The average cost of a data breach, according to the latest
research by IBM, now stands at USD 4.24
million[1], the highest reported.
The leading cause? Compromised credentials, often caused by human
error. Although these findings continue to show an upward trend in
the wrong direction, the challenge itself is not new. What is new
is the unprecedented and accelerated complexity of securing the
workplace. CISOs/CIOs are dealing with legacy systems, cloud
hosting, on-prem, remote workers, office based, traditional
software, and SaaS.
How businesses adapted was laudable, but now that employees
spread across locations, offices and homes – with more than half[2]
threatening not to return to offices unless hybrid working is
implemented – the challenge morphs into securing a nonuniform
perimeter.
We know passwords aren’t sufficient. Knowledge-based access is
usually fortified with other forms of multi-factor authentication
(MFA), such as auth apps or FIDO tokens, and in highly sensitive
cases, biometrics.
Why strong IAM is essential for hybrid
working
The era of ‘BYOD’ (Bring Your Own Device) has evolved into what
Gartner[3]
calls Bring-Your-Own-Identity: employees are accessing data from a
range of remote devices from a range of different locations.
Cybercriminals can intercept data in a variety of ways, from
compromised credentials to phishing scams to man-in-the-middle
attacks, which are made easier on public networks with no security
controls, such as Wi-Fi hotspots at coffee shops or airports. If
your employee access is only based on knowledge factors such as
usernames and passwords, attackers could easily gain full access to
sensitive data.
Hardware-based security tokens or dongles have gained
popularity, particularly at the enterprise level. They generate a
code for the user to enter when prompted, so that only the user
possessing the token can gain access. But these separate, tiny
hardware devices are not without their challenges.
Problems with hardware authentication
Cost — Security tokens cost between
$50-$100 on average for a single device. As a result, these devices
tend to be reserved only for a few high-risk individuals – while
lower-profile employees are left vulnerable.
Lost devices — Hardware tokens can be
lost, stolen, or forgotten, and employees often only notice right
when they need access. Ordering new tokens is inconvenient and
expensive.
UX — Finding the device and entering the
code takes user effort, and can’t be easily used for rapid
provisioning, personnel change, or work with outside
contractors.
Attack risk — Hardware tokens are also
not completely effective against MITM attacks – although they can’t
be directly remotely accessed, a bad actor can trick the user into
entering the code on a fraudulent version of the website/login
page.
There is an innovative, new technology that provides
a strong possession factor[4]
for IAM without extra hardware devices – and it’s in everyone’s
hands already.
Mobile phone possession as an alternative to hardware
tokens
The simpler, easier alternative to buying expensive tokens is to
make use of something your employees already have: their mobile
phone.
Using the advanced cryptographic security of the SIM card,
mobile networks already authenticate customers securely and
invisibly to allow calls and data. SIM-based authentication is
tamper-resistant, real-time verification that works the same as
chips in bank cards.
With no user action or codes to type, SIM-based authentication
makes login simple for your employees, but keeps malicious actors
out. By authenticating with the SIM card itself, rather than just
the mobile number, it’s also possible to check for recent SIM swap
activity, stopping account takeover attacks.
It’s much more cost-effective, deployable at scale, and
universal, meaning every employee, not just a few, has the highest
level of security. And unlike tiny and easily-lost hardware
dongles, the mobile phone is an essential device that employees
will already take with them everywhere.
Now, APIs by tru.ID open up SIM-based network
authentication[5]
for enterprises and businesses to implement frictionless, secure
verification.
Any additional concerns over user privacy are alleviated by the
fact that tru.ID does not process personally identifiable
information between the mobile network and its APIs. It’s purely a
URL-based lookup.
See tru.ID SIM security solution in
action
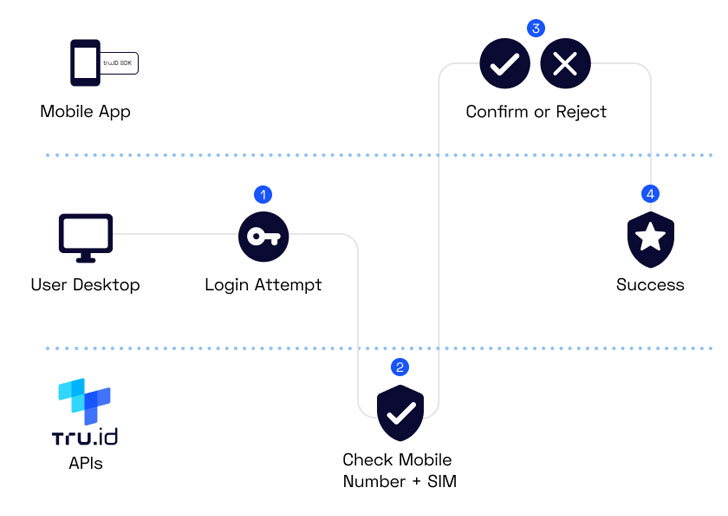
One of the ways to use tru.ID APIs is to implement a
passwordless one-tap registration and login solution to access an
enterprise system using a companion app. Here’s an example
workflow:
tru.ID covers over 2 billion mobile phones in 20 markets and can
be deployed in two ways. It can either be integrated directly into
a company app (if present) with simple REST APIs and SDKs, or it
can be rolled out with a tru.ID companion app that verifies
employee access using their mobile credentials. tru.ID is keen to
hear from the community to discuss case studies – just visit the
website[6] to see it in action in a
demo or start coding.
References
- ^
USD 4.24
million (www.ibm.com) - ^
more
than half (www.ey.com) - ^
Gartner
(www.gartner.com) - ^
an
innovative, new technology that provides a strong possession
factor (tru.id) - ^
APIs by
tru.ID open up SIM-based network authentication
(tru.id) - ^
visit
the website (tru.id)
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/6mFDDnmaZrI/hardware-grade-enterprise.html