Cybersecurity researchers today revealed a wide-ranging scam
targeting cryptocurrency users that began as early as January last
year to distribute trojanized applications to install a previously
undetected remote access tool on target systems.
Called ElectroRAT by Intezer, the RAT is written from
ground-up in Golang and designed to target multiple operating
systems such as Windows, Linux, and macOS.
The apps are developed using the open-source Electron
cross-platform desktop app framework.
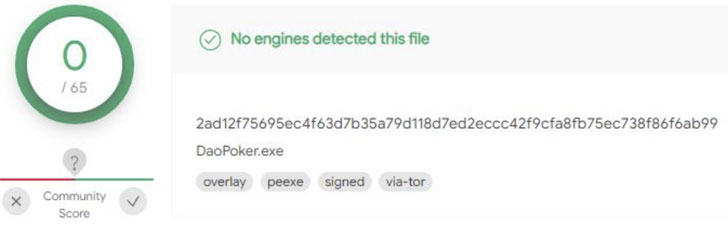
“ElectroRAT is the latest example of attackers using Golang to
develop multi-platform malware and evade most antivirus engines,”
the researchers said[1].
“It is common to see various information stealers trying to
collect private keys to access victims wallets. However, it is rare
to see tools written from scratch and targeting multiple operating
systems for these purposes.”
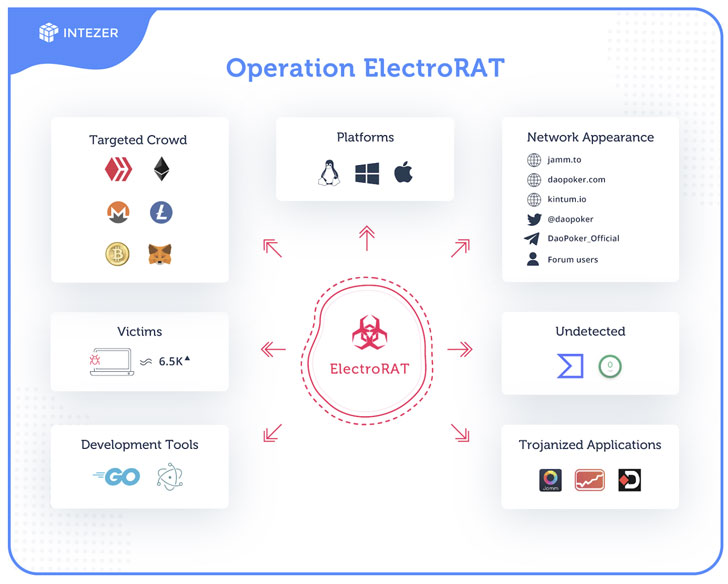
The campaign, first detected in December, is believed to have
claimed over 6,500 victims based on the number of unique visitors
to the Pastebin pages used to locate the command and control (C2)
servers.
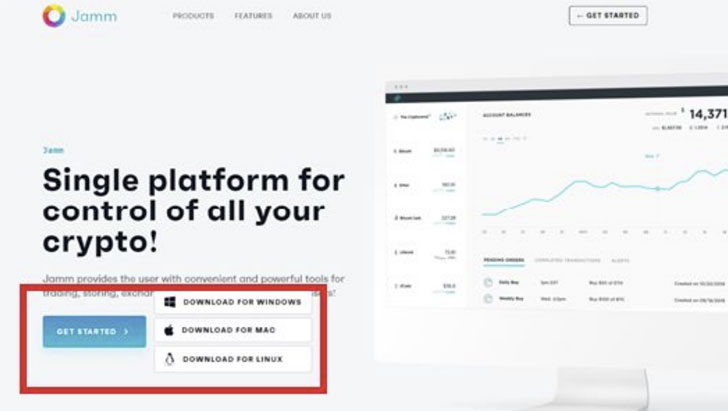
“Operation ElectroRAT” involved the attackers creating three
different tainted applications — each with a Windows, Linux, Mac
version — two of which pose as cryptocurrency trade management
applications by the name of “Jamm” and “eTrade,” while a third app
called “DaoPoker” masquerades as a cryptocurrency poker
platform.
Not only are the malicious apps hosted on websites built
specifically for this campaign, but the services are also
advertised on Twitter, Telegram, and legitimate cryptocurrency and
blockchain-related forums such as “bitcointalk” and “SteemCoinPan”
in an attempt to lure unsuspecting users into downloading the
tainted apps.
Once installed, the app opens a harmless-looking user interface
when in reality, the ElectroRAT runs hidden in the background as
“mdworker,” which comes with intrusive capabilities to capture
keystrokes, take screenshots, upload files from disk, download
arbitrary files, and execute malicious commands received from the
C2 server on the victim’s machine.
Interestingly, an analysis of the Pastebin pages — which were
published by a user named “Execmac” as early as January 8, 2020 —
and those posted by the same user prior to the campaign found C2
servers used in conjunction with Windows malware like Amadey[2]
and KPOT[3], suggesting the
attackers have pivoted from using well-known trojans to a new RAT
capable of targeting multiple operating systems.
“Another motivating factor is this is an unknown Golang malware,
which has allowed the campaign to fly under the radar for a year by
evading all antivirus detections,” the researchers said.
Users who have fallen victim to this campaign are urged to kill
the process, delete all files related to the malware, move the
funds to a new wallet, and change their passwords.
References
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/qSZYJtNE9ks/warning-cross-platform-electrorat.html