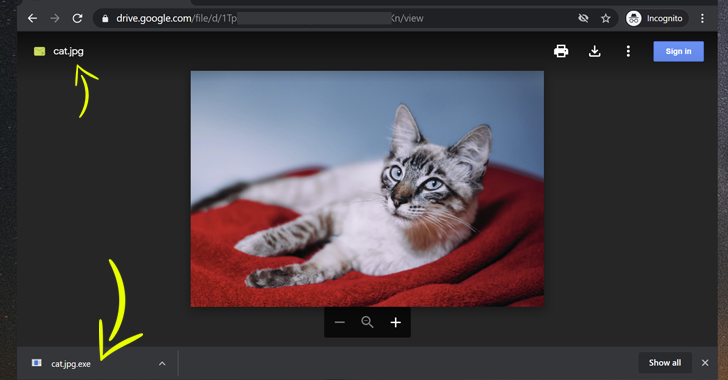
exploited by malware attackers to distribute malicious files
disguised as legitimate documents or images, enabling bad actors to
perform spear-phishing attacks comparatively with a high success
rate.
The latest security issue—of which Google is aware but,
unfortunately, left unpatched—resides in the “manage
versions[1]” functionality offered
by Google Drive that allows users to upload and manage different
versions of a file, as well as in the way its interface provides a
new version of the files to the users.
Logically, the manage versions functionally should allow Google
Drive users to update an older version of a file with a new
version having the same file extension, but it turns out that it’s
not the case.
According to A. Nikoci, a system administrator by profession who
reported the flaw to Google and later disclosed it to The Hacker
News, the affected functionally allows users to upload a new
version with any file extension for any existing file on the cloud
storage, even with a malicious executable.
The Hacker News—in doing so, a legitimate version of the file
that’s already been shared among a group of users can be replaced
by a malicious file, which when previewed online doesn’t indicate
newly made changes or raise any alarm, but when downloaded can be
employed to infect targeted systems.
“Google lets you change the file version without checking if
it’s the same type,” Nikoci said. “They did not even force the same
extension.”
Needless to say, the issue leaves the door open for highly
effective spear-phishing campaigns that take advantage of the
widespread prevalence of cloud services such as Google Drive to
distribute malware.
The development comes as Google recently fixed a security flaw in
Gmail that could have allowed a threat actor to send spoofed
emails mimicking any Gmail or G Suite customer, even when strict
DMARC/SPF security policies are enabled.
Malware Hackers Love Google Drive
Spear-phishing scams typically attempt to trick recipients into
opening malicious attachments or clicking seemingly innocuous
links, thereby providing confidential information, like account
credentials, to the attacker in the process.
The links and attachments can also be used to get the recipient
to unknowingly download malware that can give the attacker access
to the user’s computer system and other sensitive information.
This new security issue is no different. Google Drive’s file
update feature is meant to be an easy way to update shared files,
including the ability to replace the document with a completely new
version from the system. This way, the shared file can be updated
without changing its link.
However, without any validation for file extensions, this can have
potentially serious consequences when users of the shared file,
who, upon notification of the change via an email, end up
downloading the document and unwittingly infecting their systems
with malware.
Such a scenario could be leveraged to mount whaling
attacks[3], a phishing tactic often
used by cyber-criminal gangs to masquerade as senior management
personnel in an organization and target specific individuals,
hoping to steal sensitive information or gain access to their
computer systems for criminal purposes.
Even worse, Google Chrome appears to implicitly trust the files
downloaded from Google Drive even when they are detected by other
antivirus software as malicious.
Cloud Services Become An Attack Vector
Although there’s no evidence that this flaw has been exploited in
the wild, it wouldn’t be difficult for attackers to repurpose it
for their benefit given how cloud services have been a vehicle for
malware delivery in several spear-phishing attacks in recent
months.
Earlier this year, Zscaler
identified a phishing campaign that employed Google Drive to
download a password stealer post initial compromise.
Last month, Check Point
Research[5] and Cofense[6] highlighted a series of
new campaigns wherein threat actors were found not only using spam
emails to embed malware hosted on services like Dropbox and Google
Drive but also exploiting cloud storage services to host phishing
pages[7].
ESET, in an analysis of the Evilnum APT
group[8], observed a similar
trend where fintech companies in Europe and the UK have been
targeted with spear-phishing emails that contain a link to a ZIP
file hosted on Google Drive to steal software licenses, customer
credit card information, and investments and trading documents.
Likewise, Fortinet, in a campaign spotted earlier this month,
uncovered evidence of a COVID-19-themed
phishing[9] lure that purportedly
warned users of delayed payments due to the pandemic, only to
download the NetWire remote access Trojan hosted on a Google Drive
URL.
With scammers and criminals pulling out all the stops to conceal
their malicious intentions, it’s essential that users keep a close
eye on suspicious emails, including Google Drive notifications, to
mitigate any possible risk.
References
- ^
manage versions
(support.google.com) - ^
security flaw in Gmail
(ezh.es) - ^
whaling attacks
(www.kaspersky.com) - ^
Zscaler
(www.zscaler.com) - ^
Check Point Research
(research.checkpoint.com) - ^
Cofense
(cofense.com) - ^
host phishing pages
(blog.checkpoint.com) - ^
Evilnum APT group
(www.welivesecurity.com) - ^
COVID-19-themed phishing
(www.fortinet.com)
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/C-StKJrAZ8I/google-drive-file-versions.html