Nation-state hacking groups aligned with China, Iran, North
Korea, and Turkey have been targeting journalists to conduct
espionage and spread malware as part of a series of campaigns since
early 2021.
“Most commonly, phishing attacks targeting journalists are used
for espionage or to gain key insights into the inner workings of
another government, company, or other area of state-designated
import,” Proofpoint said[1]
in a report shared with The Hacker News.
The ultimate goal of the intrusions, the enterprise security
firm said, is to gain a competitive intelligence edge or spread
disinformation and propaganda.
Proofpoint said it identified two Chinese hacking groups, TA412
(aka Zirconium[2]
or Judgment Panda) and TA459[3], targeting media
personnel with malicious emails containing web beacons and
weaponized documents respectively that were used to amass
information about the recipients’ network environments and drop
Chinoxy[4]
malware.
In a similar vein, the North Korea-affiliated Lazarus Group (aka
TA404) targeted an unnamed U.S.-based media organization with a job
offer-themed phishing lure following its critical coverage of
supreme leader Kim Jong Un, once again reflective of the threat
actor’s continued[5]
reliance[6]
on the technique to further its objectives.
U.S.-based journalists and media have also come under assault
from a pro-Turkey hacking group known as TA482, which has been
linked to a credential harvesting attack designed to siphon Twitter
credentials via bogus landing pages.
“The motivations behind these campaigns […] could include
using the compromised accounts to target a journalist’s social
media contacts, use the accounts for defacement, or to spread
propaganda,” the researchers theorized.
Lastly, Proofpoint highlighted attempts on the part of multiple
Iranian APT actors such as Charming Kitten[7]
(aka TA453) by masquerading as journalists to entice academics and
policy experts into clicking on malicious links that redirect the
targets to credential harvesting domains.
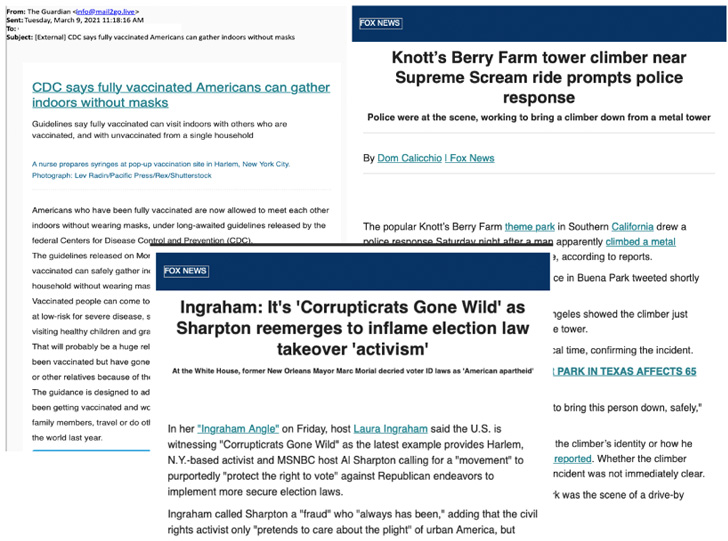
Also joining this list is a threat actor named Tortoiseshell[8]
(aka TA456 or Imperial Kitten) that’s said to have “routinely”
impersonated media organizations like Fox News and the Guardian to
send newsletter-themed emails containing web beacons.
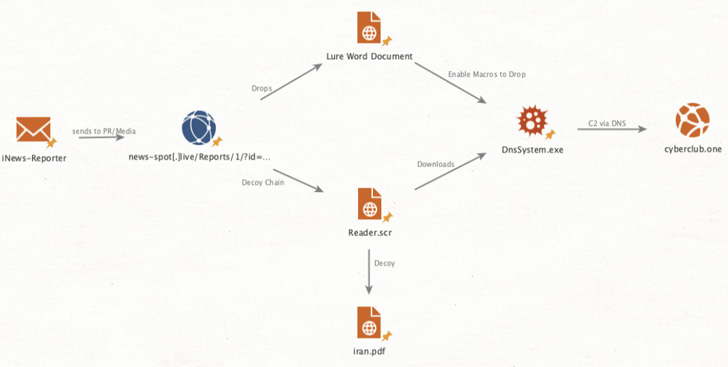
The third Iran-aligned adversary to follow an identical approach
is TA457, which posed as an “iNews Reporter” to deliver a .NET-based DNS Backdoor[9] to public relations
personnel for companies in the U.S., Israel, and Saudi Arabia.
The fact that journalists and media entities have become the
locus of attacks is underscored by their ability to offer “unique
access and information,” making them lucrative targets for
intelligence gathering efforts.
“A well-timed, successful attack on a journalist’s email account
could provide insights into sensitive, budding stories and source
identification,” the researchers said. “A compromised account could
be used to spread disinformation or pro-state propaganda, provide
disinformation during times of war or pandemic, or be used to
influence a politically charged atmosphere.”
References
- ^
said
(www.proofpoint.com) - ^
Zirconium
(thehackernews.com) - ^
TA459
(attack.mitre.org) - ^
Chinoxy
(malpedia.caad.fkie.fraunhofer.de) - ^
continued
(thehackernews.com) - ^
reliance
(thehackernews.com) - ^
Charming
Kitten (thehackernews.com) - ^
Tortoiseshell
(thehackernews.com) - ^
a
.NET-based DNS Backdoor (thehackernews.com)
Read more https://thehackernews.com/2022/07/state-backed-hackers-targeting.html