A new, large-scale phishing campaign has been observed using
adversary-in-the-middle (AitM) techniques to get around security
protections and compromise enterprise email accounts.
“It uses an adversary-in-the-middle (AitM) attack technique
capable of bypassing multi-factor authentication,” Zscaler
researchers Sudeep Singh and Jagadeeswar Ramanukolanu said[1]
in a Tuesday report. “The campaign is specifically designed to
reach end users in enterprises that use Microsoft’s email
services.”
Prominent targets include fintech, lending, insurance, energy,
manufacturing, and federal credit union verticals located in the
U.S., U.K., New Zealand, and Australia.
This is not the first time such a phishing attack has come to
light. Last month, Microsoft disclosed[2]
that over 10,000 organizations had been targeted since September
2021 by means of AitM techniques to breach accounts secured with
multi-factor authentication (MFA).
The ongoing campaign, effective June 2022, commences with an
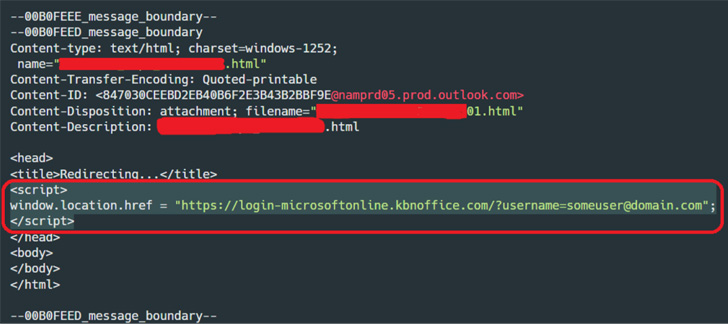
invoice-themed email sent to targets containing an HTML attachment,
which includes a phishing URL embedded within it.
Opening the attachment via a web browser redirects the email
recipient to the phishing page that masquerades as a login page for
Microsoft Office, but not before fingerprinting the compromised
machine to determine whether the victim is actually the intended
target.
AitM phishing attacks go beyond the traditional phishing
approaches designed to plunder credentials from unwitting users,
particularly in scenarios where MFA is enabled – a security barrier
that prevents the attacker from logging into the account with only
the stolen credentials.
To circumvent this, the rogue landing page developed using a
phishing kit functions as a proxy that captures and relays all the
communication between the client (i.e., victim) and the email
server.
“The kits intercept the HTML content received from the Microsoft
servers, and before relaying it back to the victim, the content is
manipulated by the kit in various ways as needed, to make sure the
phishing process works,” the researchers said.
This also entails replacing all the links to the Microsoft
domains with equivalent links to the phishing domain so as to
ensure that the back-and-forth remains intact with the fraudulent
website throughout the session.
Zscaler said it observed the attacker manually logging into the
account eight minutes after the credential theft, following it up
by reading emails and checking the user’s profile information.
What’s more, in some instances, the hacked email inboxes are
subsequently used to send additional phishing emails as part of the
same campaign to conduct business email compromise (BEC) scams.
“Even though security features such as multi-factor
authentication (MFA) add an extra layer of security, they should
not be considered as a silver bullet to protect against phishing
attacks,” the researchers noted.
“With the use of advanced phishing kits (AiTM) and clever
evasion techniques, threat actors can bypass both traditional as
well as advanced security solutions.”
Read more https://thehackernews.com/2022/08/researchers-warns-of-large-scale-aitm.html