The U.S. Treasury Department on Friday announced sanctions
against Iran’s Ministry of Intelligence and Security (MOIS) and its
Minister of Intelligence, Esmaeil Khatib, for engaging in
cyber-enabled activities against the nation and its allies.
“Since at least 2007, the MOIS and its cyber actor proxies have
conducted malicious cyber operations targeting a range of
government and private-sector organizations around the world and
across various critical infrastructure sectors,” the Treasury
said[1].
The agency also accused Iranian state-sponsored actors of
staging disruptive attacks[2] aimed at Albanian
government computer systems in mid-July 2022, forcing it to suspend
its online services.
The development comes months nearly nine months after the U.S.
Cyber Command characterized the advanced persistent threat (APT)
known as MuddyWater as a subordinate element[3]
within MOIS. It also comes almost two years following the
Treasury’s sanctions against another Iranian APT group dubbed
APT39[4]
(aka Chafer or Radio Serpens).
Friday’s sanctions effectively prohibit U.S. businesses and
citizens from engaging in transactions with MOIS and Khatib, and
non-U.S. citizens that engage in transactions with the designated
entities may themselves be exposed to sanctions.
Coinciding with the economic blockade, the Albanian government
said[5]
the cyberattack on the digital infrastructure was “orchestrated and
sponsored by the Islamic Republic of Iran through the engagement of
four groups that enacted the aggression.”
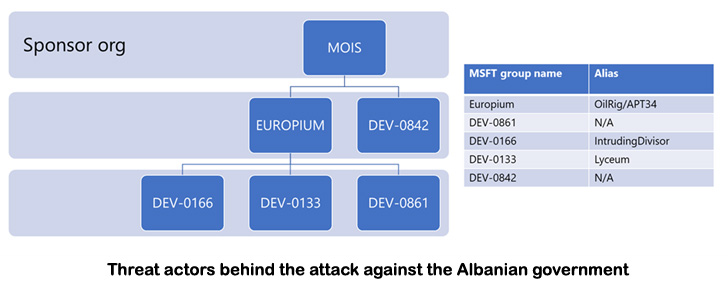
Microsoft, which investigated the attacks, said the adversaries
worked in tandem to carry out distinct phases of the attacks, with
each cluster responsible for a different aspect of the operation
–
- DEV-0842 deployed the ransomware and wiper malware
- DEV-0861 gained initial access and exfiltrated data
- DEV-0166 (aka IntrudingDivisor[6]) exfiltrated data,
and - DEV-0133 (aka Lyceum[7]
or Siamese Kitten) probed victim infrastructure
The tech giant’s threat intelligence teams also attributed the
groups involved in gaining initial access and exfiltrating data to
the Iranian MOIS-linked hacking collective codenamed Europium[8], which is also known as
APT34, Cobalt Gypsy, Helix Kitten, or OilRig.
“The attackers responsible for the intrusion and exfiltration of
data used tools previously used by other known Iranian attackers,”
it said[9]
in a technical deepdive. “The attackers responsible for the
intrusion and exfiltration of data targeted other sectors and
countries that are consistent with Iranian interests.”
“The Iranian sponsored attempt at destruction had less than a
10% total impact on the customer environment,” the company noted,
adding the post-exploitation actions involved the use of web shells
for persistence, unknown executables for reconnaissance, credential
harvesting techniques, and defense evasion methods to turn off
security products.
Microsoft’s findings dovetail with previous analysis[10] from Google’s Mandiant,
which called the politically motivated activity a “geographic
expansion of Iranian disruptive cyber operations.”
Initial access to the network of an Albanian government victim
is said to have occurred as early as May 2021 via successful
exploitation of a SharePoint remote code execution flaw (CVE-2019-0604[11]), followed by
exfiltration of email from the compromised network between October
2021 and January 2022.
A second, parallel wave of email harvesting was observed between
November 2021 and May 2022, likely through a tool called Jason[12]. On top of that, the
intrusions entailed the deployment of ransomware called ROADSWEEP,
eventually leading to the distribution of a wiper malware referred
to as ZeroCleare.
Microsoft characterized the destructive campaign as a “form of
direct and proportional retaliation” for a string of cyberattacks
on Iran, including one staged by an
Iranian hacktivist group[13] that’s affiliated to
Mujahedin-e-Khalq (MEK[14]) in the first week of
July 2022.
The MEK, also known as the People’s Mujahedin Organization of
Iran (PMOI), is an Iranian dissident group largely based in Albania
that seeks to overthrow the government of the Islamic Republic of
Iran and install its own government.
“Some of the Albanian organizations targeted in the destructive
attack were the equivalent organizations and government agencies in
Iran that experienced prior cyberattacks with MEK-related
messaging,” the Windows maker said.
Iran’s Foreign Ministry, however, has rejected
accusations[15] that the country was
behind the digital offensive on Albania, calling them “baseless”
and that it’s “part of responsible international efforts to deal
with the threat of cyberattacks.”
References
- ^
said
(home.treasury.gov) - ^
staging
disruptive attacks (www.kryeministria.al) - ^
subordinate element
(thehackernews.com) - ^
APT39
(thehackernews.com) - ^
said
(www.kryeministria.al) - ^
IntrudingDivisor
(unit42.paloaltonetworks.com) - ^
Lyceum
(thehackernews.com) - ^
Europium
(thehackernews.com) - ^
said
(www.microsoft.com) - ^
previous analysis
(thehackernews.com) - ^
CVE-2019-0604
(msrc.microsoft.com) - ^
Jason
(marcoramilli.com) - ^
staged
by an Iranian hacktivist group
(www.iranintl.com) - ^
MEK
(en.wikipedia.org) - ^
rejected accusations
(irangov.ir)
Read more https://thehackernews.com/2022/09/us-imposes-new-sanctions-on-iran-over.html