Cyber threats used to be less threatening. While nobody wants
their customers’ credit card numbers stolen in a data breach, or to
see a deranged manifesto plastered over their company website, such
incidents can almost seem quaint compared to ransomware attacks
that bring all of your critical information systems to a dead
halt.
The frequency of these attacks[1] increased more than 150%
in the U.S. last year, and in 2021 their global cost is expected to
reach $20 billion. Effective, comprehensive security training is
essential to mitigating these threats, many of which originate with
low-profile phishing or malware attacks to get a foot in the
door—attacks that can target anyone who works in your
organization.
A company’s employees are the front line of defense against
cyberattacks, and canned training videos and short quizzes are
rarely sufficient to prepare them for this responsibility. The
trouble with good training is that it takes not just expertise but
time and other resources. Companies that are trying to maximize efficiency and minimize
costs[2] sometimes struggle with
delivering security training commensurate with the threats they’re
actually facing.
According to Gartner®, many resource-constrained organizations,
specifically midsize enterprises, struggle to provide even basic
security awareness training to their users, let alone develop a
sophisticated, multichannel, context-specific, and employee-centric
enterprise security awareness program.*
One way to overcome this challenge without hiring professional
services or leaning harder on your existing IT staff is to employ
automation in security training.
What is Training Automation?
Though the word “automation” was not coined until 1947 by Ford
Motor Company to describe the use of automatic devices in the
company’s production lines, today it is one of the most widely used
terms in the tech industry. As a buzzword, “automation” really gets
around. It suggests a solution that will handle your problems
without requiring you to constantly monitor and futz with it, but
in a very technical sense, every software program ever written
involves some element of automation. Say you’ve got a security
training solution that performs some tasks automatically, like
sending out training reminders or test emails on a preset schedule.
Is this training automation?
Not in any meaningful sense. It’s just doing the bare minimum of
what any training software should do, and in that sense is about as
automated—and intelligent—as an alarm clock. True automation needs
to be about more than just putting tasks on a timer.
Adaptive, Hands-On Training Makes All the
Difference
If you’re rolling out an upgrade to your Accounts Payable
software, you can get away with herding everybody into a room,
making them watch a video about it, and handing out a quiz
afterward to make sure they were paying attention. When the purpose
of the training is to prevent data breaches, ransomware attacks,
and other serious threats, this isn’t enough.
The better solution is hands-on training that provides practice
on what to do when an actual cyberattack manifests, and ideally, it
will also take into account the knowledge level and behavioral
profile of the individual receiving the training. Savvy users might
benefit from being educated and tested on subtle, novel approaches,
while some users are just “serial clickers” who might need to
retake Phishing 101 a few times before they unlearn their bad
habits.
Of course, that assumes you know which users are which—and
automation can help you figure that out by engaging in continuous
data analysis as users work their way through the training
program.
Semi-automated solutions can compensate for their shortcomings
by offering lots of manual configuration options, but the time it
takes to set these up correctly reduces the potential gains in
efficiency, especially when things start scaling up. The path to
real optimization always runs through true automation, which is
essential for making training scalable. Only then can you optimize
to achieve efficiency at scale.
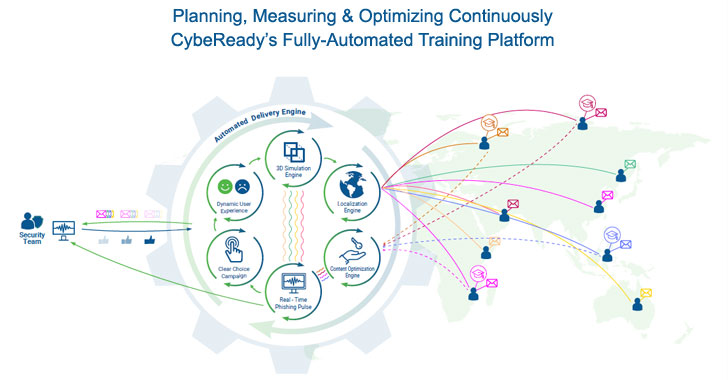
 |
| Image credit: CybeReady |
How to Use Automation in Cybersecurity Training to
Minimize Risk
Every organization has ‘High-Risk Employees’ who jeopardize its
stability. We’ve found that one out of every five people within an
organization may fall under this high-risk category[3]. They might be absolute
rock star employees in every other sense, but for some reason,
they’re just compelled to click the links in weird emails that they
shouldn’t even have opened. Maybe it’s something about the way
they’re wired, but usually, training and education are huge
factors. These employees just lack the awareness of how dangerous
phishing attacks can be and how to identify them reliably.
These are the people who need security training the most, and
they need it to be effective.
CybeReady’s solution for this is a fully-automated platform[4], powered by machine
learning technology, which mitigates the risks from human error
through an educational approach that provides frequent, adaptive,
engaging training on a continuous basis.
For security teams that run lean, the complexity required to run
such a training program is almost impossible to implement without a
truly automated solution that has expert knowledge baked into the
software.
CybeReady works by following a continuous training methodology
that generates enough data to differentiate between users who
occasionally get taken in by phishing emails and those who
habitually click on dangerous links. The latter group requires a
little extra care and attention, and by segmenting trainees
according to their risk level, you can deliver targeted training
that meets the trainee at their precise level of knowledge and
educates them with individualized lessons and simulations that
decrease their risky behaviors.
Here are a few of the principles CybeReady deploys to achieve
measurable training progress:
- Just-in-Time Learning: When an employee clicks
on a malicious email, CybeReady seizes the “golden moment” to push
a pop-up learning page that points out the red flags they
missed. - Timely Reminders: To reinforce the training
and help them outgrow their bad habits, high-risk employees are
sent reminders at strategic intervals. - Adaptive Difficulty Levels: Some simulated
phishing emails are obvious and easy to spot, others are very
sneaky. Evaluations of past performance can be used to select
simulations that will provide just the right level of challenge for
the recipient. - Adjusted Learning Frequency: High-risk
employees receive simulated phishing emails more frequently. When
they get better at identifying them and can be moved back down to a
lower risk category, the frequency is adjusted back to normal
levels.
Final Thoughts
In today’s threat environment, strong cybersecurity is critical.
True automation in your security training systems can significantly
bolster your defenses by efficiently marshaling resources toward
the employees at the highest risk for falling victim to a
cyberattack, without requiring you to hire a professional training
team or force your IT staff to become teachers on the side.
CybeReady’s machine learning solution has the expertise,
analytics, and training methodologies built right in, so when the
hackers and phishers start showing up you can feel confident that
they won’t find any easy targets amongst a staff armed with
knowledge from a state-of-the-art, data-driven, fully adaptive, and
truly automated training program.
Get started with CybeReady’s
training program, tailored for lean security
teams[5]
*Source: Gartner, “Market Guide for Security
Awareness Computer-Based Training[6],” Richard Addiscott,
Claude Mandy, William Candrick, 26 July 2021. GARTNER is a
registered trademark and service mark of Gartner, Inc. and/or its
affiliates in the U.S. and internationally and is used herein with
permission. All rights reserved.
References
- ^
The
frequency of these attacks (www.pbs.org) - ^
maximize
efficiency and minimize costs
(cybeready.com) - ^
this
high-risk category (cybeready.com) - ^
fully-automated platform
(cybeready.com) - ^
Get
started with CybeReady’s training program, tailored for lean
security teams (cybeready.com) - ^
Gartner,
“Market Guide for Security Awareness Computer-Based Training
(www.gartner.com)
Read more https://thehackernews.com/2021/12/the-guide-to-automating-security.html