A vulnerable anti-cheat driver for the Genshin Impact video game
has been leveraged by a cybercrime actor to disable antivirus
programs to facilitate the deployment of ransomware, according to
findings from Trend Micro.
The ransomware infection, which was triggered in the last week
of July 2022, banked on the fact that the driver in question
(“mhyprot2.sys”) is signed with a valid certificate, thereby making
it possible to circumvent privileges and terminate services
associated with endpoint protection applications.
Genshin Impact is a popular action role-playing game that was
developed and published by Shanghai-based developer miHoYo in
September 2020.
The driver used in the attack chain is said to have been built
in August 2020, with the existence of the flaw in the module
discussed[1]
after the release of the game, and leading to exploits[2]
demonstrating[3]
the ability to kill any arbitrary process and escalate to kernel
mode.
The idea, in a nutshell, is to use the legitimate device driver
module with valid code signing to escalate privileges from user
mode to kernel mode, reaffirming how adversaries are constantly
looking for different ways to stealthily deploy malware.
“The threat actor aimed to deploy ransomware within the victim’s
device and then spread the infection,” incident response analysts
Ryan Soliven and Hitomi Kimura said[4].
“Organizations and security teams should be careful because of
several factors: the ease of obtaining the mhyprot2.sys module, the
versatility of the driver in terms of bypassing privileges, and the
existence of well-made proofs of concept (PoCs).”
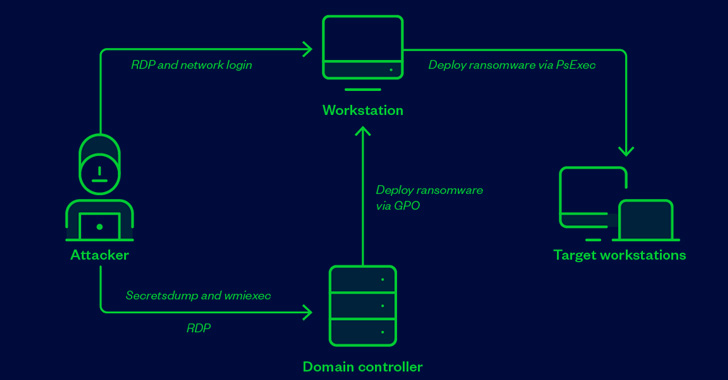
In the incident analyzed by Trend Micro, a compromised endpoint
belonging to an unnamed entity was used as a conduit to connect to
the domain controller via remote desktop protocol (RDP) and
transfer to it a Windows installer posing as AVG Internet Security,
which dropped and executed, among other files, the vulnerable
driver.
The goal, the researchers said, was to mass-deploy the
ransomware to using the domain controller via a batch file that
installs the driver, kills antivirus services, and launches the
ransomware payload.
Trend Micro pointed out that the game “does not need to be
installed on a victim’s device for this to work,” meaning threat
actors can simply install the anti-cheat driver as a precursor to
ransomware deployment.
We have reached out to miHoYo for comment, and we will update
the story if we hear back.
“It is still rare to find a module with code signing as a device
driver that can be abused,” the researchers said. “This module is
very easy to obtain and will be available to everyone until it is
erased from existence. It could remain for a long time as a useful
utility for bypassing privileges.”
“Certificate revocation and antivirus detection might help to
discourage the abuse, but there are no solutions at this time
because it is a legitimate module.”
References
Read more https://thehackernews.com/2022/09/ransomware-attackers-abuse-genshin.html