A case of software supply chain attack has been observed in the
Rust programming language’s crate registry[1]
that leveraged typosquatting techniques to publish a rogue library
containing malware.
Cybersecurity firm SentinelOne dubbed the attack “CrateDepression[2].”
Typosquatting attacks take place[3]
when an adversary mimics the name of a popular package on a public
registry in hopes that developers will accidentally download the
malicious package instead of the legitimate library.
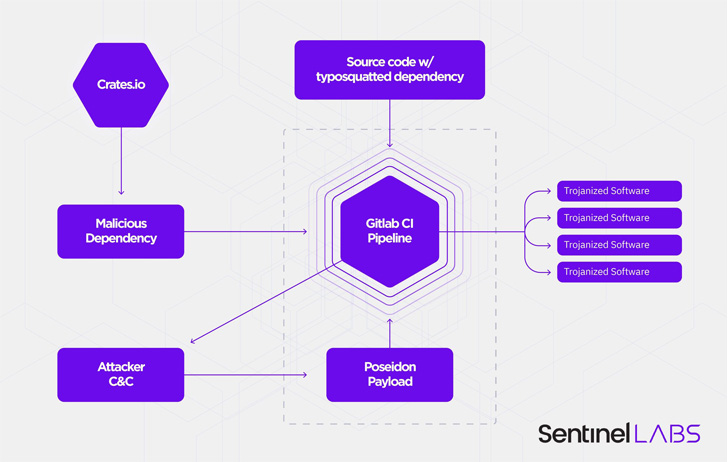
In this case, the crate in question is “rustdecimal,” a
typosquat of the real “rust_decimal[4]” package that’s been
downloaded over 3.5 million times to date. The package was flagged[5]
earlier this month on May 3 by Askar Safin, a Moscow-based
developer.
According to an advisory[6]
published by the Rust maintainers, the crate is said to have been
first pushed on March 25, 2022, attracting fewer than 500 downloads
before it was permanently removed from the repository.
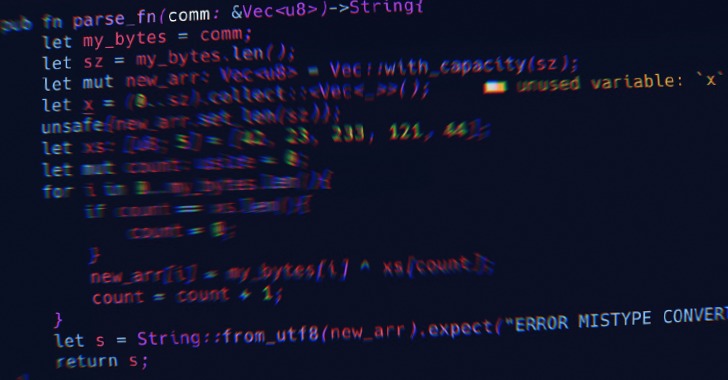
Like prior typosquatting attacks of this kind, the misspelled
library replicates the entire functionality of the original library
while also introducing a malicious function that’s designed to
retrieve a Golang binary hosted on a remote URL.
Specifically, the new function checks if the “GITLAB_CI[7]” environment variable is
set, suggesting a “singular interest in GitLab continuous
integration (CI) pipelines,” SentinelOne
noted.
The payload, which is equipped to capture screenshots, log
keystrokes, and download arbitrary files, is capable of running on
both Linux and macOS, but not Windows systems. The ultimate goals
of the campaign are unknown as yet.
While typosquatting attacks have been previously documented
against NPM (JavaScript), PyPi (Python), and RubyGems (Ruby), the
development marks an uncommon instance where such an incident has
been discovered in the Rust ecosystem.
“Software supply-chain attacks have gone from a rare occurrence
to a highly desirable approach for attackers to ‘fish with
dynamite’ in an attempt to infect entire user populations at once,”
SentinelOne researchers said.
“In the case of CrateDepression, the targeting interest in cloud
software build environments suggests that the attackers could
attempt to leverage these infections for larger scale supply-chain
attacks.”
References
- ^
crate
registry (doc.rust-lang.org) - ^
CrateDepression
(www.sentinelone.com) - ^
take
place (snyk.io) - ^
rust_decimal
(crates.io) - ^
flagged
(github.com) - ^
advisory
(blog.rust-lang.org) - ^
GITLAB_CI
(docs.gitlab.com)
Read more https://thehackernews.com/2022/05/researchers-uncover-rust-supply-chain.html