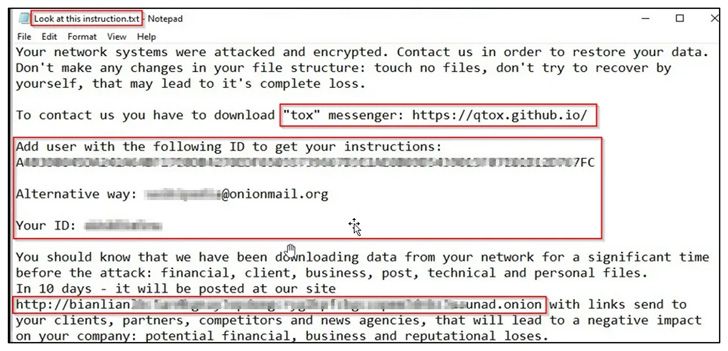
The operators of the emerging cross-platform BianLian ransomware
have increased their command-and-control (C2) infrastructure this
month, a development that alludes to an increase in the group’s
operational tempo.
BianLian, written in the Go programming language, was first
discovered in mid-July 2022 and has claimed 15 victim organizations
as of September 1, cybersecurity firm [redacted] said in a report[1]
shared with The Hacker News.
It’s worth noting that the double extortion ransomware family
has no connection to an Android banking trojan[2]
of the same name, which targets mobile banking and cryptocurrency
apps to siphon sensitive information.
Initial access to victim networks is achieved via successful
exploitation of the ProxyShell[3]
Microsoft Exchange Server flaws, leveraging it to either drop a web
shell or an ngrok payload for follow-on activities.
“BianLian has also targeted SonicWall VPN devices for
exploitation, another common target for ransomware groups,”
[redacted] researchers Ben Armstrong, Lauren Pearce, Brad Pittack,
and Danny Quist said[4].
Unlike another new Golang malware called Agenda[5], the BianLian actors
exhibit dwell times of up to six weeks from the time of initial
access and the actual encryption event, a duration that’s well
above the median intruder dwell time[6] of 15 days reported in
2021.
Besides leveraging living-off-the-land (LotL) techniques for
network profiling and lateral movement, the group is also known to
deploy a custom implant as an alternative means for maintaining
persistent access to the network.
The main goal of the backdoor, per [redacted], is to retrieve
arbitrary payloads from a remote server, load it into memory, and
then execute them.
BianLian, similar to Agenda, is capable of booting servers in
Windows safe mode to execute its file-encrypting malware while
simultaneously remaining undetected by security solutions installed
on the system.
Other steps taken to defeat security barriers include deleting
shadow copies, purging backups, and running its Golang encryptor
module via Windows Remote Management (WinRM[7]) and PowerShell
scripts.
The earliest known C2 server associated with BianLian is said to
have appeared online in December 2021. But the infrastructure has
since witnessed a “troubling explosion” to surpass 30 active IP
addresses.
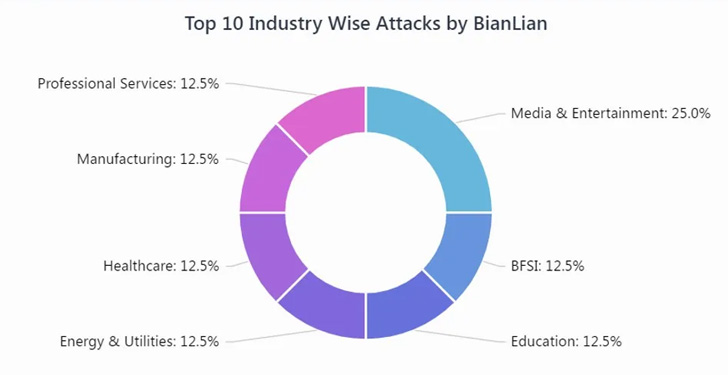
According to Cyble, which detailed[8]
the modus operandi of the ransomware earlier this month, targeted
companies span several industry sectors such as media, banking,
energy, manufacturing, education, healthcare, and professional
services. A majority of the companies are based in North America,
the U.K., and Australia.
BianLian is yet another indication of cybercriminals’ dedicated
efforts to continue hopping tactics so as to avoid detection. It
also adds to a growing number of threats using Go as the
foundational language, enabling adversaries to make swift changes
in a single codebase that can then be compiled for multiple
platforms.
“BianLian have shown themselves to be adept with the Living of
the Land (LOL) methodology to move laterally, adjusting their
operations based on the capabilities and defenses they encountered
in the network,” the researchers said.
References
Read more https://thehackernews.com/2022/09/researchers-detail-emerging-cross.html
.jpg)