headlines earlier this year for uncovering severe security
issues in the 4G LTE and 5G networks—today presented a new
attack called ‘ReVoLTE,’ that could let remote attackers
break the encryption used by VoLTE voice calls and spy on
targeted phone calls.
The attack doesn’t exploit any flaw in the Voice over LTE
(VoLTE) protocol; instead, it leverages weak implementation of the
LTE mobile network by most telecommunication providers in practice,
allowing an attacker to eavesdrop on the encrypted phone calls made
by targeted victims.
VoLTE or Voice over Long Term Evolution protocol is a standard
high-speed wireless communication for mobile phones and data
terminals, including Internet of things (IoT) devices and
wearables, deploying 4G LTE radio access technology.
same keystream for two subsequent calls within one radio connection
to encrypt the voice data between the phone and the same base
station, i.e., mobile phone tower.
Thus, the new ReVoLTE
attack[2] exploits the reuse of
the same keystream by vulnerable base stations, allowing attackers
to decrypt the contents of VoLTE powered voice calls in the
following scenario.
pointed out by Raza &
Lu, but the ReVoLTE attack turns it into a practical attack.
How Does the ReVoLTE Attack Work?
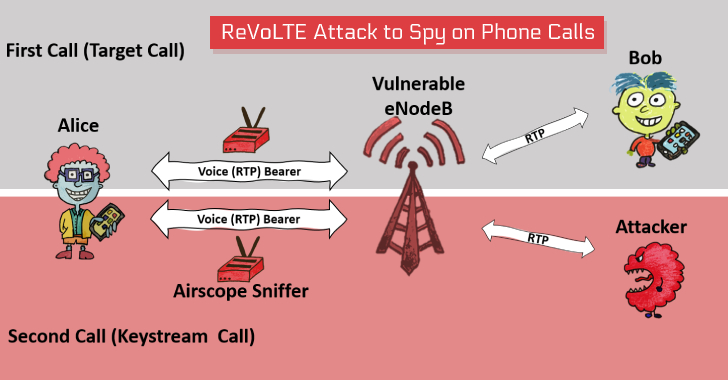
To initiate this attack, the attacker must be connected to the same
base station as the victim and place a downlink sniffer to monitor
and record a ‘targeted call’ made by the victim to someone else
that needs to be decrypted later, as part of the first phase of
ReVoLTE attack.
Once the victim hangs up the ‘targeted call,’ the attacker is
required to call the victim, usually within 10 seconds immediately,
which would force the vulnerable network into initiating a new call
between victim and attacker on the same radio connection as used by
previous targeted call.
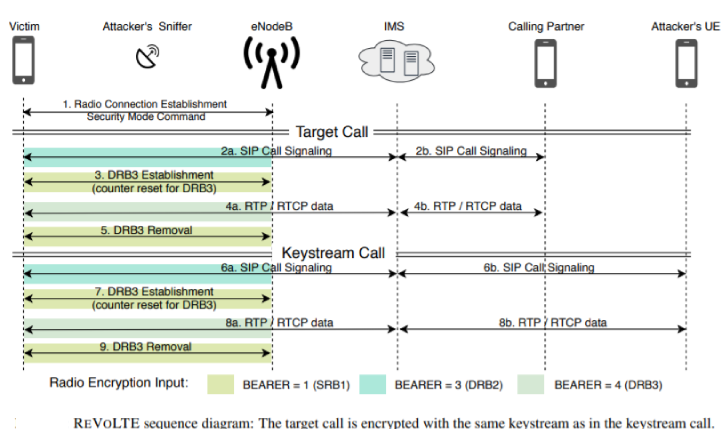
“The keystream reuse occurs when the target and keystream call use
the same user-plane encryption key. As this key is updated for
every new radio connection, the attacker must ensure that the first
packet of the keystream call arrives within the active phase after
the target call,” the researchers said.
engage the victim into a conversation and record it in plaintext,
which would help the attacker later reverse compute the keystream
used by the subsequent call.
According to researchers, XOR-ing the keystreams with the
corresponding encrypted frame of the targeted call captured in the
first phase decrypts its content, allowing attackers to listen to
what conversation its victim had in the previous phone call.
“As this results in the same keystream, all RTP data is
encrypted in the same way as the voice data of the target call. As
soon as a sufficient amount of keystream data was generated, the
adversary cancels the call,” the paper reads.
However, the length of the second call should be greater than or
equal to the first call in order to decrypt each frame; otherwise,
it can only decrypt a part of the conversation.
“It is important to note that the attacker has to engage the victim
in a longer conversation. The longer he/she talked to the victim,
the more content of the previous communication he/she can decrypt,”
the paper reads.
“Each frame is associated with a count and encrypted with an
individual keystream that we extract during the keystream
computation. As the same count generates the same keystream, the
count synchronizes the keystreams with encrypted frames of the
target call. XOR-ing the keystreams with the corresponding
encrypted frame decrypts the target call.”
“As we aim to decrypt the complete call, the keystream call must be
as long as the target call to provide a sufficient number of
packets, as otherwise we can only decrypt a part of the
conversation.”
Detecting ReVoLTE Attack and Demonstration
To demonstrate the practical feasibility of the ReVoLTE attack, the
team of academics from Ruhr University Bochum implemented an
end-to-end version of the attack within a commercial, vulnerable
network and commercial phones.
The team used the downlink analyzer Airscope by Software Radio
System to sniff the encrypted traffic and three Android-based
phones to obtain the known-plaintext at the attacker’s phone. It
then compared the two recorded conversations, determined the
encryption key, and finally decrypted a portion of the previous
call.
You can see the demo video of the ReVoLTE attack, which, according
to the researchers, could cost less than $7000 to attackers for
setting up the attack and, eventually, decrypting downlink traffic.
The team tested a number of randomly selected radio cells across
Germany to determine the scope of the issue and found that it
affects 12 out of 15 base stations in Germany, but researchers said
the security gap also affects other countries.
Researchers notified the affected German base station operators
about the ReVoLTE attack through the GSMA Coordinated Vulnerability
Disclosure Programme process in early December 2019, and the
operators managed to deploy the patches by the time of
publication.
Since the issue also affects a large number of providers
worldwide, researchers released an open source Android app, called
‘Mobile
Sentinel[4],’ that you can use to
detect whether their 4G network and base stations are vulnerable to
the ReVoLTE attack or not.
Researchers—David Rupprecht, Katharina Kohls and Thorsten Holz
of RUB University Bochum and Christina Pöpper of NYU Abu Dhabi—have
also released a dedicated website[5] and research paper
PDF[6], titled “Call Me Maybe:
Eavesdropping Encrypted LTE Calls With REVOLTE,” detailing the
ReVoLTE attack, where you can find more details.
References
- ^
security issues in the 4G LTE and 5G
networks (thehackernews.com) - ^
ReVoLTE attack
(revolte-attack.net) - ^
Raza & Lu
(www.researchgate.net) - ^
Mobile Sentinel
(github.com) - ^
dedicated website
(revolte-attack.net) - ^
PDF
(revolte-attack.net)
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/wXc99BfpOYM/a-team-of-academic-researcherswho.html