A hacktivist collective called GhostSec has
claimed credit for compromising as many as 55 Berghof programmable
logic controllers (PLCs[1]) used by Israeli
organizations as part of a “Free Palestine” campaign.
Industrial cybersecurity firm OTORIO, which dug deeper[2]
into the incident, said the breach was made possible owing to the
fact that the PLCs were accessible through the Internet and were
secured by trivially guessable credentials.
Details of the compromise first came to light on September 4
after GhostSec shared a video on its Telegram channel demonstrating
a successful login to the PLC’s admin panel, in addition to dumping
data from the hacked controllers.
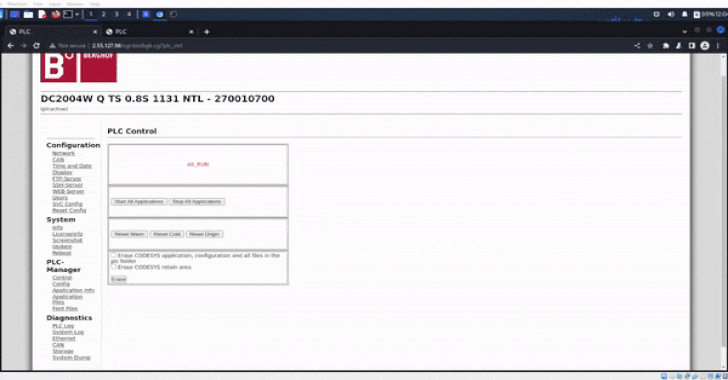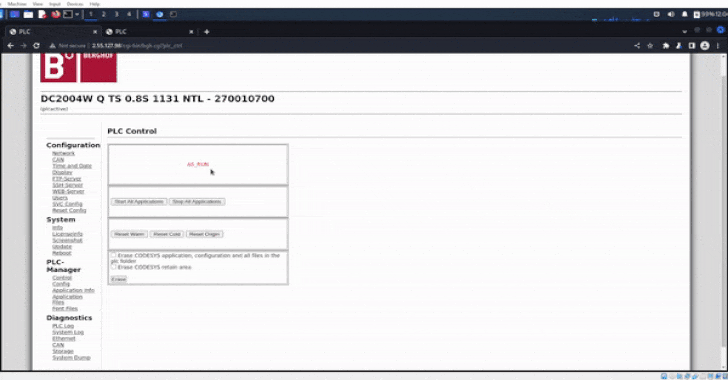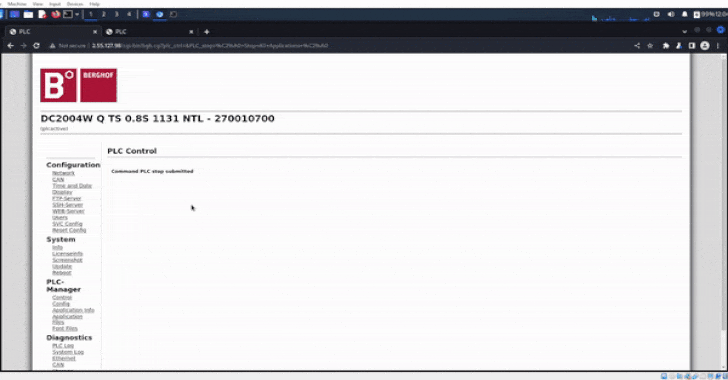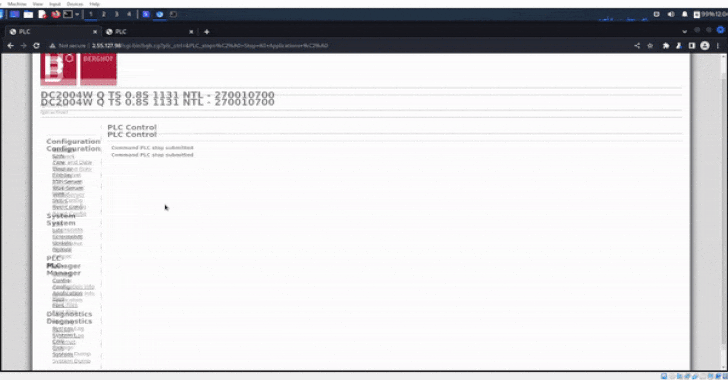
The Israeli company said the system dumps and screenshots were
exported directly from the admin panel following unauthorized
access to the controllers through their public IP addresses.
GhostSec (aka Ghost Security), first identified in 2015, is a
self-proclaimed vigilante group[3]
that was initially formed to target ISIS websites[4]
that preach Islamic extremism.
Earlier this February, the group rallied its support[5]
for Ukraine in the immediate aftermath of Russia’s military
invasion of the country. Since late June, it has also participated
in a campaign targeting Israeli organizations and enterprises.
“The group pivoted from their regular operations and started to
target multiple Israeli companies, presumably gaining access to
various IoT interfaces and ICS/SCADA systems, which led to possible
disruptions,” Cyberint noted[6]
on July 14.
The attacks against Israeli targets, dubbed “#OpIsrael,” is said
to have commenced on June 28, 2022, citing “continuous attacks from
Israel towards Palestinians.”
In the intervening period, GhostSec has carried out a number of
attacks, including those aimed at internet-exposed interfaces
belonging to Bezeq International and an ELNet power meter located
at the Scientific Industries Center (Matam).
The breach of Berghof PLCs, viewed in that light, is part of the
actor’s broader shift to strike the SCADA/ICS domain, although it
appears to be a case wherein the group took advantage of “easily
overlooked misconfigurations of industrial systems” to carry out
the attacks.
“Despite the low impact of this incident, this is a great
example where a cyber attack could have easily been avoided by
simple, proper configuration,” the researchers said.
“Disabling the public exposure of assets to the Internet, and
maintaining a good password policy, especially changing the default
login credentials, would cause the hacktivists’ breach attempt to
fail.”
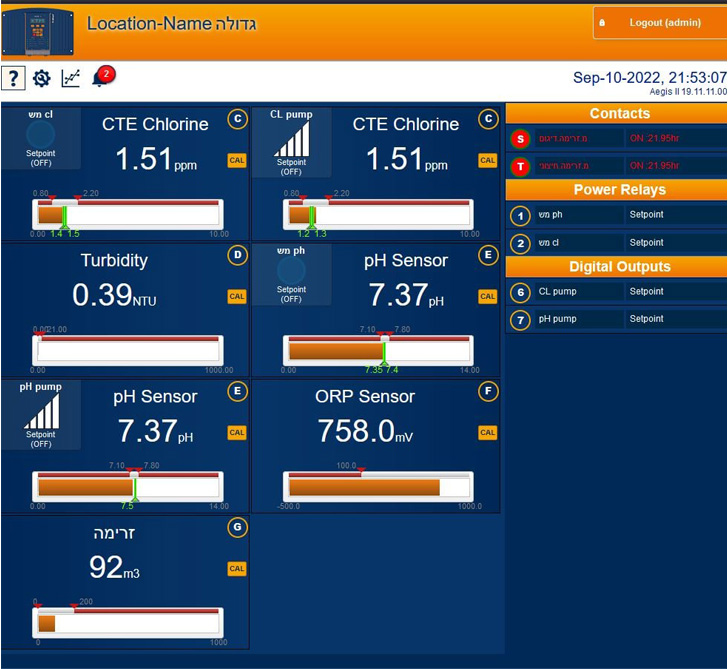
GhostSec, in the meanwhile, has continued to post more
screenshots, claiming to have gained access to another control
panel that can be used to alter chlorine and pH levels in the
water.
“Hope you all can understand our decision on not attacking their
pH levels and risking a chance to harm the innocents of #Israel,”
the group said in a tweet posted over the weekend. “Our ‘war’ has
always been FOR the people not against them. #FreePalestine”
References
- ^
PLCs
(thehackernews.com) - ^
dug
deeper (www.otorio.com) - ^
vigilante group
(outpost24.com) - ^
target
ISIS websites (thehackernews.com) - ^
rallied
its support (thehackernews.com) - ^
noted
(cyberint.com)
Read more https://thehackernews.com/2022/09/palestinian-hacktivist-group-ghostsec.html