Customer engagement platform Twilio on Monday disclosed that a
“sophisticated” threat actor gained “unauthorized access” using an
SMS-based phishing campaign aimed at its staff to gain information
on a “limited number” of accounts.
The social-engineering attack was bent on stealing employee
credentials, the company said, calling the as-yet-unidentified
adversary “well-organized” and “methodical in their actions.” The
incident came to light on August 4.
“This broad based attack against our employee base succeeded in
fooling some employees into providing their credentials,” it
said[1]
in a notice. “The attackers then used the stolen credentials to
gain access to some of our internal systems, where they were able
to access certain customer data.”
The communications giant has 268,000 active customer
accounts[2], and counts companies
like Airbnb, Box, Dell, DoorDash, eBay, Glassdoor, Lyft,
Salesforce, Stripe, Twitter, Uber, VMware, Yelp, and Zendesk among
its clients. It also owns the popular two-factor authentication
(2FA) service Authy[3].
Twilio, which is still continuing its investigation into the
hack, noted it’s working directly with customers who were impacted.
It didn’t disclose the scale of the attack, the number of employee
accounts that were compromised, or what types of data may have been
accessed.
Phishing schemes, both leveraging email and SMS, are known to
lean on aggressive scare tactics to coerce victims into handing
over their sensitive information. This is no exception.
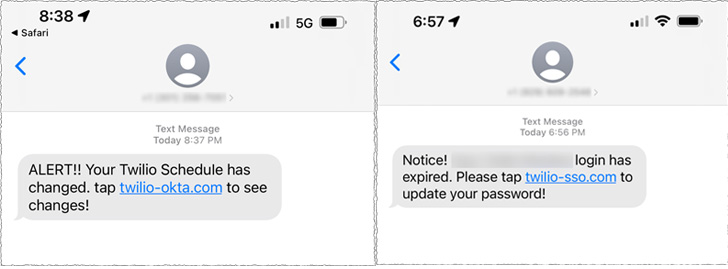
The SMS messages are said to have been sent to both current and
former employees masquerading as coming from its IT department,
luring them with password expiry notifications to click on
malicious links.
The URLs included words such as “Twilio,” “Okta,” and “SSO[4]” (short for single
sign-on) to increase the chance of success and redirected the
victims to a phony website that impersonated the company’s sign-in
page. It’s not immediately clear if the breached accounts were
secured by 2FA protections.
Twilio said the messages originated from U.S. carrier networks
and that it worked with the telecom service and hosting providers
to shut down the scheme and the attack infrastructure used in the
campaign. The takedown efforts, however, have been offset by the
attackers migrating to other carriers and hosting providers.
“Additionally, the threat actors seemed to have sophisticated
abilities to match employee names from sources with their phone
numbers,” it noted.
The San Francisco-based firm has since revoked access to the
compromised employee accounts to mitigate the attack, adding it’s
examining additional technical safeguards as a preventive
measure.
The disclosure arrives as spear-phishing continues to be a major
threat faced by enterprises. Last month, it emerged that the $620
million Axie Infinity hack was the consequence of one of its former
employees getting tricked by a fraudulent job offer[5] on LinkedIn.
References
- ^
said
(www.twilio.com) - ^
268,000 active customer accounts
(www.twilio.com) - ^
Authy
(www.twilio.com) - ^
SSO
(en.wikipedia.org) - ^
tricked
by a fraudulent job offer
(thehackernews.com)
Read more https://thehackernews.com/2022/08/twilio-suffers-data-breach-after.html