Password security is only as strong as the password itself.
Unfortunately, we are often reminded of the danger of weak, reused,
and compromised passwords with major cybersecurity breaches that
start with stolen credentials. For example, in May 2022, the
popular wedding planning site, Zola, was the victim of a
significant cybersecurity breach where hackers used an attack known
as credential stuffing. It resulted in fraudulent activity
tied to customer accounts. Let’s look at the Zola breach and why it
emphasizes the need for organizations to bolster their password
security and protect against various types of password attacks.
What happened with the Zola attack?
Instead of going after Zola’s core business-critical
infrastructure, hackers went after customer accounts with the May
attack. Attackers used an age-old technique called credential
stuffing to compromise several Zola customer accounts. With
access to the compromised accounts, they attempted to purchase gift
vouchers which they could then use.
A Zola spokesperson mentioned that around 3,000 accounts[1], or around .1 % of Zola
accounts, were compromised. Users saw hundreds of dollars worth of
gift cards or monetary gifts taken from their accounts. Hackers
even changed the email associated with users’ Zola accounts in many
cases, preventing them from logging in. Compromised Zola accounts
were quickly placed for sale on the dark web. Other users reported
fraudulent charges on credit cards associated with Zola
accounts.
Emily Forrest, Zola Director of Communications, mentioned the
following in a statement[2]
regarding the compromise:
“These hackers likely gained access to those set of exposed
credentials on third-party sites and used them to try to log in to
Zola and take bad actions. Our team jumped into action immediately
to ensure that all couples and guests on Zola are protected…We
understand the disruption and stress that this caused some of our
couples, but we are happy to report that all attempted fraudulent
cash fund transfer attempts were blocked. All cash funds have been
restored.”
As part of their remediation of the attack, Zola, in addition to
forcing users to reset their account passwords, temporarily
disabled mobile apps connected to the platform. They have since
reactivated the mobile app platforms. However, even though Zola
allows connecting bank account information to Zola accounts,
they still do not require multi-factor
authentication[3]
as part of their security provisions.
What went wrong from a security perspective with the Zola
attack?
Hindsight is often 20/20 when it comes to post-mortem analysis
of cybersecurity breaches. However, there were many things that
could have been done and can be done moving forward to prevent
attacks like the Zola hack from being carried out.
More companies now require multi-factor authentication to be
enabled on your account to take advantage of their services.
Arguably, any service geared toward collecting money into an
account or that allows connecting a bank account or credit card
should require multi-factor. With multi-factor enabled, even if an
attacker has legitimate credentials, such as a username and
password, with an additional factor required, they still do not
have everything needed to authenticate and log in.
The attack on Zola helps underscore that companies must also
monitor accounts for suspicious activities. For example, watching
for suspicious geolocations, the number of logins from a single
source, or other metrics can help identify and remediate nefarious
activities.
What is credential stuffing?
Credential stuffing is a hacking technique that has been around
a long while and plays upon the weakness of password reuse
among end-users. It is defined as[4]
the automated injection of stolen username and password
pairs. What does this mean? It is human nature to reuse passwords
across multiple sites, services, and applications. This technique
makes it easier to remember logins across various platforms.
Hackers use this logic to defeat password authentication used
across most platforms. If they compromise or find leaked
credentials associated with a user/email/password combination in
one platform, they can try the same credentials across multiple
platforms.
It can be effective even if they don’t know the user/email
address has an account associated. For example, suppose they can
access several compromised credential sets (usernames, passwords).
In that case, they will likely find valid user accounts across
multiple services where users have used the same username/password
combination.
Note the following alarming statistics[5]
related to credential reuse:
- Some 50% of IT professionals admitted to reusing passwords on
work accounts
There was a surprisingly higher percentage of IT workers reusing
credentials than non-privileged users (39% comparatively)
- In a study that spanned three months, Microsoft found that some
44 million of its users had used the same password on more than one
account - In a 2019 Google study, they found that 13% of people reuse the
same password across all accounts, 52% percent use the same one for
multiple online accounts, and only 35% use a different password for
every account
Another alarming scenario that organizations must consider is
that end-users may use the same passwords for their corporate
Active Directory environments as they do for their personal
accounts. While businesses can’t control and enforce password
policies for end-users personal accounts, monitoring for breached
passwords and password reuse across their corporate Active
Directory infrastructure is crucial.
Protecting Active Directory against breached passwords and
password reuse
On-premises Active Directory Domain Services (AD DS) does not
have built-in protection against breached passwords or password
reuse. For example, suppose every single account in Active
Directory has the same password, and the password meets the
configured password policy. In that case, there is no notification
or way to prevent this with native Active Directory Password Policy
functionality.
Moreover, many organizations are federating Active Directory
Domain Services on-premises with Single Sign-On (SSO) cloud
solutions. Unfortunately, it means all of the weak passwords,
breached passwords, and passwords reused across your organization
are now federated for use with cloud services, further weakening
your security posture.
Built-in Active Directory Password Policies can’t protect you
against:
- Incremental passwords
- Leetspeak passwords
- Easily guessed but “complex” passwords
- Breached passwords
- Passwords associated with your business or industry
Bolster Active Directory password security with Specops
With the shortcomings of built-in capabilities provided by
Active Directory Domain Services (AD DS), organizations need to
bolster their Active Directory password security using a
third-party solution. Specops Password Policy[6]
is a powerful solution that provides businesses with the tools and
capabilities required to increase their password security and
overall cybersecurity stance.
Specops Password Policy seamlessly integrates with existing
Active Directory Password Policies and adds missing password
security features to help protect your organization from many
attacks, including credential stuffing. Note the following key
features provided by Specops Password Policy:
- You can create custom dictionary lists to block words common to
your organization - Prevent the use of more than 2 billion compromised passwords
with Specops Breached Password Protection - Find and remove compromised passwords in your environment
- Users get informative messaging from Specops at failed password
changes, reducing calls to the helpdesk - Real-time, dynamic feedback at password change with the Specops
Authentication client - Length-based password expiration with customizable email
notifications - Block user names, display names, specific words, consecutive
characters, incremental passwords, reusing part of a password - Granular, GPO-driven targeting for any GPO level, computer,
user, or group population - Passphrase support
- Over 25 languages supported
- Use Regular Expressions for more granular password
policies
Organizations can start protecting their user’s passwords with
Breached Password Protection with just a few clicks in the Specops
Password Policy configuration settings. With the continuously
check for leaked passwords and force users to change them
setting, you can leverage Specop Password Policy’s enhanced
honeypot intelligence for the most late-breaking breached
passwords available.
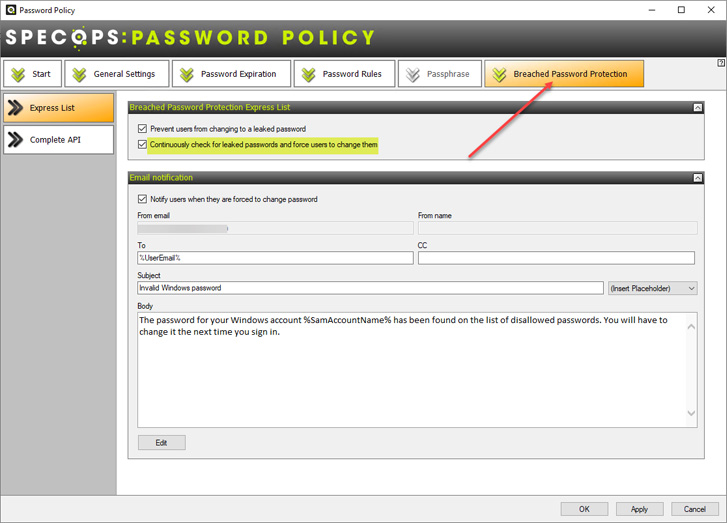 |
| Configuring Specops Password Policy Breached Password Protection |
Specops provides the tools needed to combat password risks such
as reused passwords easily.
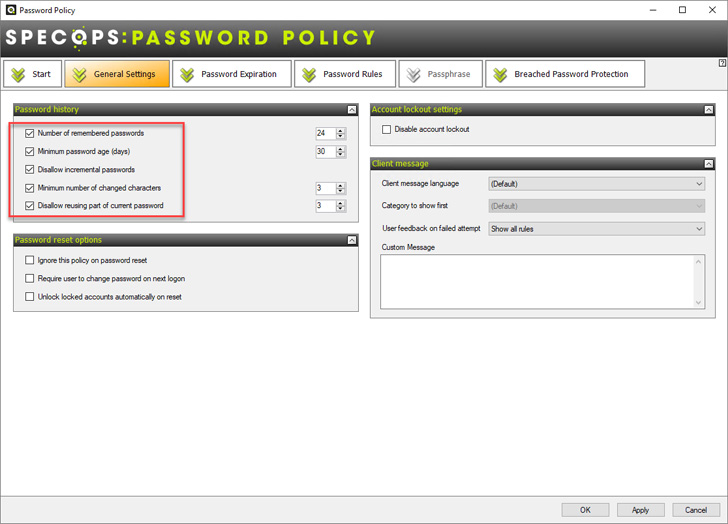 |
| Preventing incremental passwords and requiring a minimum number of changes to an existing password |
Wrapping Up
The Zola hack helps to emphasize the importance of preventing
users from reusing passwords in business-critical environments. It
leads to credential stuffing, password guessing, breached
passwords, and many other types of password attacks. Specops
Password Policy is a powerful tool allowing organizations to
effectively prevent password reuse, incremental passwords, and a
minimum number of changes to existing passwords at the next
password change.
Learn more about Specops Password Policy and
see how it can help your business bolster your password security
strategy with a free trial[7].
References
- ^
around
3,000 accounts (www.nydailynews.com) - ^
in a
statement (therecord.media) - ^
they
still do not require multi-factor authentication
(www.techradar.com) - ^
defined
as (owasp.org) - ^
alarming
statistics (www.comparitech.com) - ^
Specops
Password Policy (specopssoft.com) - ^
Learn
more about Specops Password Policy and see how it can help your
business bolster your password security strategy with a free
trial (specopssoft.com)
Read more https://thehackernews.com/2022/08/what-zola-hack-can-teach-us-about.html
