Google has rolled out yet another update to Chrome browser for
Windows, Mac, and Linux to fix four security vulnerabilities,
including one zero-day flaw that’s being exploited in the wild.
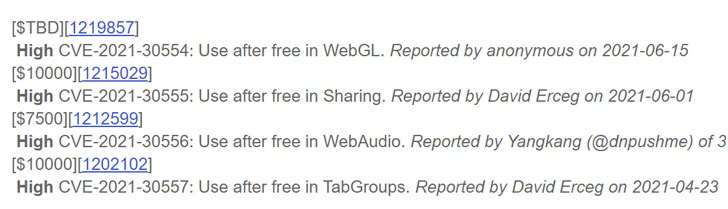
Tracked as CVE-2021-30554, the high severity
flaw concerns a use after free vulnerability[1] in WebGL (aka Web
Graphics Library), a JavaScript API for rendering interactive 2D
and 3D graphics within the browser.
Successful exploitation of the flaw could mean corruption of
valid data, leading to a crash, and even execution of unauthorized
code or commands.
The issue was reported to Google anonymously on June 15, Chrome
technical program manager Srinivas Sista noted[2], adding the company is
“aware that an exploit for CVE-2021-30554 exists in the wild.”
While it’s usually the norm to limit details of the
vulnerability until a majority of users are updated with the fix,
the development comes less than 10 days after Google addressed
another zero-day vulnerability exploited in active attacks
(CVE-2021-30551[3]).
CVE-2021-30554 is also the eighth zero-day flaw patched by
Google since the start of the year.
“I’m happy we are getting better at detecting these exploits and
the great partnerships we have to get the vulnerabilities patched,
but I remain concerned about how many are being discovered on an
ongoing basis and the role of commercial providers,” tweeted[4]
Shane Huntley, Director of Google’s Threat Analysis Group, on June
8.
Chrome users are recommended to update to the latest version
(91.0.4472.114) by heading to Settings > Help > ‘About Google
Chrome’ to mitigate the risk associated with the flaw.
References
- ^
use
after free vulnerability (cwe.mitre.org) - ^
noted
(chromereleases.googleblog.com) - ^
CVE-2021-30551
(thehackernews.com) - ^
tweeted
(twitter.com)