A new phishing-as-a-service (PhaaS) toolkit dubbed EvilProxy is
being advertised on the criminal underground as a means for threat
actors to bypass two-factor authentication (2FA) protections
employed against online services.
“EvilProxy actors are using reverse proxy and cookie injection
methods to bypass 2FA authentication – proxifying victim’s
session,” Resecurity researchers said[1]
in a Monday write-up.
The platform generates phishing links that are nothing but
cloned pages designed to compromise user accounts associated with
Apple iCloud, Facebook, GoDaddy, GitHub, Google, Dropbox,
Instagram, Microsoft, NPM, PyPI, RubyGems, Twitter, Yahoo, and
Yandex, among others.
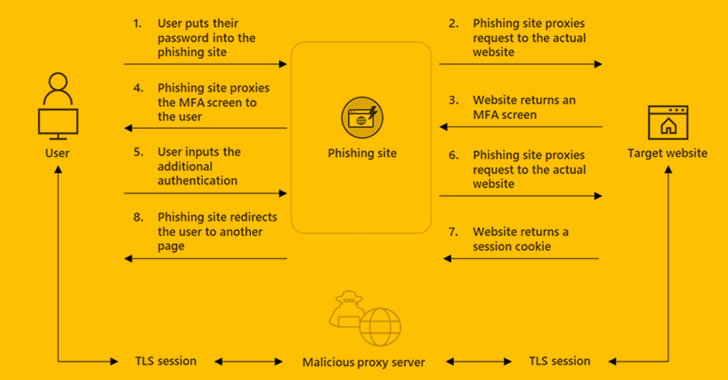
EvilProxy is similar to adversary-in-the-middle (AiTM[2]) attacks in that users
interact with a malicious proxy server that acts as a go-between
for the target website, covertly harvesting the credentials and 2FA
passcodes entered in the login pages.
It’s offered on a subscription basis per service for a time
period of 10, 20, or 31 days, with the kit available for $400 a
month and accessed over the TOR anonymity network after the payment
is arranged manually with an operator on Telegram. Attacks against
Google accounts, in contrast, cost up to $600 per month.
“After activation, the operator will be asked to provide SSH
credentials to further deploy a Docker container and a set of
scripts,” Resecurity said, adding the technique mirrors that of
another PhaaS service called Frappo[3]
that came to light earlier this year.
While the sale of EvilProxy to prospective customers is subject
to vetting by the actors, it goes without saying that the service
offers a “cost-effective and scalable solution” to carry out social
engineering attacks.
The development is further an indication that adversaries are
upgrading their attack arsenal to orchestrate sophisticated
phishing campaigns targeting users in a manner that can defeat
existing security safeguards.
To add to the concerns, the targeting of public-facing code and
package repositories such as GitHub, NPM, PyPI, and RubyGems
suggests that the operators are also aiming to facilitate supply
chain attacks via such operations.
Gaining unauthorized access to accounts and injecting malicious
code into widely used projects by trusted developers can be a
goldmine for threat actors, significantly widening the impact of
the campaigns.
“It’s highly likely the actors aim to target software developers
and IT engineers to gain access to their repositories with the end
goal to hack ‘downstream’ targets,” the researchers said.
Read more https://thehackernews.com/2022/09/new-evilproxy-phishing-service-allowing.html