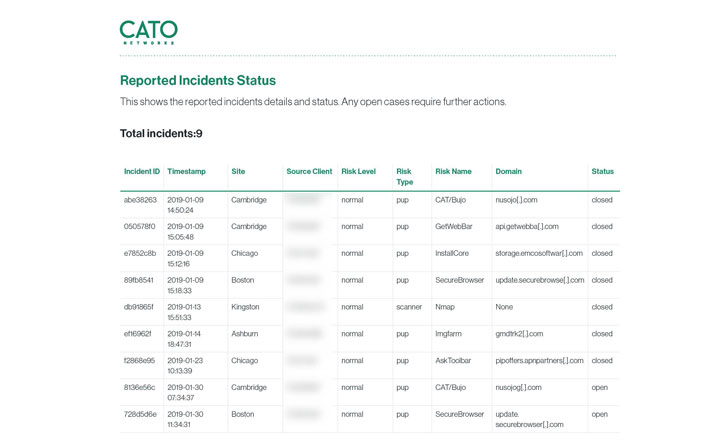 |
|
Monthly audit reports of all events |
Wrap-up
Cato MDR won us – and ) over with its sophisticated capabilities on
the one hand, and easy-to-use portal on the other. But mostly we
were impressed by the peace and quiet it provides enterprises and
their IT teams.
Customers – over with its sophisticated capabilities on the one
hand, and easy-to-use portal on the other. But mostly we were
impressed by the peace and quiet it provides enterprises and their
IT teams.
Cato supports Gartner’s four stages of an adaptive security
architecture[6]. Cato’s integrated
security stack addresses the Prediction and Prevention stages, and
Cato MDR concludes with the remaining stages of Detection and
Response.
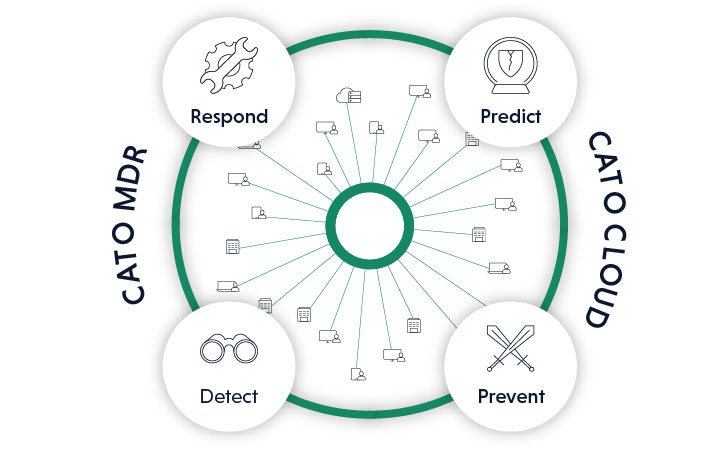 |
| Cato MDR adds Detection and Response to Prediction and Prevention already delivered by Cato Cloud |
Big LIKE Cato Networks!
References
- ^
DBIR
(enterprise.verizon.com) - ^
Gartner
(www.gartner.com) - ^
SASE
(www.catonetworks.com) - ^
Cato Cloud
(www.catonetworks.com) - ^
Instant Insight
(www.catonetworks.com) - ^
adaptive security architecture
(blogs.gartner.com)
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/phfQ-B-YZqI/cato-threat-detection-response.html