that exploits undocumented techniques to stay under the radar and
targets publicly accessible Docker servers hosted with popular
cloud platforms, including AWS, Azure, and Alibaba Cloud.
Docker is a popular platform-as-a-service (PaaS) solution for
Linux and Windows designed to make it easier for developers to
create, test, and run their applications in a loosely isolated
environment called a container.
According to the latest research Intezer shared with The Hacker News, an ongoing
Ngrok mining botnet campaign scanning the Internet for
misconfigured Docker API endpoints and has already infected many
vulnerable servers with new malware.
[2]
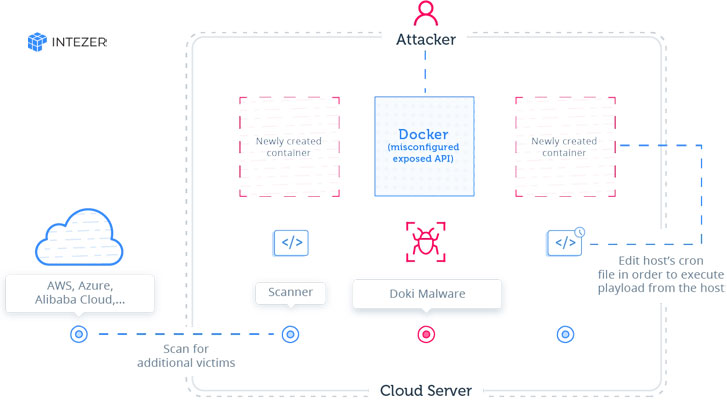
While the Ngrok mining botnet is active for the past two years, the
new campaign is primarily focused on taking control over
misconfigured Docker servers and exploiting them to set up
malicious containers with cryptominers running on the victims’
infrastructure.
Dubbed ‘Doki,’ the new multi-threaded malware leverages
“an undocumented method to contact its operator by abusing the
Dogecoin cryptocurrency blockchain in a unique way in order to
dynamically generate its C2 domain address despite samples being
publicly available in VirusTotal.”
- has been designed to execute commands received from its
operators, - uses a Dogecoin cryptocurrency block explorer to generate its
C2 domain in real-time dynamically, - uses the embedTLS library for cryptographic functions and
network communication, - crafts unique URLs with a short lifetime and uses them to
download payloads during the attack.
“The malware utilizes the DynDNS service and a unique Domain
Generation Algorithm (DGA) based on the Dogecoin cryptocurrency
blockchain in order to find the domain of its C2 in real time.”
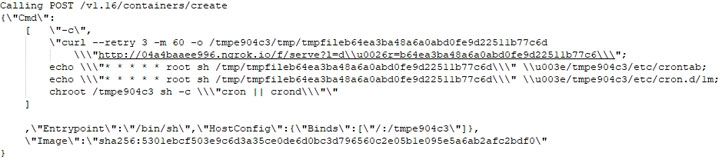
Besides this, the attackers behind this new campaign have also
managed to compromise the host machines by binding newly created
containers with the server’s root directory, allowing them to
access or modify any file on the system.
utility of the host. The attacker modifies the host’s cron to
execute the downloaded payload every minute.”
“This attack is very dangerous due to the fact the attacker uses
container escape techniques to gain full control of the victim’s
infrastructure.”
Once done, the malware also leverages compromised systems to
further scan the network for ports associated with Redis, Docker,
SSH, and HTTP, using a scanning tool like zmap, zgrap, and
jq.
Doki managed to stay under the radar for more than six months
despite having been uploaded to VirusTotal on January 14, 2020, and
scanned multiple times since. Surprisingly, at the time of writing,
it’s still undetectable by any of the 61 top malware detection
engines.
The most prominent container software has been targeted for the
second time in a month. Late last month, malicious actors were
found targeting exposed Docker API endpoints and crafted
malware-infested images to facilitate DDoS attacks and mine
cryptocurrencies[3].
Users and organizations who run Docker instances are advised not
to expose docker APIs to the Internet, but if you still need to,
ensure that it is reachable only from a trusted network or VPN, and
only to trusted users to control your Docker daemon.
If you manage Docker from a web server to provision containers
through an API, you should be even more careful than usual with
parameter checking to ensure that a malicious user cannot pass
crafted parameters causing Docker to create arbitrary
containers.
Adhere to best Docker security
practices here.
[4]
References
- ^
undetectable Linux malware
(www.virustotal.com) - ^
shared
(www.intezer.com) - ^
facilitate DDoS attacks and mine
cryptocurrencies (thehackernews.com) - ^
Docker security practices
(docs.docker.com)
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/Of2qe5V0Wgk/docker-linux-malware.html