Google’s Project Zero team has made public details of an
improperly patched zero-day security vulnerability in Windows print
spooler API that could be leveraged by a bad actor to execute
arbitrary code.
Details of the unpatched flaw were revealed publicly after
Microsoft failed to patch it within 90 days of responsible
disclosure on September 24.
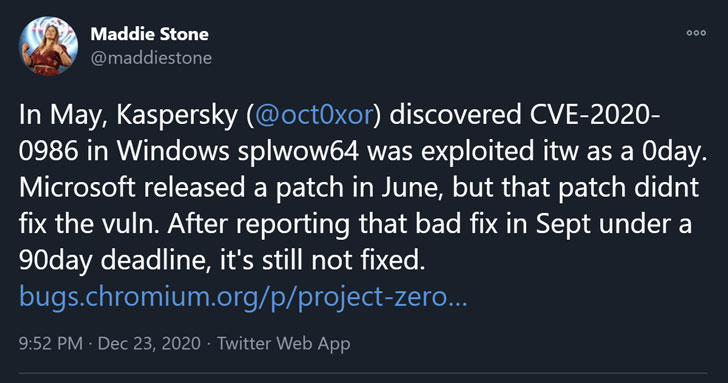
Originally tracked as CVE-2020-0986[1], the flaw concerns an
elevation of privilege exploits in the GDI Print / Print Spooler[2]
API (“splwow64.exe”) that was reported to Microsoft by an anonymous
user working with Trend Micro’s Zero Day Initiative (ZDI) back in
late December 2019.
But with no patch in sight for about six months, ZDI ended up
posting a public advisory[3]
as a zero-day on May 19 earlier this year, after which it was
exploited[4]
in the wild in a campaign dubbed “Operation PowerFall[5]” against an unnamed
South Korean company.
“splwow64.exe” is a Windows core system binary that allows
32-bit applications to connect with the 64-bit printer spooler
service on 64-bit Windows systems. It implements a Local Procedure
Call (LPC[6]) server that can be used
by other processes to access printing functions.
Successful exploitation of this vulnerability could result in an
attacker manipulating the memory of the “splwow64.exe” process to
achieve execution of arbitrary code in kernel mode, ultimately
using it to install malicious programs; view, change, or delete
data; or create new accounts with full user rights.
However, to achieve this, the adversary would first have to log
on to the target system in question.
Although Microsoft eventually addressed[7]
the shortcoming as part of its June Patch Tuesday update, new
findings from Google’s security team reveals that the flaw has not
been fully remediated.
“The vulnerability still exists, just the exploitation method
had to change,” Google Project Zero researcher Maddie Stone
said[8]
in a write-up.
“The original issue was an arbitrary pointer dereference which
allowed the attacker to control the src and dest pointers to a
memcpy,” Stone detailed[9]. “The ‘fix’ simply
changed the pointers to offsets, which still allows control of the
args to the memcpy.”
The newly reported elevation of privilege flaw, identified as
CVE-2020-17008, is expected to be resolved by Microsoft on January
12, 2021, due to “issues identified in testing” after promising an
initial fix in November.
Stone has also shared a proof-of-concept (PoC) exploit code for
CVE-2020-17008, based off of a POC released by Kaspersky for
CVE-2020-0986.
“There have been too many occurrences this year of zero-days
known to be actively exploited being fixed incorrectly or
incompletely,” Stone said[10]. “When [in the wild]
zero-days aren’t fixed completely, attackers can reuse their
knowledge of vulnerabilities and exploit methods to easily develop
new 0-days.”
References
- ^
CVE-2020-0986
(googleprojectzero.blogspot.com) - ^
Print
Spooler (docs.microsoft.com) - ^
advisory
(www.zerodayinitiative.com) - ^
exploited
(securelist.com) - ^
Operation PowerFall
(securelist.com) - ^
LPC
(en.wikipedia.org) - ^
addressed
(msrc.microsoft.com) - ^
said
(bugs.chromium.org) - ^
detailed
(twitter.com) - ^
said
(twitter.com)