A “dangerous piece of functionality” has been discovered in
Microsoft 365 suite that could be potentially abused by a malicious
actor to ransom files stored on SharePoint and OneDrive and launch
attacks on cloud infrastructure.
The cloud ransomware attack makes it possible to launch
file-encrypting malware to “encrypt files stored on SharePoint and
OneDrive in a way that makes them unrecoverable without dedicated
backups or a decryption key from the attacker,” Proofpoint said[1]
in a report published today.
The infection sequence can be carried out using a combination of
Microsoft APIs, command-line interface (CLI) scripts, and
PowerShell scripts, the enterprise security firm added.
The attack, at its core, hinges on a Microsoft 365 feature
called AutoSave that creates copies of older file versions as and
when users make edits to a file stored on OneDrive or SharePoint
Online.
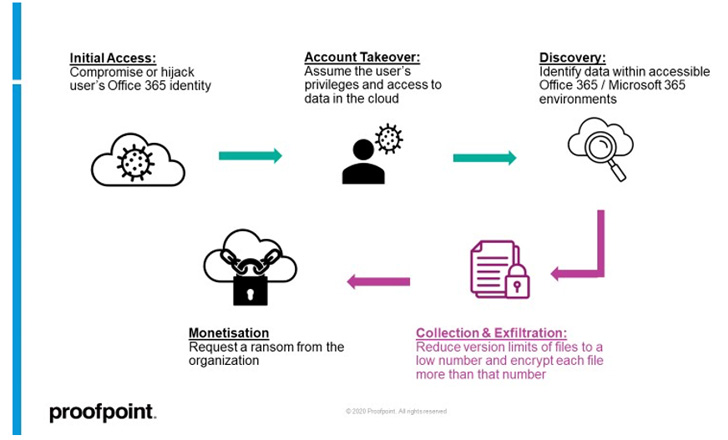
It commences with gaining unauthorized access to a target user’s
SharePoint Online or OneDrive account, followed by abusing the
access to exfiltrate and encrypt files. The three most common
avenues to obtain the initial foothold involve directly breaching
the account via phishing or brute-force attacks, tricking a user
into authorizing a rogue third-party OAuth application, or taking
over the web session of a logged-in user.
But where this attack stands apart from traditional endpoint
ransomware activity is that the encryption phase requires locking
each file on SharePoint Online or OneDrive more than the permitted versioning limit[2].
Microsoft elaborates[3]
the versioning behavior in its documentation as follows –
Some organizations allow unlimited versions of files and
others apply limitations. You might discover, after checking in the
latest version of a file, that an old version is missing. If your
most recent version is 101.0 and you notice that there is no longer
a version 1.0, it means that the administrator configured the
library to allow only 100 major versions of a file. The addition of
the 101st version causes the first version to be deleted. Only
versions 2.0 through 101.0 remain. Similarly, if a 102nd version is
added, only versions 3.0 through 102.0 remain.
By leveraging the access to the account, an attacker can either
create too many versions of a file or alternatively reduce the
version limit of a document library to a lower such as “1” and then
proceed to encrypt each file twice.
“Now all original (pre-attacker) versions of the files are lost,
leaving only the encrypted versions of each file in the cloud
account,” the researchers explained. “At this point, the attacker
can ask for a ransom from the organization.”
Microsoft, in response to the findings, pointed out that older
versions of files can be potentially recovered and restored for an
additional 14 days with the assistance of Microsoft Support, a
process that Proofpoint found to be unsuccessful.
We have reached out to the tech giant for further comment, and
we will update the story if we hear back.
To mitigate such attacks, it’s recommended to enforce a strong
password policy, mandate multi-factor authentication (MFA), and
prevent large-scale data downloads to unmanaged devices.
“Files stored in a hybrid state on both endpoint and cloud such
as through cloud sync folders will reduce the impact of this novel
risk as the attacker will not have access to the local/endpoint
files,” the researchers said. “To perform a full ransom flow, the
attacker will have to compromise the endpoint and the cloud account
to access the endpoint and cloud-stored files.”
References
- ^
said
(www.proofpoint.com) - ^
permitted versioning limit
(support.microsoft.com) - ^
elaborates
(support.microsoft.com)
Read more https://thehackernews.com/2022/06/a-microsoft-office-365-feature-could.html