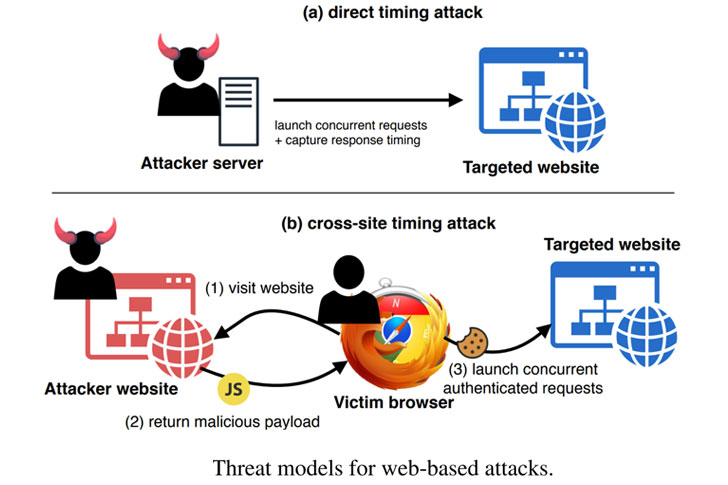
renders a remote timing-based side-channel attack more effective
regardless of the network congestion between the adversary and the
target server.
Remote timing
attacks[1] that work over a network
connection are predominantly affected by variations in network
transmission time (or jitter), which, in turn, depends on the load
of the network connection at any given point in time.
But since measuring the time taken to execute cryptographic
algorithms is crucial to carrying out a timing attack and
consequently leak information, the jitter on the network path from
the attacker to the server can make it impractical to successfully
exploit timing side-channels that rely on a small difference in
execution time.
The new method, called Timeless Timing
Attacks (TTAs) by researchers from DistriNet Research Group and
New York University Abu Dhabi, instead leverages multiplexing of
network protocols and concurrent execution by applications, thus
making the attacks immune to network conditions.
[2]
“These concurrency-based timing attacks infer a relative timing
difference by analyzing the order in which responses are returned,
and thus do not rely on any absolute timing information,” the
researchers said.
Using HTTP/2’s Request Multiplexing to Reduce Jitter
Unlike the typical timing-based attacks, wherein the execution
times are measured independently and sequentially, the latest
technique attempts to extract information from the order and the
relative timing difference between two concurrently executed
requests without relying on any timing information.
To do so, a bad actor initiates a pair of HTTP/2 requests to the
victim server either directly or using a cross-site — such as a
malicious advertisement or tricking the victim into visiting an
attacker-controlled web page — to launch requests to the server via
JavaScript code.
response time between the second request and the first. The TTA,
then, works by taking into account whether this difference is
positive or negative, where positive indicates that the processing
time of the first request takes less time than processing the
second request.
“On web servers hosted over HTTP/2, we find that a timing
difference as small as 100ns can be accurately inferred from the
response order of approximately 40,000 request-pairs,” the
researchers noted.
“The smallest timing difference that we could observe in a
traditional timing attack over the Internet was 10μs, 100 times
higher than our concurrency-based attack.”
A limitation of this approach is that attacks aimed at servers
using HTTP/1.1 cannot exploit the protocol to coalesce multiple
requests in a single network packet, thereby requiring that a
concurrent timing attack be performed using multiple connections
instead of sending all requests over the same connection.
This stems from HTTP/1.1’s use of head-of-line (HOL) blocking,
which causes all requests over the same connection to be handled
sequentially, whereas HTTP/2 addresses this issue through request
multiplexing.
[3]
Currently, 37.46% of all desktop
websites are served over HTTP/2, a number that increases
further to 54.04% for sites that support HTTPS. Although this makes
a huge number of websites susceptible to TTAs, the researchers note
that many of them rely on content delivery networks (CDN), such as
Cloudflare, which still uses HTTP/1.1 for connections between the
CDN and the origin site.
Tor Onion Service and Wi-Fi EAP-PWD Vulnerable
But in a twist, the researchers found that concurrency-based timing
attacks can also be deployed against Tor onion services, including
those that only support HTTP/1.1, allowing an attacker to create
two Tor connections to a particular onion service, and then
simultaneously send a request on each of the connections to measure
a timing difference of 1μs.
That’s not all. The EAP-PWD
authentication[5]
method, which uses a shared password between the server and
supplicant when connecting to Wi-Fi networks, is rendered
vulnerable to dictionary attacks by exploiting a timing leak in the
Dragonfly handshake
protocol[6] to reveal the
information about the password itself.
Although timing attacks can be countered by ensuring
constant-time execution, it’s easier said than done, especially for
applications that rely on third-party components. Alternatively,
the researchers suggest adding a random delay to incoming requests
and ensure that different requests are not combined in a single
packet.
This is not the first time remote timing attacks have been
employed to leak sensitive information. Researchers have previously
demonstrated it’s possible to exploit cache side-channels to sniff
out SSH passwords from Intel CPU cache (NetCAT[7]) and even achieve
Spectre-like
speculative execution[8]
over a network connection (NetSpectre[9]).
“Since the NetSpectre attacks target applications above the
network layer, an attacker could, in theory, leverage our
concurrency-based timing attacks to improve the timing accuracy,”
the researchers said.
The findings will be presented at the USENIX Security
Symposium[10] later this year. The
researchers have also published a Python-based
tool[11] to test HTTP/2 servers
for TTA vulnerabilities.
References
- ^
timing
attacks (en.wikipedia.org) - ^
Timeless Timing Attacks
(tom.vg) - ^
HOL
(en.wikipedia.org) - ^
desktop websites
(almanac.httparchive.org) - ^
EAP-PWD authentication
(en.wikipedia.org) - ^
Dragonfly handshake protocol
(tools.ietf.org) - ^
NetCAT
(thehackernews.com) - ^
Spectre-like speculative execution
(thehackernews.com) - ^
NetSpectre (v) - ^
USENIX Security Symposium
(www.usenix.org) - ^
Python-based tool
(github.com)
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/5dvftYNf1vo/http2-timing-side-channel-attacks.html