Microsoft on Monday published guidance for a newly discovered
zero-day security flaw[1]
in its Office productivity suite that could be exploited to achieve
code execution on affected systems.
The weakness, now assigned the identifier CVE-2022-30190[2], is rated 7.8 out of 10
for severity on the CVSS vulnerability scoring system. Microsoft
Office versions Office 2013, Office 2016, Office 2019, and Office
2021, as well as Professional Plus editions, are impacted.
“To help protect customers, we’ve published CVE-2022-30190 and
additional guidance here[3],” a Microsoft
spokesperson told The Hacker News in an emailed statement.
The Follina[4]
vulnerability, which came to light late last week, involved a
real-world exploit that leveraged the shortcoming in a weaponized
Word document to execute arbitrary PowerShell code by making use of
the “ms-msdt:” URI scheme. The sample was uploaded to VirusTotal
from Belarus.
But first signs of exploitation of the flaw date back to April
12, 2022, when a second sample was uploaded to the malware
database. This artifact is believed to have targeted a user in
Russia with a malicious Word document (“приглашение на интервью.doc[5]“) that masqueraded as an
interview invitation with Sputnik Radio.
“A remote code execution vulnerability exists when MSDT is
called using the URL protocol from a calling application such as
Word,” Microsoft said in an advisory for CVE-2022-30190.
“An attacker who successfully exploits this vulnerability can
run arbitrary code with the privileges of the calling application.
The attacker can then install programs, view, change, or delete
data, or create new accounts in the context allowed by the user’s
rights.”
The tech giant credited crazyman, a member of the Shadow Chaser
Group[6], for reporting the flaw
on April 12, coinciding with the discovery of the in-the-wild
exploit targeting Russian users, indicating the company had been
already aware of the vulnerability.
Indeed, according to screenshots[7]
shared by the researcher on Twitter, Microsoft closed the report on
April 21, 2022 stating “the issue has been fixed,” while also
dismissing the flaw as “not a security issue” since it requires a
passkey provided by a support technician when starting the
diagnostic tool.
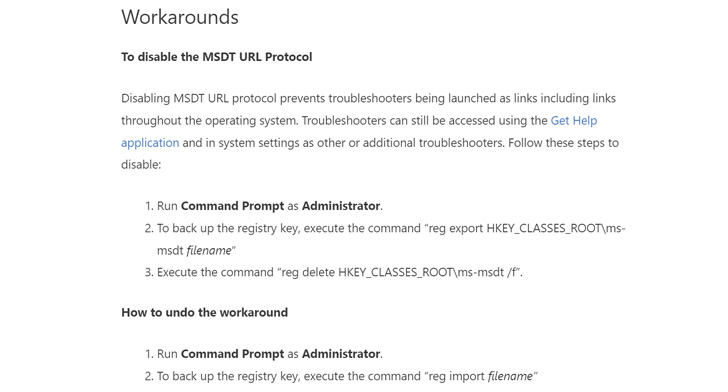
Besides releasing detection rules for Microsoft Defender for
Endpoint, the Redmond-based company has offered workarounds in its
guidance to disable the MSDT URL protocol via a Windows Registry
modification.
“If the calling application is a Microsoft Office application,
by default, Microsoft Office opens documents from the internet in
Protected View or Application Guard for Office, both of which
prevent the current attack,” Microsoft said.
This is not the first time Microsoft Office protocol schemes
like “ms-msdt:” have come under the scanner for their potential
misuse. Earlier this January, Germany security company SySS
disclosed[8]
how it’s possible to open files directly via specially crafted URLs
such as “ms-excel:ofv|u|https://192.168.1.10/poc[.]xls.”
References
- ^
zero-day
security flaw (thehackernews.com) - ^
CVE-2022-30190
(msrc.microsoft.com) - ^
here
(msrc-blog.microsoft.com) - ^
Follina
(doublepulsar.com) - ^
приглашение на интервью.doc
(www.virustotal.com) - ^
Shadow
Chaser Group (twitter.com) - ^
screenshots
(twitter.com) - ^
disclosed
(blog.syss.com)
Read more https://thehackernews.com/2022/05/microsoft-releases-workarounds-for.html