A previously undocumented, financially motivated threat group
has been connected to a string of data theft and extortion attacks
on over 40 entities between September and November 2021.
The hacker collective, which goes by the self-proclaimed name
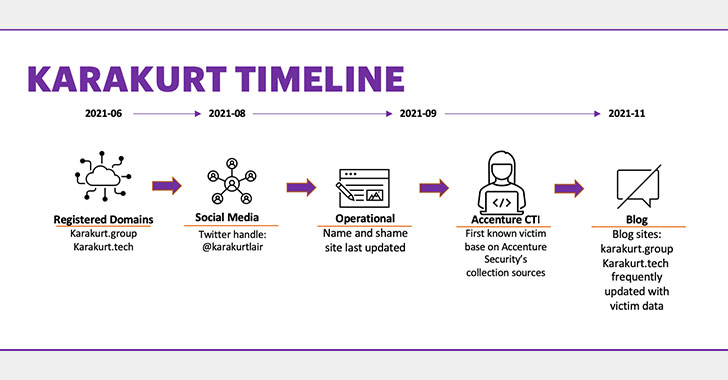
Karakurt[1] and was first identified
in June 2021, is capable of modifying its tactics and techniques to
adapt to the targeted environment, Accenture’s Cyber
Investigations, Forensics and Response (CIFR) team said in a report
published on December 10.
“The threat group is financially motivated, opportunistic in
nature, and so far, appears to target smaller companies or
corporate subsidiaries versus the alternative big game hunting
approach,” the CIFR team said[2]. “Based on intrusion
analysis to date, the threat group focuses solely on data
exfiltration and subsequent extortion, rather than the more
destructive ransomware deployment.”
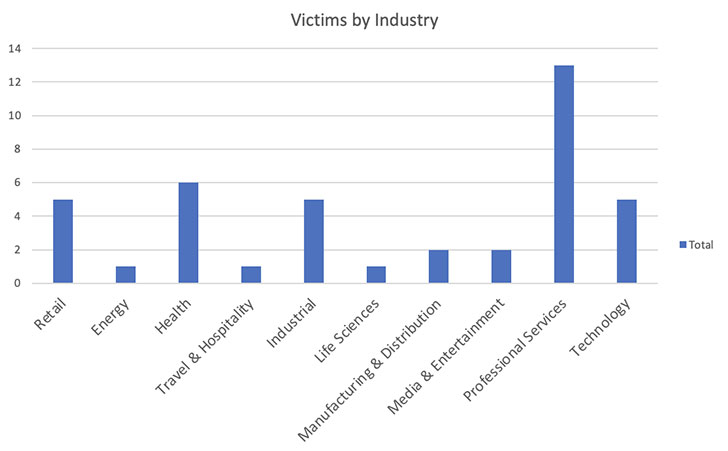
95% of the known victims are based in North America, while the
remaining 5% are in Europe. Professional services, healthcare,
industrial, retail, technology, and entertainment verticals have
been the most targeted.
The goal, the researchers noted, is to avoid drawing attention
to its malicious activities as much as possible by relying on
living off the land (LotL[3]) techniques, wherein the
attackers abuse legitimate software and functions available in a
system such as operating system components or installed software to
move laterally and exfiltrate data, as opposed to deploying
post-exploitation tools like Cobalt Strike.
With ransomware attacks gaining worldwide attention in the wake
of incidents aimed at Colonial Pipeline[4], JBS[5], and Kaseya[6]
as well as the subsequent law enforcement actions that have caused
actors like DarkSide[7], BlackMatter[8], and REvil[9]
to shutter their operations, Karakurt appears to be trying a
different tack.
Rather than deploy ransomware after gaining initial access to
victims’ internet-facing systems via legitimate VPN credentials,
the actors focuses almost exclusively on data exfiltration and
extortion, a move that’s less likely to bring the targets’ business
activities to a standstill and yet enable Karakurt to demand a
“ransom” in return for the stolen information.
Besides encryption data at rest wherever applicable,
organizations are recommended to turn on multiple-factor
authentication (MFA) to authenticate accounts, disable RDP on
external-facing devices, and update the infrastructure to the
latest versions to prevent adversaries from exploiting unpatched
systems with publicly-known vulnerabilities.
References
Read more https://thehackernews.com/2021/12/karakurt-new-emerging-data-theft-and.html