a new high-risk vulnerability affecting billions of devices
worldwide—including servers and workstations, laptops, desktops,
and IoT systems running nearly any Linux distribution or Windows
system.
Dubbed ‘BootHole‘ and tracked as CVE-2020-10713,
the reported vulnerability resides in the GRUB2 bootloader, which,
if exploited, could potentially let attackers bypass the Secure
Boot feature and gain high-privileged persistent and stealthy
access to the targeted systems.
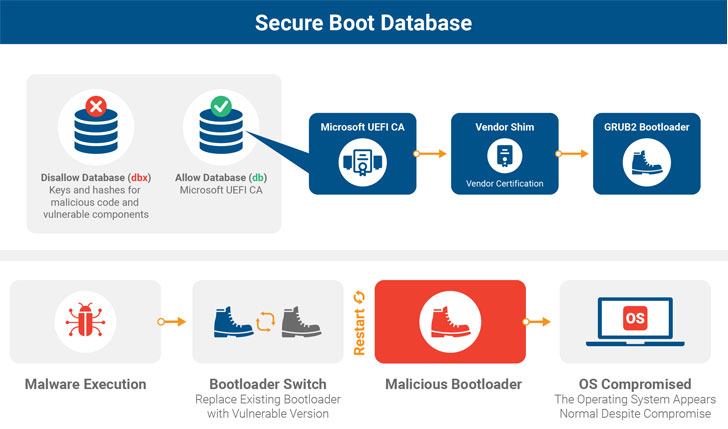
Secure Boot is a security feature of the Unified Extensible
Firmware Interface (UEFI) that uses a bootloader to load critical
components, peripherals, and the operating system while ensuring
that only cryptographically signed code executes during the boot
process.
“One of the explicit design goals of Secure Boot is to prevent
unauthorized code, even running with administrator privileges, from
gaining additional privileges and pre-OS persistence by disabling
Secure Boot or otherwise modifying the boot chain,” the report
explained.
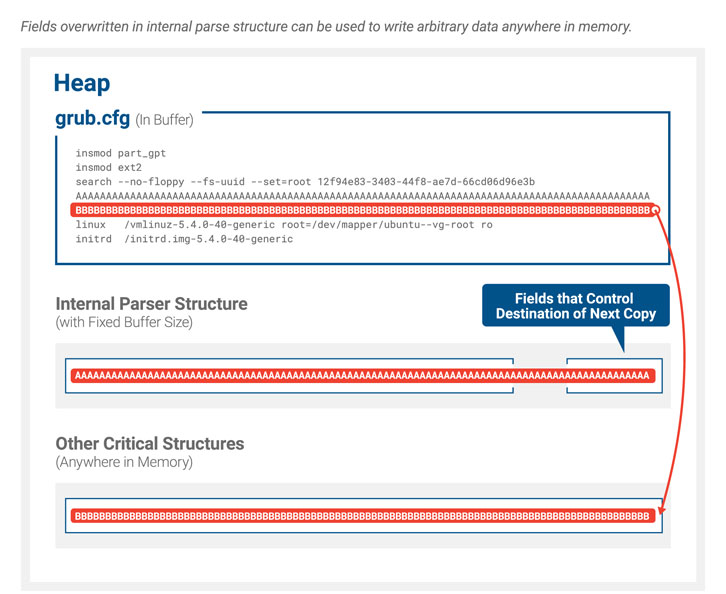
Discovered by researchers from Eclypsium, BootHole is a buffer
overflow vulnerability that affects all versions of GRUB2 and
exists in the way it parses content from the config file, which
typically is not signed like other files and executables—leaving an
opportunity for attackers to break the hardware root of trust
mechanism.
partition, and thus, to modify the file, an attacker still needs an
initial foothold on the targeted system with admin privileges that
would eventually provide the attacker with an additional escalation
of privilege and persistence on the device.
Though GRUB2 is the standard bootloader used by most Linux
systems, it supports other operating systems, kernels, and
hypervisors like XEN as well.
“The buffer overflow allows the attacker to gain arbitrary code
execution within the UEFI execution environment, which could be
used to run malware, alter the boot process, directly patch the OS
kernel, or execute any number of other malicious actions,”
researchers said.
Thus, to exploit BootHole flaw on Windows systems, attackers can
replace the default bootloaders installed on Windows systems with a
vulnerable version of GRUB2 to install the rootkit malware.
“The problem also extends to any Windows device that uses Secure
Boot with the standard Microsoft Third Party UEFI Certificate
Authority,” the report says.
According to the detailed
report[1] researchers shared with
The Hacker News, this vulnerability can lead to major consequences,
and that’s primarily because the attack allows hackers to execute
malicious code even before the operating system boots, making it
difficult for security software to detect the presence of malware
or remove it.
Besides this, the researcher also added that “the UEFI execution
environment does not have Address Space Layout Randomization (ASLR)
or Data Execution Prevention (DEP/NX) or other exploit mitigation
technologies typically found in modern operating systems, so
creating exploits for this kind of vulnerability is significantly
easier.”
entities, including OS vendors and computer manufacturers, to help
them patch the issue.
However, it doesn’t appear to be an easy task to patch the issue
altogether. The three-stage mitigation process will likely take
years for organizations to complete patching.
According to Eclypsium, even “mitigation will require new
bootloaders to be signed and deployed, and vulnerable bootloaders
should be revoked to prevent adversaries from using older,
vulnerable versions in an attack.”
In an advisory[2]
released today, Microsoft acknowledged the issue, informing that
it’s “working to complete validation and compatibility testing of a
required Windows Update that addresses this vulnerability.”
It also recommended users to apply security patches as soon as
they are rolled out in the coming weeks.
Besides Microsoft, many popular Linux distributions have also
released related advisories explaining the flaw, possible
mitigations, and timeline on the upcoming security patches.
Here’s a list for all advisories:
References
- ^
detailed report
(eclypsium.com) - ^
advisory
(portal.msrc.microsoft.com)
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/WBdiyKEddek/grub2-bootloader-vulnerability.html