Cybersecurity researchers have dissected the inner workings of
an information-stealing malware called Saintstealer that’s
designed to siphon credentials and system information.
“After execution, the stealer extracts username, passwords,
credit card details, etc.,” Cyble researchers said[1]
in an analysis last week. “The stealer also steals data from
various locations across the system and compresses it in a
password-protected ZIP file.”
A 32-bit C# .NET-based executable with the name “saintgang.exe,”
Saintstealer is equipped with anti-analysis checks, opting to
terminate itself if it’s running either in a sandboxed or virtual
environment.
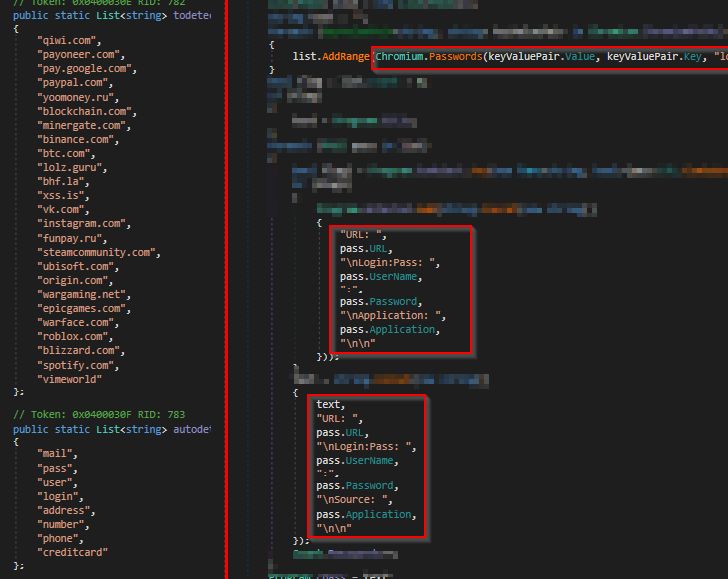
The malware can capture a wide range of information that ranges
from taking screenshots to gathering passwords, cookies, and
autofill data stored in Chromium-based browsers such as Google
Chrome, Opera, Edge, Brave, Vivaldi, and Yandex, among others.
It can also steal Discord multi-factor authentication tokens,
files with .txt, .doc, and .docx extensions as well as extract
information from VimeWorld, Telegram, and VPN apps like NordVPN,
OpenVPN, and ProtonVPN.
Besides transmitting the compressed information to a Telegram
channel, the metadata related to the exfiltrated data is sent to a
remote command-and-control (C2) server.
What’s more, the IP address linked to the C2 domain —
141.8.197[.]42 — is tied to multiple stealer families such as
Nixscare stealer, BloodyStealer, QuasarRAT, Predator stealer, and
EchelonStealer.
“Information stealers can be harmful to individuals as well as
large organizations,” the researchers said. “If even
unsophisticated stealers like Saintstealer gain infrastructural
access, it could have devastating effects on the
cyberinfrastructure of the targeted organization.”
The disclosure comes as a new infostealer named Prynt Stealer[2]
has surfaced in the wild that can also perform keylogging
operations and financial theft using a clipper module.
“It can target 30+ Chromium-based browsers, 5+ Firefox-based
browsers, and a range of VPN, FTP, messaging, and gaming apps,”
Cyble noted last month.
Sold for $100 for a one-month license and $900 for a lifetime
subscription, the malware joins a long list of other recently
advertised stealers, including Jester[3], BlackGuard[4], Mars Stealer[5], META[6], FFDroider, and Lightning Stealer[7].
References
- ^
said
(blog.cyble.com) - ^
Prynt
Stealer (blog.cyble.com) - ^
Jester
(thehackernews.com) - ^
BlackGuard
(thehackernews.com) - ^
Mars
Stealer (thehackernews.com) - ^
META
(isc.sans.edu) - ^
FFDroider, and Lightning Stealer
(thehackernews.com)
Read more https://thehackernews.com/2022/05/experts-detail-saintstealer-and-prynt.html