More than 200 Android apps masquerading as fitness, photo
editing, and puzzle apps have been observed distributing spyware
called Facestealer to siphon user credentials and other
valuable information.
“Similar to Joker[1], another piece of mobile
malware, Facestealer changes its code frequently, thus spawning
many variants,” Trend Micro analysts Cifer Fang, Ford Quin, and
Zhengyu Dong said[2]
in a new report. “Since its discovery, the spyware has continuously
beleaguered Google Play.”
Facestealer, first documented[3]
by Doctor Web in July 2021, refers to a group of fraudulent apps
that invade the official app marketplace for Android with the goal
of plundering sensitive data such as Facebook login
credentials.
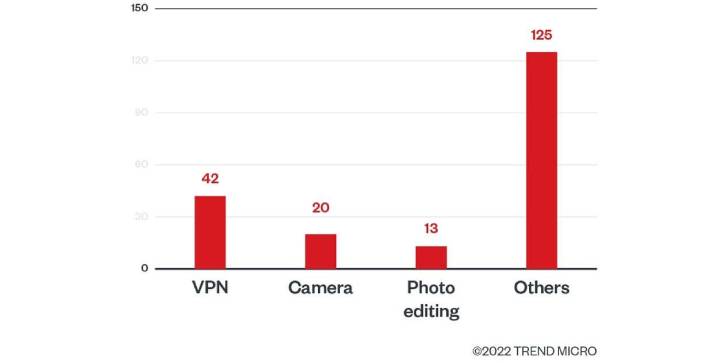
Of the 200 apps, 42 are VPN services, followed by a camera (20)
and photo editing applications (13). In addition to harvesting
credentials, the apps are also designed to collect Facebook cookies
and personally identifiable information associated with a victim’s
account.
Additionally, Trend Micro disclosed that it uncovered over 40
rogue cryptocurrency miner apps that target users interested in
virtual coins with malware designed to trick users into watching
ads and paying for subscription services.
Some of the fake crypto apps, such as Cryptomining Farm Your own
Coin, take it one step further by also attempting to steal private
keys and mnemonic phrases[4]
(or seed phrases) that are used to recover access to a
cryptocurrency wallet.
To avoid falling victim to such scam apps, it’s recommended that
users check negative reviews, verify the legitimacy of the
developers, and avoid downloading apps from third-party app
stores.
New study analyzes malicious Android apps installed in the
wild
The findings come as researchers from NortonLifeLock and Boston
University published[5]
what they called the “largest on-device study” of potentially
harmful apps (PHAs[6]) on Android-based on 8.8
million PHAs installed on over 11.7 million devices between 2019
and 2020.
“PHAs persist on Google Play for 77 days on average and 34 days
on third-party marketplaces,” the study noted, pointing out the
delay between when PHAs are identified and when they are removed,
adding 3,553 apps exhibit inter-market migration after being taken
down.
On top of that, the research also shows that PHAs linger for a
much longer period on average when users switch devices and
automatically install the apps when restoring from a backup.
As many as 14,000 PHAs are said to have been transferred to
35,500 new Samsung devices by using the Samsung Smart Switch mobile
app, with the apps lasting on the phones for a period of
approximately 93 days.
“The Android security model severely limits what mobile security
products can do when detecting a malicious app, allowing PHAs to
persist for many days on victim devices,” the academics said. “The
current warning system employed by mobile security programs is not
effective in convincing users to promptly uninstall PHAs.”
References
Read more https://thehackernews.com/2022/05/over-200-apps-on-play-store-caught.html