The first ever incident possibly involving the ransomware family
known as Maui occurred on April 15, 2021, aimed at an unnamed
Japanese housing company.
The disclosure from Kaspersky arrives a month after U.S.
cybersecurity and intelligence agencies issued an advisory[1]
about the use of the ransomware strain by North Korean
government-backed hackers to target the healthcare sector since at
least May 2021.
Much of the data about its modus operandi came from incident
response activities and industry analysis of a Maui sample that
revealed a lack of “several key features” typically associated with
ransomware-as-a-service (RaaS) operations.
Not only is Maui designed to be manually executed by a remote
actor via a command-line interface, it’s also notable for not
including a ransom note to provide recovery instructions.
Subsequently, the Justice Department announced[2]
the seizure of $500,000 worth of Bitcoin that were extorted from
several organizations, including two healthcare facilities in the
U.S. states of Kansas and Colorado, by using the ransomware
strain.
While these attacks have been pinned on North Korean advanced
persistent threat groups, the Russian cybersecurity firm has linked
the cybercrime with low to medium confidence to a Lazarus subgroup
known as Andariel[3], also known as Operation
Troy, Silent Chollima, and Stonefly.
“Approximately ten hours prior to deploying Maui to the initial
target system [on April 15], the group deployed a variant of the
well-known Dtrack malware to the target, preceded by 3proxy[4] months earlier,”
Kaspersky researchers Kurt Baumgartner and Seongsu Park said[5].
Dtrack, also called Valefor and Preft, is a remote access trojan
used by the Stonefly group in its espionage attacks to exfiltrate
sensitive information.
It’s worth pointing out that the backdoor, alongside 3proxy, was
deployed by the threat actor against an engineering firm that works
in the energy and military sectors in February 2022 by exploiting
the Log4Shell vulnerability[6].
“Stonefly specializes in mounting highly selective targeted
attacks against targets that could yield intelligence to assist
strategically important sectors such as energy, aerospace, and
military equipment,” Symantec, a division of Broadcom Software,
said[7]
in April.
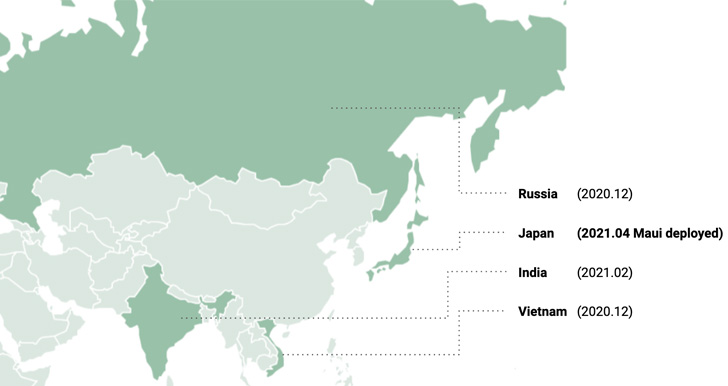
Furthermore, Kaspersky said that the Dtrack sample used in the
Japanese Maui incident was also used to breach multiple victims in
India, Vietnam, and Russia from December 2021 to February 2021.
“Our research suggests that the actor is rather opportunistic
and could compromise any company around the world, regardless of
their line of business, as long as it enjoys good financial
standing,” the researchers said.
This isn’t Andariel’s first tryst with ransomware as a means to
reap monetary gains[8]
for the sanctions-hit nation. In June 2021, a South Korean entity
was revealed[9]
to have been infected by file-encrypting malware following an
elaborate multi-stage infection procedure that commenced with a
weaponized Word document.
Then last month, Microsoft disclosed that an emerging threat
cluster associated with Andariel has been using a ransomware strain
known as H0lyGh0st[10] in cyberattacks
targeting small businesses since September 2021.
References
- ^
advisory
(thehackernews.com) - ^
announced
(thehackernews.com) - ^
Andariel
(malpedia.caad.fkie.fraunhofer.de) - ^
3proxy
(github.com) - ^
said
(securelist.com) - ^
Log4Shell vulnerability
(thehackernews.com) - ^
said
(symantec-enterprise-blogs.security.com) - ^
reap
monetary gains (thehackernews.com) - ^
revealed
(thehackernews.com) - ^
H0lyGh0st
(thehackernews.com)
Read more https://thehackernews.com/2022/08/experts-uncover-details-on-maui.html