Microsoft has shared technical details about a now-fixed,
actively exploited critical security vulnerability affecting
SolarWinds Serv-U managed file transfer service that it has
attributed with “high confidence” to a threat actor operating out
of China.
In mid-July, the Texas-based company remedied[1]
a remote code execution flaw (CVE-2021-35211[2]) that was rooted in
Serv-U’s implementation of the Secure Shell (SSH) protocol, which
could be abused by attackers to run arbitrary code on the infected
system, including the ability to install malicious programs and
view, change, or delete sensitive data.
“The Serv-U SSH server is subject to a pre-auth remote code
execution vulnerability that can be easily and reliably exploited
in the default configuration,” Microsoft Offensive Research and
Security Engineering team said in a detailed write-up[3]
describing the exploit.
“An attacker can exploit this vulnerability by connecting to the
open SSH port and sending a malformed pre-auth connection request.
When successfully exploited, the vulnerability could then allow the
attacker to install or run programs, such as in the case of the
targeted attack we previously reported,” the researchers added.
While Microsoft linked[4]
the attacks to DEV-0322, a China-based collective citing “observed
victimology, tactics, and procedures,” the company has now revealed
that the remote, pre-auth vulnerability stemmed from the manner the
Serv-U process handled access violations without terminating the
process, thereby making it simple to pull off stealthy, reliable
exploitation attempts.
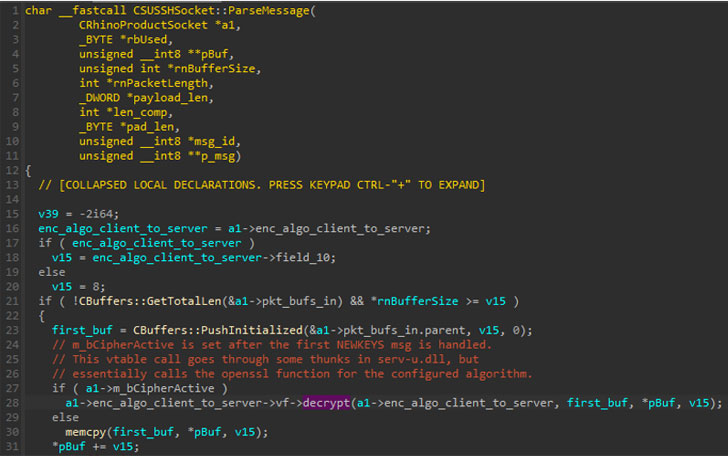
“The exploited vulnerability was caused by the way Serv-U
initially created an OpenSSL AES128-CTR context,” the researchers
said. “This, in turn, could allow the use of uninitialized data as
a function pointer during the decryption of successive SSH
messages.”
“Therefore, an attacker could exploit this vulnerability by
connecting to the open SSH port and sending a malformed pre-auth
connection request. We also discovered that the attackers were
likely using DLLs compiled without address space layout
randomization (ASLR) loaded by the Serv-U process to facilitate
exploitation,” the researchers added.
ASLR refers to a protection mechanism[5]
that’s used to increase the difficulty of performing a buffer
overflow attack by randomly arranging the address space positions
where system executables are loaded into memory.
Microsoft, which disclosed the attack to SolarWinds, said it
recommended enabling ASLR compatibility[6] for all binaries loaded
in the Serv-U process. “ASLR is a critical security mitigation for
services which are exposed to untrusted remote inputs, and requires
that all binaries in the process are compatible in order to be
effective at preventing attackers from using hardcoded addresses in
their exploits, as was possible in Serv-U,” the researchers
said.
If anything, the revelations highlight the variety of techniques
and tools used by threat actors to breach corporate networks,
including piggybacking on legitimate software.
Back in December 2020, Microsoft disclosed that a separate espionage group[7] may have been taking
advantage of the IT infrastructure provider’s Orion software to
drop a persistent backdoor called Supernova on infected systems.
Cybersecurity firm Secureworks connected the intrusions to a
China-linked threat actor called Spiral[8].
References
- ^
remedied
(thehackernews.com) - ^
CVE-2021-35211
(www.solarwinds.com) - ^
detailed
write-up (www.microsoft.com) - ^
linked
(thehackernews.com) - ^
protection mechanism
(www.fireeye.com) - ^
enabling
ASLR compatibility (docs.microsoft.com) - ^
separate
espionage group (thehackernews.com) - ^
Spiral
(thehackernews.com)