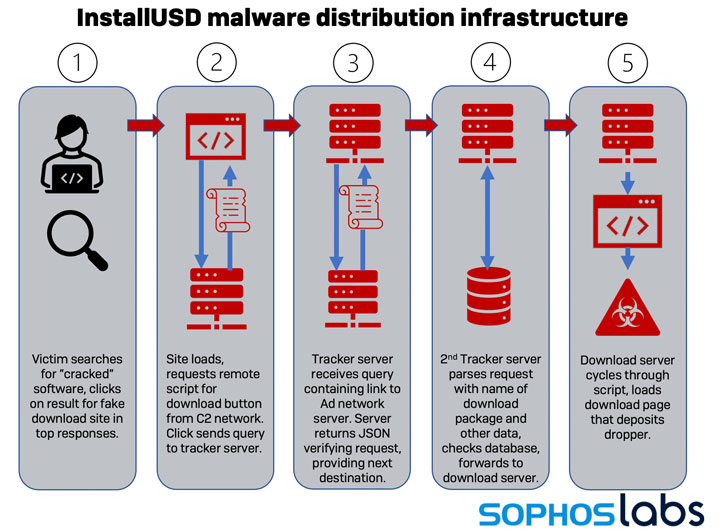
An ongoing campaign has been found to leverage a network of
websites acting as a “dropper as a service” to deliver a bundle of
malware payloads to victims looking for “cracked” versions of
popular business and consumer applications.
“These malware included an assortment of click fraud bots, other
information stealers, and even ransomware,” researchers from
cybersecurity firm Sophos said[1]
in a report published last week.
The attacks work by taking advantage of a number of bait pages
hosted on WordPress that contain “download” links to software
packages, which, when clicked, redirect the victims to a different
website that delivers potentially unwanted browser plug-ins and
malware, such as installers for Raccoon Stealer[2], Stop ransomware, the
Glupteba backdoor, and a variety of malicious cryptocurrency miners
that masquerade as antivirus solutions.
“Visitors who arrive on these sites are prompted to allow
notifications; If they allow this to happen, the websites
repeatedly issue false malware alerts,” the researchers said. “If
the users click the alerts, they’re directed through a series of
websites until they arrive at a destination that’s determined by
the visitor’s operating system, browser type, and geographic
location.”
Using techniques like search engine optimization, links to the
websites appear at the top of search results when individuals
search for pirated versions of a wide range of software apps. The
activities, considered to be the product of an underground
marketplace for paid download services, allows entry-level cyber
actors to set up and tailor their campaigns based on geographical
targeting.
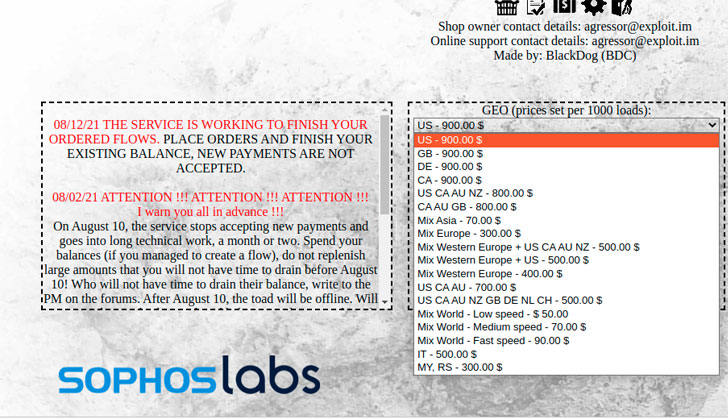
Traffic exchanges, as the distribution infrastructure is also
called, typically require a Bitcoin payment before affiliates can
create accounts on the service and begin distributing installers,
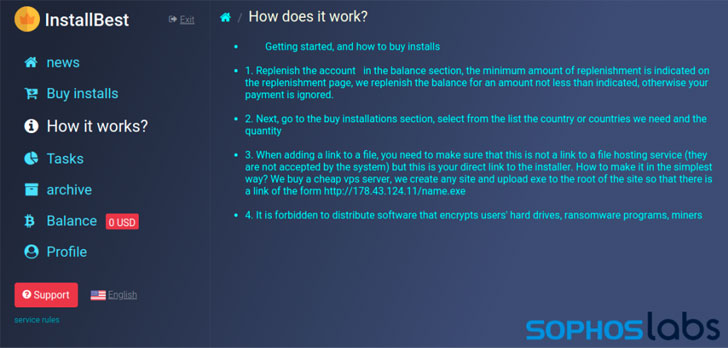
with sites like InstallBest offering advice on “best practices,”
such as recommending against using Cloudflare-based hosts for
downloaders, as well as using URLs within Discord’s CDN, Bitbucket,
or other cloud platforms.
On top of that, the researchers also found some of the services
that act as “go-betweens” to established malvertising networks that
pay website publishers for traffic. One such established traffic
supplier is InstallUSD, a Pakistan-based advertising network, which
has been linked to a number of malware campaigns involving the
cracked software sites.
This is far from the first time “warez” websites have been put
to use as an infection vector by threat actors. Earlier this June,
a cryptocurrency miner called Crackonosh[3]
was found abusing the method to install a coin miner package called
XMRig for stealthily exploiting the infected host’s resources to
mine Monero.
A month later, the attackers behind a piece of malware dubbed
MosaicLoader[4]
were found targeting individuals searching for cracked software as
part of a global campaign to deploy a fully-featured backdoor
capable of roping the compromised Windows systems into a
botnet.
References
- ^
said
(news.sophos.com) - ^
Raccoon
Stealer (news.sophos.com) - ^
Crackonosh
(thehackernews.com) - ^
MosaicLoader
(thehackernews.com)