Palo Alto Networks Unit 42 has detailed the inner workings of a
malware called OriginLogger, which has been touted
as a successor to the widely used information stealer and remote
access trojan (RAT) known as Agent Tesla[1].
A .NET based keylogger and remote access, Agent Tesla has had a
long-standing presence in the threat landscape, allowing malicious
actors to gain remote access to targeted systems and beacon
sensitive information to an actor-controlled domain.
Known to be used in the wild since 2014, it’s advertised for
sale on dark web forums and is generally distributed through
malicious spam emails as an attachment.
In February 2021, cybersecurity firm Sophos disclosed two new variants[2] of the commodity malware
(version 2 and 3) that featured capabilities to steal credentials
from web browsers, email apps, and VPN clients, as well as use
Telegram API for command-and-control.
Now according to Unit 42 researcher Jeff White, what has been
tagged as AgentTesla version 3 is actually OriginLogger[3], which is said to have
sprung up to fill the void left by the former after its operators
shut shop on March 4, 2019, following legal troubles.
The cybersecurity firm’s starting point for the investigation
was a YouTube video[4]
that was posted in November 2018 detailing its features, leading to
the discovery of a malware sample (“OriginLogger.exe[5]“) that was uploaded to
the VirusTotal malware database on May 17, 2022.
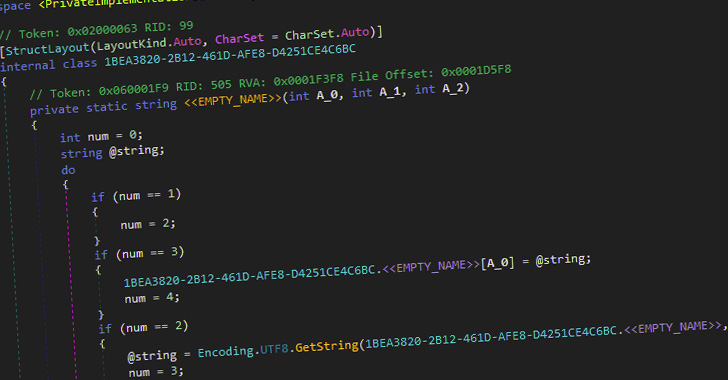
The executable is a builder binary that allows a purchased
customer to specify the kinds of data to be captured, including
clipboard, screenshots, and the list of applications and services
(e.g., browsers, email clients etc.) from which the credentials are
to be extracted.
User authentication is achieved by sending a request to an
OriginLogger server, which resolves to the domain names 0xfd3[.]com
and its newer counterpart originpro[.]me based on two builder
artifacts compiled on September 6, 2020, and June 29, 2022.
Unit 42 said it was able to identify a GitHub profile with the
username 0xfd3 that hosted two source code repositories for
stealing passwords from Google Chrome and Microsoft Outlook, both
of which are used in OrionLogger.
OrionLogger, like Agent Tesla, is delivered via a decoy Microsoft Word document[6] that, when opened, is
designed to display an image of a passport for a German citizen and
a credit card, along with a number of Excel Worksheets embedded
into it.
The worksheets, in turn, contain a VBA macro that uses MSHTA[7]
to invoke an HTML page hosted on a remote server, which, for its
part, includes an obfuscated JavaScript code to fetch two encoded
binaries hosted on Bitbucket.
The first of the two pieces of malware is a loader that utilizes
the technique of process hollowing[8]
to inject the second executable, the OrionLogger payload, into the
aspnet_compiler.exe process[9], a legitimate utility to
precompile ASP.NET applications.
“The malware uses tried and true methods and includes the
ability to keylog, steal credentials, take screenshots, download
additional payloads, upload your data in a myriad of ways and
attempt to avoid detection,” White said.
What’s more, an analysis of a corpus of over 1,900 samples shows
that the most common exfiltration mechanisms for sending the data
back to the attacker is via SMTP, FTP, web uploads to the
OrionLogger panel, and Telegram with the help of 181 unique
bots.
“Commercial keyloggers have historically catered to less
advanced attackers, but as illustrated in the initial lure document
analyzed here, this does not make attackers any less capable of
using multiple tools and services to obfuscate and make analysis
more complicated,” White further said.
References
- ^
Agent
Tesla (malpedia.caad.fkie.fraunhofer.de) - ^
disclosed two new variants
(thehackernews.com) - ^
OriginLogger
(unit42.paloaltonetworks.com) - ^
YouTube
video (www.youtube.com) - ^
OriginLogger.exe
(www.virustotal.com) - ^
decoy
Microsoft Word document
(www.virustotal.com) - ^
MSHTA
(attack.mitre.org) - ^
process
hollowing (attack.mitre.org) - ^
aspnet_compiler.exe process
(docs.microsoft.com)
Read more https://thehackernews.com/2022/09/researchers-detail-originlogger-rat.html