High-profile companies and local governments located primarily
in Asia are the subjects of targeted attacks by a previously
undocumented espionage group dubbed Worok that has
been active since late 2020.
“Worok’s toolset includes a C++ loader CLRLoad, a PowerShell
backdoor PowHeartBeat, and a C# loader PNGLoad that uses
steganography to extract hidden malicious payloads from PNG files,”
ESET researcher Thibaut Passilly said[1]
in a new report published today.
Worok is said to share overlaps in tools and interests with
another adversarial collective tracked as TA428[2], with the group linked
to attacks against entities spanning energy, financial, maritime,
and telecom sectors in Asia as well as a government agency in the
Middle East and a private firm in southern Africa.
Malicious activities undertaken by the group experienced a
noticeable break from May 2021 to January 2022, before resuming the
next month. The Slovak cybersecurity firm assessed the group’s
goals to be aligned with information theft.
Initial foothold to target networks through 2021 and 2022
entailed the use of ProxyShell exploits[3]
in select instances, followed by deploying additional custom
backdoors for entrenched access. Other initial compromise routes
are unknown as yet.
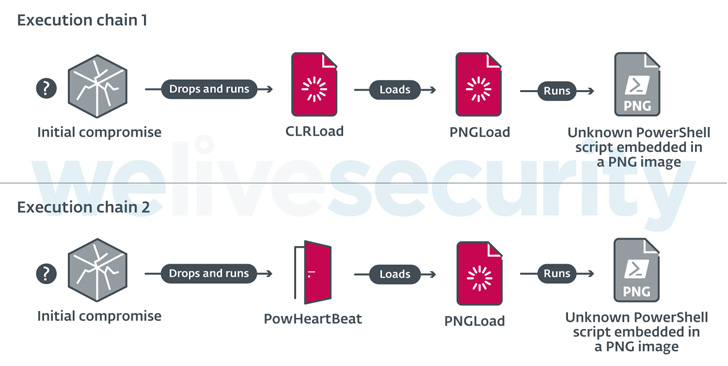
Among the tools in Worok’s malware arsenal is a first-stage
loader called CLRLoad, which is succeeded by a .NET-based
steganographic loader codenamed PNGLoad that’s capable of executing
an unknown PowerShell script embedded in a PNG image file.
Infection chains in 2022 have since dropped CLRLoad in favor of
a full-featured PowerShell implant referred to as PowHeartBeat
that’s subsequently used to launch PNGLoad, in addition to
communicating with a remote server via HTTP or ICMP[4]
to execute arbitrary commands, send and receive files, and carry
out related file operations.
ESET said it was unable to retrieve any of the final-stage PNG
payloads, although it’s suspected that the malware could be
concealed in valid, innocuous-looking PNG images and therefore
“hide in plain sight” without attracting attention.
“Worok is a cyber espionage group that develops its own tools,
as well as leveraging existing tools, to compromise its targets,”
Passilly said.
“Stealing information from their victims is what we believe the
operators are after because they focus on high-profile entities in
Asia and Africa, targeting various sectors, both private and
public, but with a specific emphasis on government entities.”
References
Read more https://thehackernews.com/2022/09/worok-hackers-target-high-profile-asian.html