The notorious Conti ransomware gang, which last month staged an
attack on Costa Rican administrative systems, has threatened to
“overthrow” the new government of the country.
“We are determined to overthrow the government by means of a
cyber attack, we have already shown you all the strength and
power,” the group said on its official website. “We have our
insiders in your government. We are also working on gaining access
to your other systems, you have no other options but to pay
us.”
In a further attempt to increase pressure, the Russian-speaking
cybercrime syndicate has raised its ransom demand to $20 million in
return for a decryption key to unlock their systems.
Another message posted on its dark web portal over the weekend
issued a warning stating it will delete the decryption keys in a
week, a move that would make it impossible for Costa Rica to
recover access to the files encrypted by the ransomware.
“I appeal to every resident of Costa Rica, go to your government
and organize rallies so that they would pay us as soon as possible
if your current government cannot stabilize the situation? Maybe
it’s worth changing it?,” the message read.
The devastating attack, which took place[1]
on April 19, has caused the new government to declare a state of
emergency, while the group has leaked troves of data stolen from
the infected systems prior to encryption.
Conti attributed the intrusion to an affiliate actor dubbed
“UNC1756,” mimicking the moniker threat intelligence firm Mandiant
assigns to uncategorized threat groups.
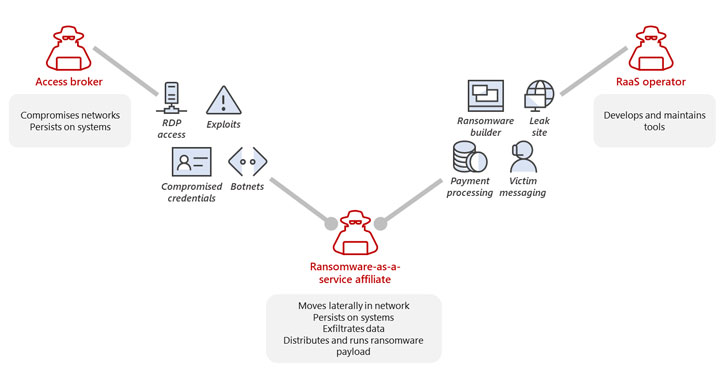
Affiliates are hacking groups who rent access to
already-developed ransomware tools to orchestrate intrusions into
corporate networks as part of what’s called a
ransomware-as-a-service (RaaS[2]) gig economy, and then
split the earnings with the operators.
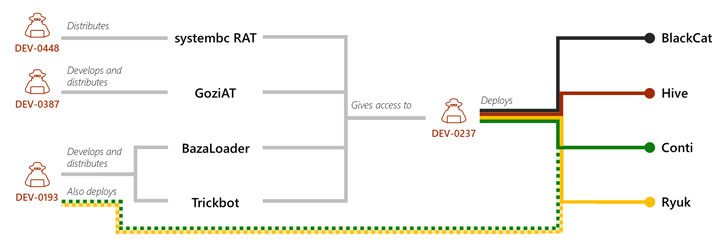
Linked to a threat actor known as Gold Ulrick (aka Grim Spider
or UNC1878), Conti has continued to target entities[3] across the world despite
suffering a massive data leak[4]
of its own earlier this year in the wake of its public support to
Russia in the country’s ongoing war against Ukraine.
Microsoft’s security division, which tracks the cybercriminal
group under the cluster DEV-0193, called Conti the “most prolific
ransomware-associated cybercriminal activity group active
today.”
“DEV-0193’s actions and use of the cybercriminal gig economy
means they often add new members[5]
and projects and utilize contractors to perform various parts of
their intrusions,” Microsoft Threat Intelligence Center (MSTIC)
said[6].
“As other malware operations have shut down for various reasons,
including legal actions, DEV-0193 has hired developers from these
groups. Most notable are the acquisitions of developers from
Emotet[7], Qakbot[8], and IcedID[9], bringing them to the
DEV-0193 umbrella.”
The interminable attacks have also led the U.S. State Department
to announce[10] rewards of up to $10
million for any information leading to the identification of key
individuals who are part of the cybercrime cartel.
References
- ^
took
place (twitter.com) - ^
RaaS
(www.crowdstrike.com) - ^
continued to target entities
(thehackernews.com) - ^
massive
data leak (thehackernews.com) - ^
add new
members (thehackernews.com) - ^
said
(www.microsoft.com) - ^
Emotet
(thehackernews.com) - ^
Qakbot
(thehackernews.com) - ^
IcedID
(thehackernews.com) - ^
announce
(thehackernews.com)
Read more https://thehackernews.com/2022/05/russian-conti-ransomware-gang-threatens.html