A corporate cyber-espionage hacker group has resurfaced after a
seven-month hiatus with new intrusions targeting four companies
this year, including one of the largest wholesale stores in Russia,
while simultaneously making tactical improvements to its toolset in
an attempt to thwart analysis.
“In every attack, the threat actor demonstrates extensive red
teaming skills and the ability to bypass traditional antivirus
detection using their own custom malware,” Group-IB’s Ivan Pisarev
said[1].
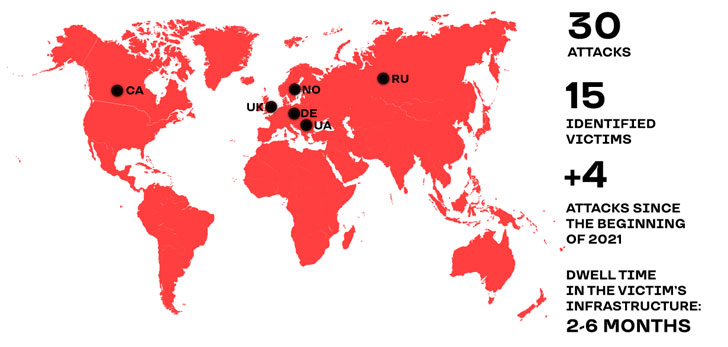
Active since at least November 2018, the Russian-speaking
RedCurl hacking group[2]
has been linked to 30 attacks to date with the goal of corporate
cyber espionage and document theft aimed at 14 organizations
spanning construction, finance, consulting, retail, insurance, and
legal sectors and located in the U.K., Germany, Canada, Norway,
Russia, and Ukraine.
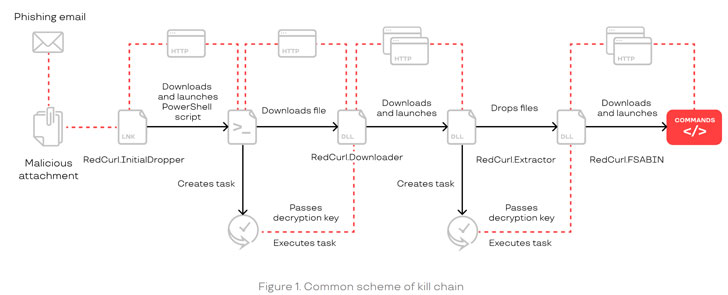
The threat actor uses an array of established hacking tools to
infiltrate its targets and steal internal corporate documentation,
such as staff records, court and legal files, and enterprise email
history, with the collective spending anywhere from two to six
months between initial infection to the time data gets actually
stolen.
RedCurl’s modus operandi marks a departure from other
adversaries, not least because it doesn’t deploy backdoors nor rely
on post-exploitation tools like CobaltStrike and Meterpreter, both
of which are seen as typical methods to remotely control
compromised devices. What’s more, despite maintaining entrenched
access, the group hasn’t been observed conducting attacks that are
motivated by financial gain and involve encrypting victim
infrastructure, or demanding ransoms for stolen data.
Rather, the emphasis appears to be to obtain valuable
information as covertly as possible using a combination of
self-developed and publicly available programs to gain initial
access using social engineering means, perform reconnaissance,
achieve persistence, move laterally, and exfiltrate sensitive
documentation.
“Espionage in cyberspace is a hallmark of state-sponsored
advanced persistent threats,” the researchers said. “In most cases,
such attacks target other states or state-owned companies.
Corporate cyber espionage is still a relatively rare and, in many
ways, unique occurrence. However, it is possible that the group’s
success could lead to a new trend in cybercrime.”
References
- ^
said
(www.group-ib.com) - ^
RedCurl
hacking group (www.group-ib.com)
Read more https://thehackernews.com/2021/11/redcurl-corporate-espionage-hackers.html