A malicious campaign mounted by the North Korea-linked Lazarus Group[1]
is targeting energy providers around the world, including those
based in the United States, Canada, and Japan.
“The campaign is meant to infiltrate organizations around the
world for establishing long-term access and subsequently
exfiltrating data of interest to the adversary’s nation-state,”
Cisco Talos said[2]
in a report shared with The Hacker News.
Some elements of the espionage attacks have already entered
public domain, courtesy of prior reports from Broadcom-owned
Symantec[3]
and AhnLab[4]
earlier this April and May.
Symantec attributed the operation to a group referred to as
Stonefly, a Lazarus subgroup which is better known as Andariel,
Guardian of Peace, OperationTroy, and Silent Chollima.
While these attacks previously led to the instrumentation of
Preft (aka Dtrack) and NukeSped (aka Manuscrypt) implants, the
latest attack wave is notable for employing two other pieces of
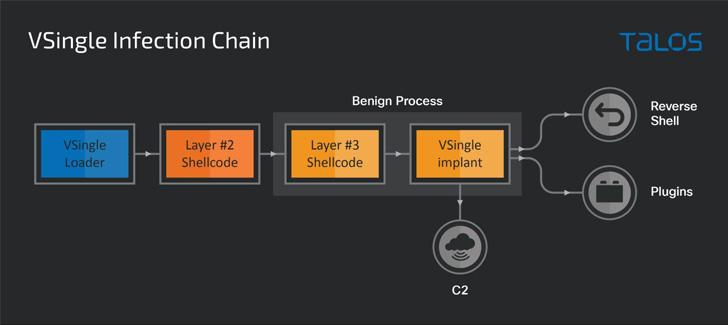
malware: VSingle[5], an HTTP bot which
executes arbitrary code from a remote network, and a Golang
backdoor called YamaBot[6].
Also put to use in the campaign is a new remote access trojan
called MagicRAT[7]
that comes with capabilities to evade detection and launch
additional payloads on the infected systems.
“Although the same tactics have been applied in both attacks,
the resulting malware implants deployed have been distinct from one
another, indicating the wide variety of implants available at the
disposal of Lazarus,” researchers Jung soo An, Asheer Malhotra, and
Vitor Ventura said.
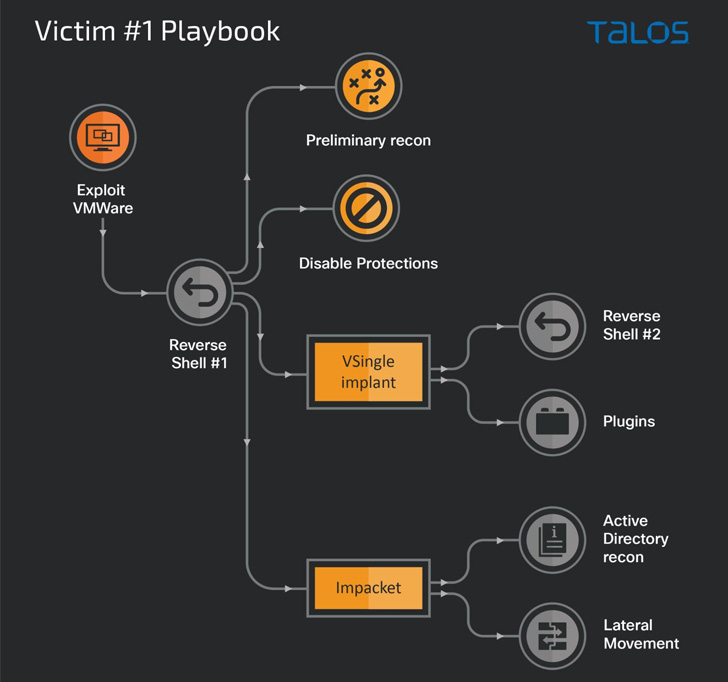
Initial access into enterprise networks is facilitated by means
of exploitation of vulnerabilities in VMware products (e.g.,
Log4Shell), with the ultimate goal of establishing persistent
access to perform activities in support of North Korean government
objectives.
The use of VSingle in one attack chain is said to have enabled
the threat actor to carry out a variety of activities such as
reconnaissance, exfiltration, and manual backdooring, giving the
operators a solid understanding of the victim environment.
Other tactics embraced by the group besides the use of bespoke
malware include credential harvesting via tools like Mimikatz and
Procdump, disabling antivirus components, and reconnaissance of the
Active Directory services, and even taking steps to cleanup their
traces after activating the backdoors on the endpoint.
References
Read more https://thehackernews.com/2022/09/north-korean-lazarus-hackers-targeting.html