Citrix has issued an emergency advisory warning its customers of
a security issue affecting its NetScaler application delivery
controller (ADC) devices that attackers are abusing to launch
amplified distributed denial-of-service (DDoS) attacks against
several targets[1].
“An attacker or bots can overwhelm the Citrix ADC [Datagram
Transport Layer Security] network throughput, potentially leading
to outbound bandwidth exhaustion,” the company noted[2]. “The effect of this
attack appears to be more prominent on connections with limited
bandwidth.”
ADCs are purpose-built networking
appliances[3] whose function is to
improve the performance, security, and availability of applications
delivered over the web to end-users.
The desktop virtualization and networking service provider said
it’s monitoring the incident and is continuing to investigate its
impact on Citrix ADC, adding “the attack is limited to a small
number of customers around the world.”
The issue came to light after multiple reports of a DDoS amplify
attack over UDP/443 against Citrix (NetScaler) Gateway devices at
least since December 19, according to Marco Hofmann[4], an IT administrator for
a German software firm ANAXCO GmbH.
Datagram Transport Layer Security or DTLS[5]
is based on the Transport Layer Security (TLS) protocol that aims
to provide secure communications in a way that’s designed to thwart
prevent eavesdropping, tampering, or message forgery.
Since DTLS uses the connectionless[6]
User Datagram Protocol (UDP) protocol, it’s easy for an attacker to
spoof an IP packet datagram[7] and include an arbitrary
source IP address.
Thus when the Citrix ADC is flooded with an overwhelming flux of
DTLS packets whose source IP addresses are forged to a victim IP
address, the elicit responses lead to an oversaturation of
bandwidth, creating a DDoS condition.
Citrix is currently working to enhance DTLS to eliminate the
susceptibility to this attack, with an expected patch to be
released on January 12, 2021.
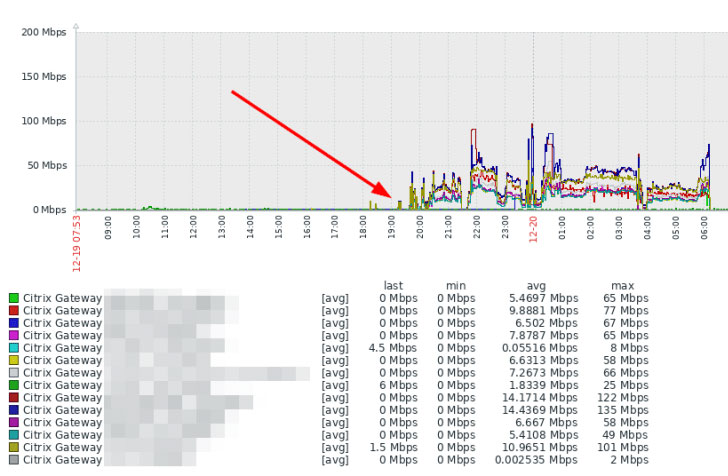
To determine if a Citrix ADC equipment is targeted by the
attack, Cisco recommends keeping an eye on the outbound traffic
volume for any significant anomaly or spikes.
Customers impacted by the attack, in the meantime, can disable
DTLS while a permanent fix from Citrix is pending by running the
following command on the Citrix ADC: “set vpn vserver
<vpn_vserver_name> -dtls OFF.”
References
- ^
several
targets (twitter.com) - ^
noted
(support.citrix.com) - ^
networking appliances
(www.citrix.com) - ^
Marco
Hofmann (www.meinekleinefarm.net) - ^
DTLS
(en.wikipedia.org) - ^
connectionless
(en.wikipedia.org) - ^
spoof an
IP packet datagram (us-cert.cisa.gov)
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/4DJfJATymo8/citrix-adc-ddos-attack.html