The malware loader known as Bumblebee is being increasingly
co-opted by threat actors associated with BazarLoader, TrickBot,
and IcedID in their campaigns to breach target networks for
post-exploitation activities.
“Bumblebee operators conduct intensive reconnaissance activities
and redirect the output of executed commands to files for
exfiltration,” Cybereason researchers Meroujan Antonyan and Alon
Laufer said[1]
in a technical write-up.
Bumblebee[2]
first came to light in March 2022 when Google’s Threat Analysis
Group (TAG) unmasked the activities of an initial access broker
dubbed Exotic Lily[3]
with ties to the TrickBot[4]
and the larger Conti[5]
collectives.
Typically delivered via initial access acquired through
spear-phishing campaigns, the modus operandi has since been tweaked
by eschewing macro-laced documents in favor of ISO and LNK files,
primarily in response to Microsoft’s decision to block macros by default[6].
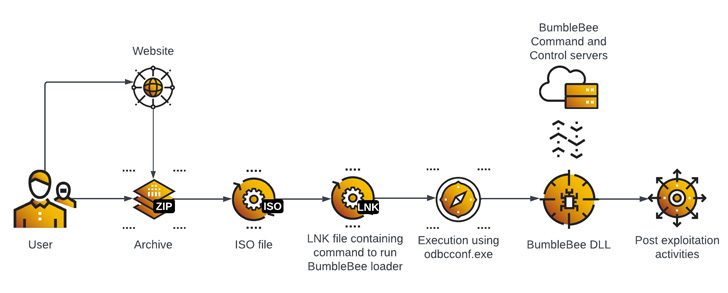
“Distribution of the malware is done by phishing emails with an
attachment or a link to a malicious archive containing Bumblebee,”
the researchers said. “The initial execution relies on the end-user
execution which has to extract the archive, mount an ISO image
file, and click a Windows shortcut (LNK) file.”
The LNK file, for its part, contains the command to launch the
Bumblebee loader, which is then used as a conduit for next-stage
actions such as persistence, privilege escalation, reconnaissance,
and credential theft.
Also employed during the attack is the Cobalt Strike adversary
simulation framework upon gaining elevated privileges on infected
endpoints, enabling the threat actor to laterally move across the
network. Persistence is achieved by deploying AnyDesk remote
desktop software.
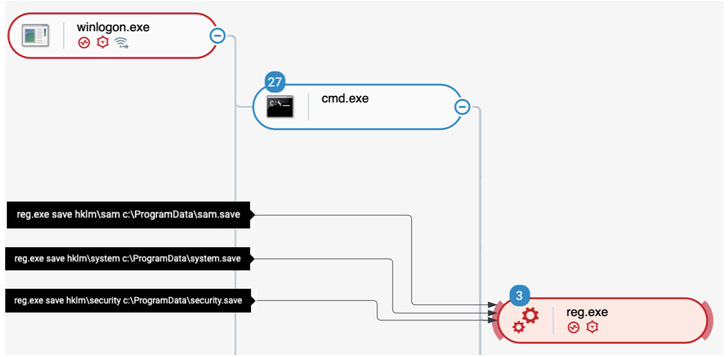
In the incident analyzed by Cybereason, the stolen credentials
of a highly privileged user were subsequently utilized to seize
control of the Active Directory[7], not to mention create a
local user account for data exfiltration.
“The time it took between initial access and Active Directory
compromise was less than two days,” the cybersecurity firm said.
“Attacks involving Bumblebee must be treated as critical, […] and
this loader is known for ransomware delivery.”
References
- ^
said
(www.cybereason.com) - ^
Bumblebee
(thehackernews.com) - ^
Exotic
Lily (thehackernews.com) - ^
TrickBot
(thehackernews.com) - ^
Conti
(thehackernews.com) - ^
block
macros by default (thehackernews.com) - ^
Active
Directory (docs.microsoft.com)
Read more https://thehackernews.com/2022/08/hackers-using-bumblebee-loader-to.html