Malicious actors can gain unauthorized access to users’ online
accounts via a new technique called “account pre-hijacking,” new
research has found.
The attack takes aim at the account creation process that’s
ubiquitous in websites and other online platforms, enabling an
adversary to perform a set of actions before an unsuspecting victim
creates an account in a target service.
The study was led by independent security researcher Avinash
Sudhodanan in collaboration with Andrew Paverd of the Microsoft
Security Response Center (MSRC).
Pre-hijacking banks on the prerequisite that an attacker is
already in possession of a unique identifier associated with a
victim, such as an email address or phone number, which can be
obtained either from the target’s social media accounts or
credential dumps circulating on the web.
The attacks can then play out in five different ways, including
the use of the same email address during account creation by both
the adversary and the victim, potentially granting the two parties
concurrent access to the account.
“If the attacker can create an account at a target service using
the victim’s email address before the victim creates an account,
the attacker could then use various techniques to put the account
into a pre-hijacked state,” the researchers said[1].
“After the victim has recovered access and started using the
account, the attacker could regain access and take over the
account.” The five types of pre-hijacking attacks are below –
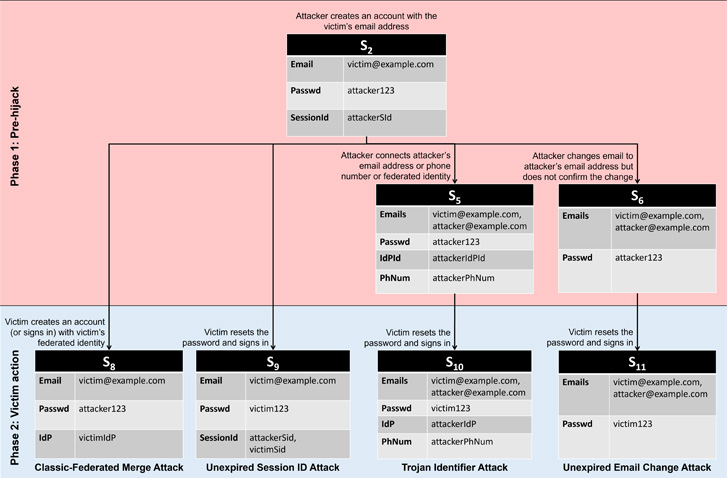
- Classic-Federated Merge Attack, in which two
accounts created using classic and federated identity[2]
routes with the same email address allow the victim and the
attacker to access to the same account.
- Unexpired Session Identifier Attack, in which
the attacker creates an account using the victim’s email address
and maintains a long-running active session. When the user recovers
the account using the same email address, the attacker continues to
maintain access because the password reset did not terminate the
attacker’s session.
- Trojan Identifier Attack, in which the
attacker creates an account using the victim’s email address and
then adds a trojan identifier, say, a secondary email address or a
phone number under their control. Thus when the actual user
recovers access following a password reset, the attacker can use
the trojan identifier to regain access to the account.
- Unexpired Email Change Attack, in which the
attacker creates an account using the victim’s email address and
proceeds to change the email address to one under their control.
When the service sends a verification URL to the new email address,
the attacker waits for the victim to recover and start using the
account before completing the change-of-email process to seize
control of the account.
- Non-Verifying Identity Provider (IdP) Attack,
in which the attacker creates an account with the target service
using a non-verifying IdP. If the victim creates an account using
the classic registration method with the same email address, it
enables the attacker to gain access to the account.
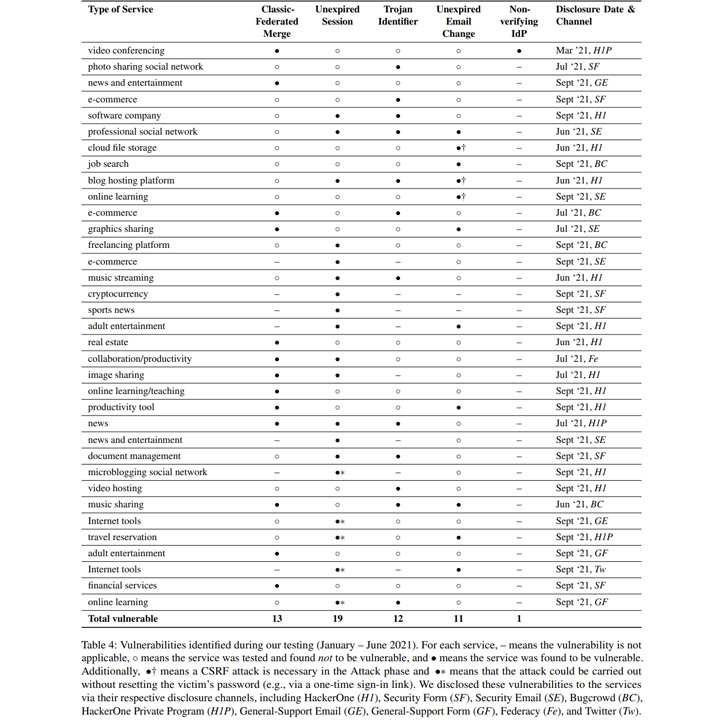
In an empirical evaluation of 75 of the most popular websites
from Alexa, 56 pre-hijacking vulnerabilities were identified on 35
services. This includes 13 Classic-Federated Merge, 19 Unexpired
Session Identifier, 12 Trojan Identifier, 11 Unexpired Email
Change, and one Non-Verifying IdP attacks –
- Dropbox – Unexpired Email Change Attack
- Instagram – Trojan Identifier Attack
- LinkedIn – Unexpired Session and Trojan Identifier Attacks
- WordPress.com – Unexpired Session and Unexpired Email Change
Attacks, and - Zoom – Classic-Federated Merge and Non-verifying IdP
Attacks
“The root cause of all of the attacks […] is a failure to
verify ownership of the claimed identifier,” the researchers
said.
“Although many services do perform this type of verification,
they often do so asynchronously, allowing the user to use certain
features of the account before the identifier has been verified.
Although this might improve usability (reduces user friction during
sign up), it leaves the user vulnerable to pre-hijacking
attacks.”
While implementing strict identifier verification in services is
crucial to mitigating pre-hijacking attacks, it’s recommended that
users secure their accounts with multi-factor authentication
(MFA).
“Correctly implemented MFA will prevent the attacker from
authenticating to a pre-hijacked account after the victim starts
using this account,” the researchers noted. “The service must also
invalidate any sessions created prior to the activation of MFA to
prevent the Unexpired Session attack.”
On top of that, online services are also advised to periodically
delete unverified accounts, enforce a low window to confirm a
change of email address, and invalidate sessions during password
resets for a defense in-depth approach to account management.
“When a service merges an account created via the classic route
with one created via the federated route (or vice-versa), the
service must ensure that the user currently controls both
accounts,” Sudhodanan and Paverd said.
References
- ^
said
(msrc-blog.microsoft.com) - ^
federated identity
(en.wikipedia.org)
Read more https://thehackernews.com/2022/05/learn-how-hackers-can-hijack-your.html