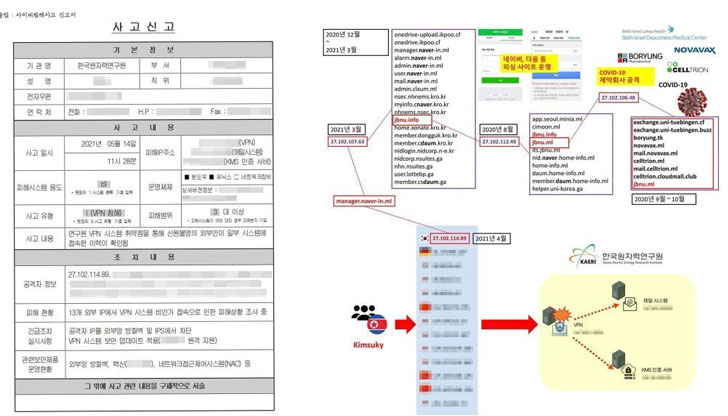
South Korea’s state-run Korea Atomic Energy Research Institute
(KAERI) on Friday disclosed that its internal network was
infiltrated by suspected attackers operating out of its northern
counterpart.
The intrusion is said to have taken place on May 14 through a
vulnerability in an unnamed virtual private network (VPN) vendor
and involved a total of 13 IP addresses[1], one of which —
“27.102.114[.]89” — has been previously linked to a state-sponsored
threat actor dubbed Kimsuky[2].
KAERI, established in 1959 and situated in the city of Daejeon,
is a government-funded research institute that designs and develops
nuclear technologies related to reactors, fuel rods, radiation
fusion, and nuclear safety.
Following the intrusion, the think tank said it took steps to
block the attacker’s IP addresses in question and applied necessary
security patches to the vulnerable VPN solution. “Currently, the
Atomic Energy Research Institute is investigating the subject of
the hacking and the amount of damage,” the entity said[3]
in a statement.
The development comes following a report from SISA Journal[4], which disclosed the
breach, alleging that the agency was attempting to cover up the
hack by denying such an incident took place. KAERI attributed it to
a “mistake in the response of the working-level staff.”
Active since 2012, Kimsuky (aka Velvet Chollima, Black Banshee,
or Thallium) is a North Korean threat actor known for its
cyberespionage campaigns targeting think tanks and nuclear power
operators in South Korea.
Earlier this month, cybersecurity firm Malwarebytes disclosed[5]
a wave of attacks undertaken by the adversary to strike
high-profile government officials in the country by installing an
Android and Windows backdoor called AppleSeed for amassing valuable
information.
The targeted entities involved the Ministry of Foreign Affairs,
Ambassador of the Embassy of Sri Lanka to the State, International
Atomic Energy Agency (IAEA) Nuclear Security Officer, and the
Deputy Consul General at Korean Consulate General in Hong Kong,
with the aforementioned IP address used for command-and-control
(C2) communications.
It is not immediately clear what VPN vulnerability was exploited
to breach the network. But it’s worth noting that unpatched VPN
systems from Pulse Secure[6], SonicWall[7], Fortinet FortiOS, and Citrix[8] have been subjected to
attacks by multiple threat actors in recent years.
References
- ^
total of
13 IP addresses (www.koreadaily.com) - ^
Kimsuky
(malpedia.caad.fkie.fraunhofer.de) - ^
said
(www.kaeri.re.kr) - ^
SISA
Journal (www.sisajournal.com) - ^
disclosed
(thehackernews.com) - ^
Pulse
Secure (thehackernews.com) - ^
SonicWall
(thehackernews.com) - ^
Fortinet
FortiOS, and Citrix (thehackernews.com)