A cyberespionage threat actor known for targeting a variety of
critical infrastructure sectors in Africa, the Middle East, and the
U.S. has been observed using an upgraded version of a remote access
trojan with information stealing capabilities.
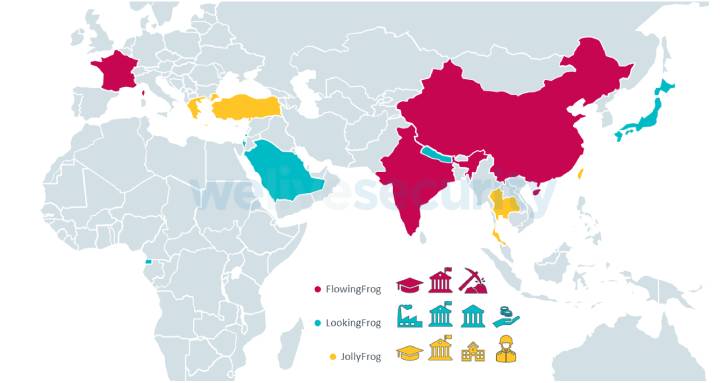
Calling TA410 an umbrella group comprised of three teams
dubbed FlowingFrog, LookingFrog and JollyFrog, Slovak cybersecurity
firm ESET assessed[1]
that “these subgroups operate somewhat independently, but that they
may share intelligence requirements, an access team that runs their
spear-phishing campaigns, and also the team that deploys network
infrastructure.”
TA410 — said to share behavioral and tooling overlaps with
APT10[2]
(aka Stone Panda or TA429) — has a history of targeting U.S-based
organizations in the utilities sector as well as diplomatic
entities in the Middle East and Africa.
Other victims of the hacker collective include a manufacturing
company in Japan, a mining business in India, and a charity in
Israel, in addition to unnamed victims in the education and
military verticals.
TA410 was first documented[3]
by Proofpoint in August 2019 when the threat actor unleashed
phishing campaigns containing macro-laden documents to compromise
utility providers across the U.S. with a modular malware called
LookBack.
Nearly a year later, the group returned with a new backdoor
codenamed FlowCloud, also delivered to U.S. utilities providers,
that Proofpoint described as malware that gives attackers complete
control over infected systems.
“Its remote access trojan (RAT) functionality includes the
ability to access installed applications, the keyboard, mouse,
screen, files, services, and processes with the ability to
exfiltrate information via command-and-control,” the company
noted[4]
in June 2020.
Industrial cybersecurity firm Dragos, which tracks the activity
group under the moniker TALONITE, pointed out the group’s penchant
for blending techniques and tactics in order to ensure a successful
intrusion.
“TALONITE focuses on subverting and taking advantage of trust
with phishing lures focusing on engineering-specific themes and
concepts, malware that abuses otherwise legitimate binaries or
modifies such binaries to include additional functionality, and a
combination of owned and compromised network infrastructure,”
Dragos said[5]
in April 2021.
ESET’s investigation into the hacking crew’s modus operandi and
toolset has shed light on a new version of FlowCloud, which comes
with the ability to record audio using a computer’s microphone,
monitor clipboard events, and control attached camera devices to
take pictures.
Specifically, the audio recording function is designed to be
automatically triggered when sound levels near the compromised
computer cross a 65-decibel threshold.
TA410 is also known to take advantage of both spear-phishing and
vulnerable internet-facing applications such as Microsoft Exchange,
SharePoint, and SQL Servers to gain initial access.
“This indicates to us that their victims are targeted
specifically, with the attackers choosing which entry method has
the best chance of infiltrating the target,” ESET malware
researcher Alexandre Côté Cyr said[6].
Each team within the TA410 umbrella is said to use different
toolsets. While JollyFrog relies on off-the-shelf malware such as
QuasarRAT and Korplug (aka PlugX[7]), LookingFrog uses X4, a
barebones implant, and LookBack.
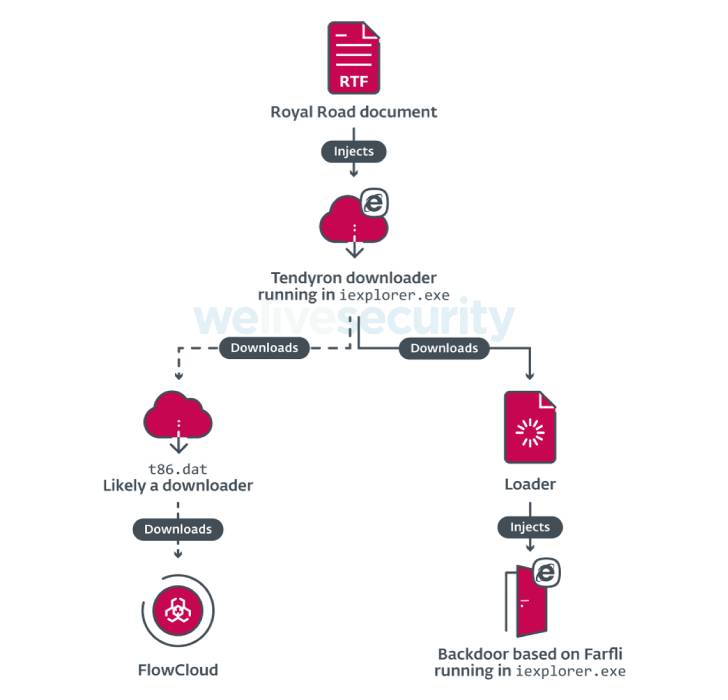
FlowingFrog, in contrast, employs a downloader called Tendyron
that’s delivered by means of the Royal Road RTF weaponizer[8], using it to download
FlowCloud as well as a second backdoor, which is based on Gh0stRAT[9]
(aka Farfli).
“TA410 is a cyberespionage umbrella targeting high-profile
entities such as governments and universities worldwide,” ESET
said. “Even though the JollyFrog team uses generic tools,
FlowingFrog and LookingFrog have access to complex implants such as
FlowCloud and LookBack.”
References
- ^
assessed
(www.welivesecurity.com) - ^
APT10
(malpedia.caad.fkie.fraunhofer.de) - ^
first
documented (www.proofpoint.com) - ^
noted
(www.proofpoint.com) - ^
said
(www.dragos.com) - ^
said
(www.eset.com) - ^
PlugX
(thehackernews.com) - ^
Royal
Road RTF weaponizer (thehackernews.com) - ^
Gh0stRAT
(malpedia.caad.fkie.fraunhofer.de)
Read more https://thehackernews.com/2022/04/experts-detail-3-hacking-teams-working.html