The threat actor behind the malware-as-a-service (MaaS) called
Eternity has been linked to new piece of malware called
LilithBot.
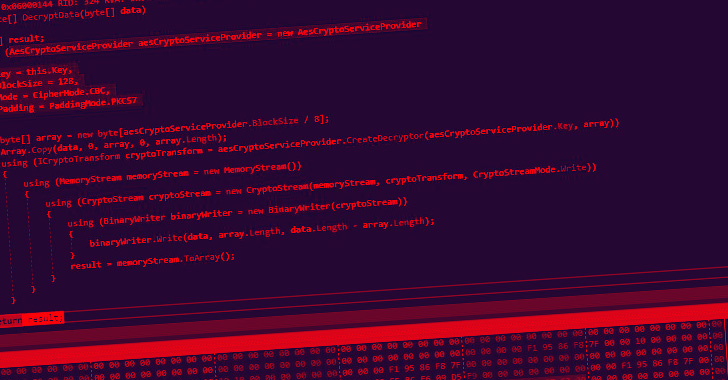
“It has advanced capabilities to be used as a miner, stealer,
and a clipper along with its persistence mechanisms,” Zscaler
ThreatLabz researchers Shatak Jain and Aditya Sharma said[1]
in a Wednesday report.
“The group has been continuously enhancing the malware, adding
improvements such as anti-debug and anti-VM checks.”
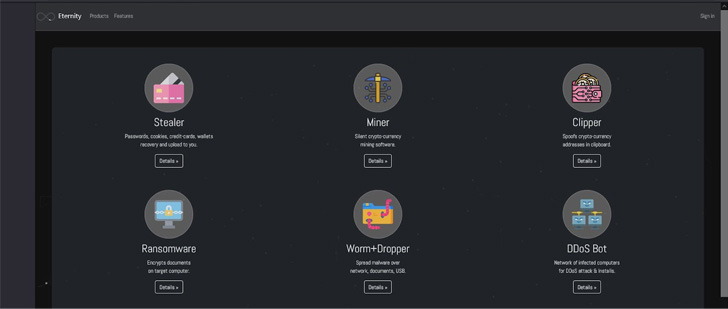
Eternity Project[2]
came on the scene earlier this year, advertising its warez and
product updates on a Telegram channel. The services provided
include a stealer, miner, clipper, ransomware, USB worm, and a DDoS
bot.
LilithBot is the latest addition to this list. Like its
counterparts, the multifunctional malware bot is sold on a
subscription basis to other cybercriminals in return for a
cryptocurrency payment.
Upon a successful compromise, the information gathered through
the bot – browser history, cookies, pictures, and screenshots – is
compressed into a ZIP archive (“report.zip”) and exfiltrated to a
remote server.
The development is a sign that the Eternity Project is actively
expanding its malware arsenal, not to mention adopting
sophisticated techniques to bypass detections.
References
- ^
said
(www.zscaler.com) - ^
Eternity
Project (thehackernews.com)
Read more https://thehackernews.com/2022/10/eternity-group-hackers-offering-new.html