A newly observed phishing campaign is leveraging the recently
disclosed Follina security vulnerability to distribute a previously
undocumented backdoor on Windows systems.
“Rozena is a backdoor malware that is capable of injecting a
remote shell connection back to the attacker’s machine,” Fortinet
FortiGuard Labs researcher Cara Lin said[1]
in a report this week.
Tracked as CVE-2022-30190[2], the now-patched
Microsoft Windows Support Diagnostic Tool (MSDT) remote code
execution vulnerability has come under heavy exploitation in recent
weeks ever since it came to light in late May 2022.
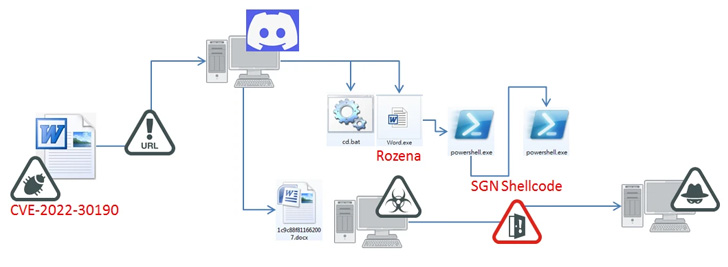
The starting point for the latest attack chain observed by
Fortinet is a weaponized Office document[3]
that, when opened, connects to a Discord CDN URL[4]
to retrieve an HTML file (“index.htm[5]“) that, in turn, invokes
the diagnostic utility using a PowerShell command to download
next-stage payloads from the same CDN attachment space.
This includes the Rozena implant (“Word.exe”) and a batch file
(“cd.bat”) that’s designed to terminate MSDT processes, establish
the backdoor’s persistence by means of Windows Registry
modification, and download a harmless Word document as a decoy.
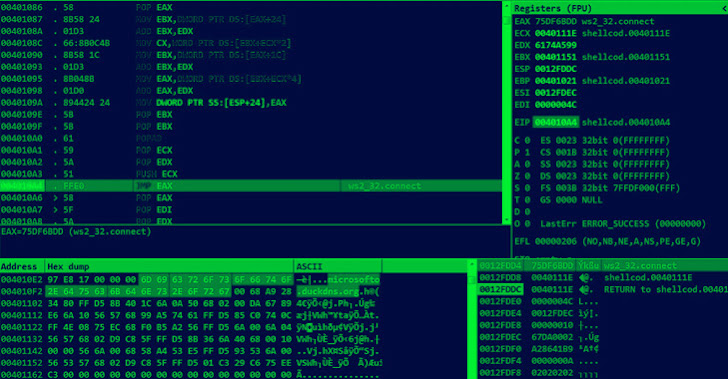
The malware’s core function is to inject shellcode that launches
a reverse shell to the attacker’s host
(“microsofto.duckdns[.]org”), ultimately allowing the attacker to
take control of the system required to monitor and capture
information, while also maintaining a backdoor to the compromised
system.
The exploitation of the Follina flaw to distribute malware
through malicious Word documents comes as social engineering
attacks relying[6]
on Microsoft Excel, Windows shortcut (LNK), and ISO image files as
droppers to deploy malware such as Emotet[7], QBot[8], IcedID[9], and Bumblebee[10] to a victim’s
device.
The droppers are said to be distributed through emails that
contain directly the dropper or a password-protected ZIP as an
attachment, an HTML file that extracts the dropper when opened, or
a link to download the dropper in the body of the email.
While attacks spotted in early April prominently featured Excel
files with XLM macros, Microsoft’s decision to block macros by
default around the same time is said to have forced the threat
actors to pivot to alternative methods like HTML smuggling[11] as well as .LNK and
.ISO files.
Last month, Cyble disclosed details of a malware tool called
Quantum[12] that’s being sold on
underground forums so as to equip cybercriminal actors with
capabilities to build malicious .LNK and .ISO files.
It’s worth noting that macros[13] have been a
tried-and-tested attack vector for adversaries looking to drop
ransomware and other malware on Windows systems, whether it be
through phishing emails or other means.
Microsoft has since temporarily paused[14] its plans to disable
Office macros in files downloaded from the internet, with the
company telling The Hacker News that it’s taking the time to make
“additional changes to enhance usability.”
References
- ^
said
(www.fortinet.com) - ^
CVE-2022-30190
(thehackernews.com) - ^
Office
document (www.virustotal.com) - ^
Discord
CDN URL (thehackernews.com) - ^
index.htm
(www.virustotal.com) - ^
relying
(www.fortinet.com) - ^
Emotet
(thehackernews.com) - ^
QBot
(thehackernews.com) - ^
IcedID
(thehackernews.com) - ^
Bumblebee
(thehackernews.com) - ^
HTML
smuggling (thehackernews.com) - ^
Quantum
(thehackernews.com) - ^
macros
(docs.microsoft.com) - ^
temporarily paused
(thehackernews.com)
Read more https://thehackernews.com/2022/07/hackers-exploiting-follina-bug-to.html