in the Android app developed by Chinese drone-maker Da Jiang
Innovations (DJI) that comes with an auto-update mechanism that
bypasses Google Play Store and could be used to install malicious
applications and transmit sensitive personal information to DJI’s
servers.
The twin reports, courtesy of cybersecurity firms Synacktiv[1]
and GRIMM[2], found that DJI’s Go
4[3] Android app not only
asks for extensive permissions and collects personal data (IMSI,
IMEI, the serial number of the SIM card), it makes of anti-debug
and encryption techniques to thwart security analysis.
“This mechanism is very similar to command and control servers
encountered with malware,” Synacktiv said.
“Given the wide permissions required by DJI GO 4 — contacts,
microphone, camera, location, storage, change network connectivity
— the DJI or Weibo Chinese servers have almost full control over
the user’s phone.”
The Android app has over one million installs via the Google Play
Store. But the security vulnerabilities identified in the app don’t
apply to its iOS version, which is not obfuscated, nor does it have
the hidden update feature.
A “Shady” Self-Update Mechanism
GRIMM said the research was undertaken in response to a security
audit requested by an unnamed defense and public safety technology
vendor that sought to “investigate the privacy implications of DJI
drones within the Android DJI GO 4 application.”
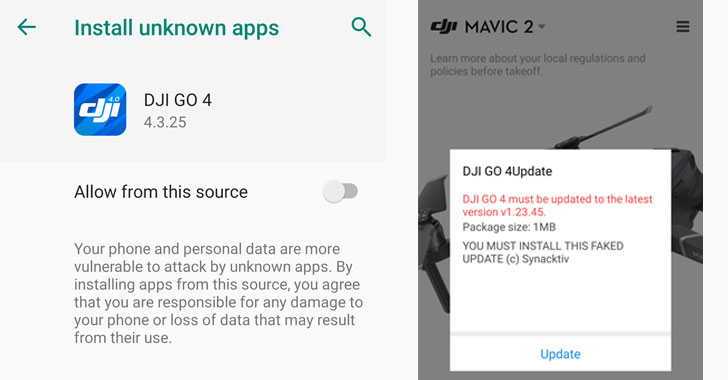
Reverse engineering the app, Synacktiv said it uncovered the
existence of a URL
(“hxxps://service-adhoc.dji.com/app/upgrade/public/check”) that it
uses to download an application update and prompt the user to grant
permission to “Install Unknown
Apps[4].”
“We modified this request to trigger a forced update to an
arbitrary application, which prompted the user first for allowing
the installation of untrusted applications, then blocking him from
using the application until the update was installed,” the
researchers said.
but the implications of this feature are also enormous. An attacker
could compromise the update server to target users with malicious
application updates.
Even more concerning, the app continues to run in the background
even after it’s closed and leverages a Weibo SDK
(“com.sina.weibo.sdk”) to install an arbitrarily downloaded app,
triggering the feature for users who have opted to live stream the
drone video feed via Weibo. GRIMM said it didn’t find any evidence
that it was exploited to target individuals with malicious
application installations.
Besides this, the researchers found that the app takes advantage
of MobTech SDK[5] to hoover metadata about
the phone, including screen size, brightness, WLAN address, MAC
address, BSSIDs, Bluetooth addresses, IMEI and IMSI numbers,
carrier name, SIM serial Number, SD card information, OS language
and kernel version, and location information.
DJI Pushes Back Against the Findings
Calling the findings “typical software concerns,” DJI disputed the
research, stating it contradicts “reports from the U.S. Department of
Homeland Security (DHS), Booz Allen
Hamilton and others that have found no evidence of unexpected
data transmission connections from DJI’s apps designed for
government and professional customers.”
“There is no evidence they were ever exploited, and they were not
used in DJI’s flight control systems for government and
professional customers,” the company said, adding it wasn’t able to
replicate the behavior of the app restarting on its own.
“In future versions, users will also be able to download the
official version from Google Play if it is available in their
country. If users do not consent to doing so, their unauthorized
(hacked) version of the app will be disabled for safety
reasons.”
DJI is the world’s largest maker of commercial drones and has
faced increased scrutiny alongside other Chinese companies over
national security concerns, leading the U.S. Department of the
Interior to ground its fleet of
DJI drones[9] earlier this
January.
Last May, the DHS had warned
companies[10] that their data may be
at risk if they use commercial drones manufactured in China and
that they “contain components that can compromise your data and
share your information on a server accessed beyond the company
itself.”
“This decision makes clear that the U.S. government’s concerns
about DJI drones, which make up a small portion of the DOI fleet,
have little to do with security and are instead part of a
politically-motivated agenda to reduce market competition and
support domestically produced drone technology, regardless of its
merits,” the company had said in a statement[11] back in January.
References
- ^
Synacktiv
(www.synacktiv.com) - ^
GRIMM
(blog.grimm-co.com) - ^
DJI’s Go 4
(www.dji.com) - ^
Install Unknown Apps
(support.google.com) - ^
MobTech
SDK (www.mob.com) - ^
DJI disputed the research
(www.dji.com) - ^
Department of Homeland
(www.auvsi.org) - ^
Booz Allen Hamilton
(www.precisionhawk.com) - ^
ground its fleet of DJI drones
(www.doi.gov) - ^
warned companies
(edition.cnn.com) - ^
statement
(www.dji.com)
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/H5zXjflhH_g/dji-drone-hacking_24.html