Details have emerged about what’s the first Rust-language-based
ransomware strain spotted in the wild that has already amassed
“some victims from different countries” since its launch last
month.
The ransomware, dubbed BlackCat, was disclosed[1]
by MalwareHunterTeam. “Victims can pay with Bitcoin or Monero,” the
researchers said in a series of tweets detailing the
file-encrypting malware. “Also looks they are giving credentials to
intermediaries” for negotiations.
BlackCat, akin to many other variants that have sprung before
it, operates as a ransomware-as-a-service (RaaS), wherein the core
developers recruit affiliates to breach corporate environments and
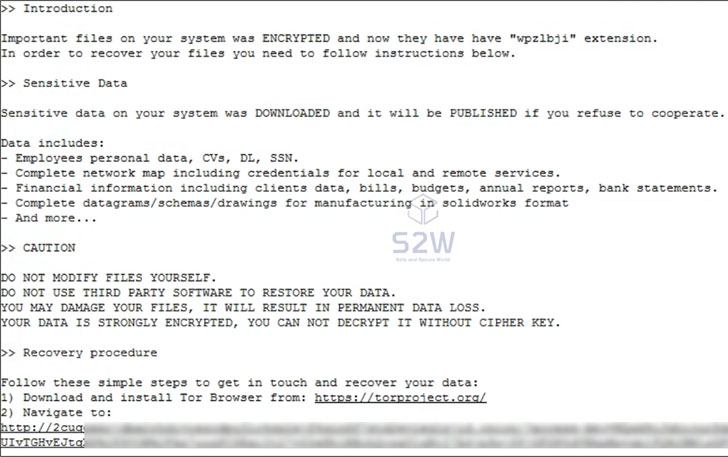
encrypt files, but not before stealing the said documents in a
double extortion scheme to pressure the targets into paying the
requested amount or risk exposure of the stolen data should the
companies refuse to pay up.
Security researcher Michael Gillespie called[2]
it a “very sophisticated ransomware.”
South Korean cybersecurity company S2W, in a separate analysis[3]
of BlackCat, said that the ransomware conducts its malicious
actions by referring to an internal configuration like other RaaS
programs, calling out its similarities with BlackMatter[4], another ransomware that
emerged from the ashes of DarkSide in July only to sunset its
activities in early November.
While it’s typical of ransomware groups to go underground,
regroup, and resurface under a new name, the researchers cautioned
against calling BlackCat a BlackMatter rebrand, citing differences
in the programming language used (Rust vs. C++), the myriad
execution options, and the dark web infrastructure maintained by
the actor.
BlackCat, starting December 4, 2021, has been advertised on
Russian-language underground markets like XSS and Exploit under the
username “alphv” and as “ransom” on the RAMP forum in a bid to
recruit other participants, including penetration testers, and join
what it called “the next generation of ransomware.”
The ransomware actor is also said to be operating five onion
domains, three of which function as the group’s negotiation site,
with the rest categorized as an “Alphv” public leak site and a
private leak site. Only two victims have been identified so far,
suggesting that the nascent ransomware is being actively deployed
against companies in real-world attacks.
“After information about the BlackCat ransomware and Alphv leak
site was revealed on Twitter, they deleted all information of both
two victims and added their warning message on Alphv leak site,”
S2W researchers noted.
The development signals[5]
a growing[6]
trend[7]
where threat actors are adopting lesser-known programming languages
such as Dlang, Go, Nim, and Rust, to bypass security protections,
evade analysis, and hamper reverse engineering efforts.
Rust is also gaining traction for its ability[8]
to achieve high-performance compared to that of languages such as C
and C++, while simultaneously offering memory safety guarantees
that could be leveraged to create malware that’s less susceptible
to exploitation and render them powerless.
References
Read more https://thehackernews.com/2021/12/blackcat-new-rust-based-ransomware.html