Two point-of-sale (PoS) malware variants have been put to use by
a threat actor to steal information related to more than 167,000
credit cards from payment terminals.
According to Singapore-headquartered cybersecurity company
Group-IB, the stolen data dumps could net the operators as much as
$3.34 million by selling them on underground forums.
While a significant proportion of attacks aimed at gathering
payment data rely on JavaScript sniffers[1]
(aka web skimmers) stealthily inserted on e-commerce websites, PoS
malware continues to be an ongoing, if less popular, threat.
Just last month, Kaspersky detailed new tactics adopted by a
Brazilian threat actor known as Prilex[2]
to steal money by means of fraudulent transactions.
“Almost all POS malware strains have a similar card dump
extraction functionality, but different methods for maintaining
persistence on infected devices, data exfiltration and processing,”
researchers Nikolay Shelekhov and Said Khamchiev said[3].
Treasure Hunter and its advanced successor MajikPOS are alike in
that they are designed to brute-force their way into a PoS
terminal, or alternatively purchase initial access from other
parties known as initial access brokers, followed by extracting
payment card information from the system’s memory, and forwarding
it to a remote server.
It’s worth noting that MajikPOS first came to light[4]
in early 2017, mainly affecting businesses across the U.S. and
Canada. Treasure Hunter[5]
(aka TREASUREHUNT[6]), on the other hand, has
been chronicled since 2014, with its source code suffering a leak
in 2018.
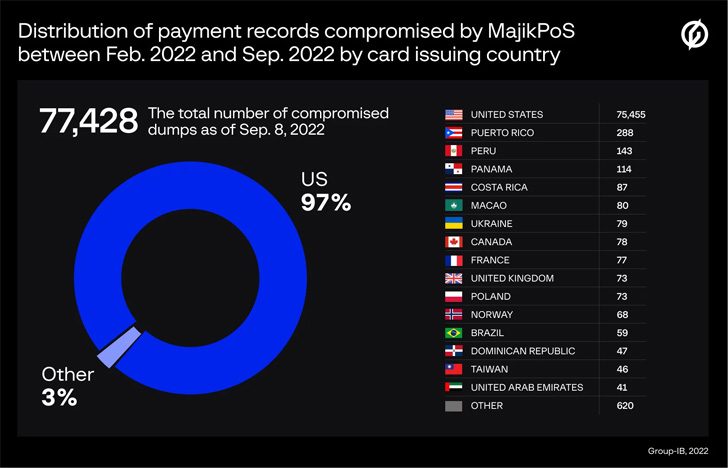
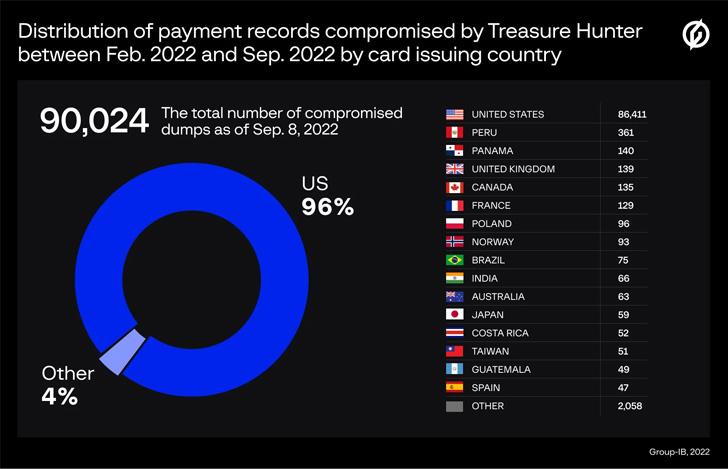
Group-IB, which identified the command-and-control (C2) servers,
associated with the two PoS malware, said 77,428 and 90,024 unique
payment records were compromised by MajikPOS and Treasure Hunter
between February and September 2022.
Most of the stolen cards are said to have been issued by banks
in the U.S., Puerto Rico, Peru, Panama, the U.K., Canada, France,
Poland, Norway, and Costa Rica.
The identity of the criminal actors behind the scheme is
unknown, and it’s currently not clear if the pilfered data has
already been sold for monetary gains by the group.
This can have severe consequences should the card-issuing banks
not enforce adequate protection mechanisms, effectively enabling
bad actors to employ cloned cards to illicitly withdraw funds and
make unauthorized transactions.
“PoS malware has become less attractive for threat actors in
recent years due to some of its limitations and the security
measures implemented within the card payment industry,” the
researchers said.
“Nevertheless, […] it remains a significant threat to the
payment industry as a whole and to separate businesses that have
not yet implemented the latest security practices. It is too early
to write off PoS malware.”
References
- ^
JavaScript sniffers
(thehackernews.com) - ^
Prilex
(thehackernews.com) - ^
said
(blog.group-ib.com) - ^
first
came to light (www.trendmicro.com) - ^
Treasure
Hunter (malpedia.caad.fkie.fraunhofer.de) - ^
TREASUREHUNT
(web.archive.org)
Read more https://thehackernews.com/2022/10/cybercriminals-used-two-pos-malware-to.html